Source: www.bleepingcomputer.com – Author: Bill Toulas Jimbos Protocol, an Arbitrum-based DeFi project, has suffered a flash loan attack that resulted in the loss of more than...
Day: May 29, 2023
MCNA Dental data breach impacts 8.9 million people after ransomware attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Managed Care of North America (MCNA) Dental has published a data breach notification on its website, informing almost 9 million...
Lazarus hackers target Windows IIS web servers for initial access – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The notorious North Korean state-backed hackers, known as the Lazarus Group, are now targeting vulnerable Windows Internet Information Services (IIS)...
How to Secure Your SCM Repositories with GitGuardian Honeytokens – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guest Expert Sponsorships Available Keshav Malik Keshav is a full-time Security Engineer who loves to build and break stuff. He is constantly...
From Data Chaos to Data Mastery How to Build and Scale Data Lakes with AWS Services – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dariel Marlow In today’s data-driven world, organizations are faced with an ever-increasing volume of data from various sources. To extract meaningful insights...
Protecting your business: Advice to SMB CEOs from a former CIO – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog The acronym CIO is sometimes understood to stand for “Career Is Over,” and here’s why: Business leaders in charge of...
The Top Threats to Cloud Infrastructure Security and How to Address Them – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dariel Marlow What is infrastructure security in Cloud Computing? Infrastructure security refers to the protection of physical and virtual components that make...
United States of America: Memorial Day 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Essential security practices in OT control systems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Prayukth K V Operational Technology (OT) security controls include the measures, workflows and procedures put in place to protect various OT systems...
Meta’s $1.3 Billion Fine, AI Hoax Hysteria, Montana’s TikTok Ban – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Eston In this episode, we discuss Meta’s record-breaking $1.3 billion fine by the EU for unlawfully transferring user data, shedding light...
LogRhythm Receives Best SIEM – Computer Software at the SBR Technology Excellence Awards 2023 for its Ability to Eliminate Noise Effectively – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nicholas Tan SINGAPORE – 29 May 2022 – LogRhythm, a leading cybersecurity company, has been recognised with the SIEM – Computer Software...
Are We Seeing Fewer Ransomware Attacks? Not Now – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Despite what you may have heard, ransomware threats continue to grow and evolve in mid-2023. Here’s what you need...
Invoice and CEO Scams Dominate Fraud Impacting Businesses – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Card Not Present Fraud , Finance & Banking , Fraud Management & Cybercrime UK Financial Services Firms Record $1.5 Billion in...
Top Privacy Considerations for Website Tracking Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Incident & Breach Response , Privacy Lokker CEO Ian Cohen on Growing Health Information Concerns With...
Sports Warehouse Fined $300,000 Over Payment Card Data Theft – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Audit , Card Not Present Fraud , Cybercrime Data Breach Exposed Nearly 20 Years of ‘Indefinitely’ Stored Payment Card Data Mathew...
Protect your business network with PureDome – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at PureDome. Thanks to the great team there for...
Top Cyberattacks Revealed in New Threat Intelligence Report – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 We recognize that in today’s world, security leaders must expand their focus beyond technologies and their vulnerabilities. To effectively manage risk,...
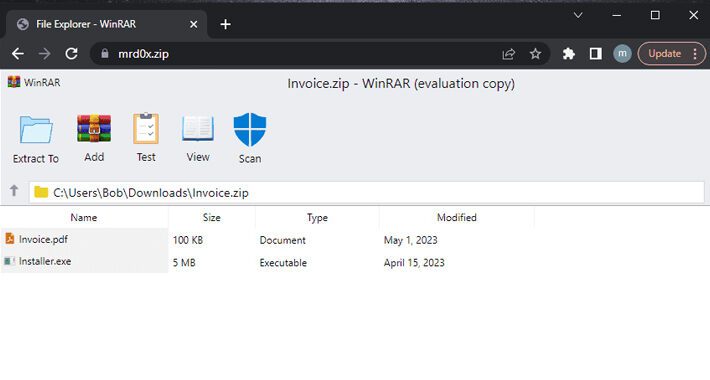
New Phishing Kit: File Archivers in the Browser – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac A new phishing kit, “File Archivers in the Browser” abuses ZIP domains. The kit displays bogus WinRAR or Windows File...
New Mirai Variant Campaigns are Targeting IoT Devices – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Unit 42, Palo Alto Networks threat research team, has found new malicious activity targeting IoT devices, using a variant of Mirai,...
Hackers hold city of Augusta hostage in a ransomware attack – Source: www.csoonline.com
Source: www.csoonline.com – Author: The ransomware group has released 10GB of sample data from the cyberattack on the US city of Augusta and claimed they have...
New phishing technique poses as a browser-based file archiver – Source: www.csoonline.com
Source: www.csoonline.com – Author: The new technique has a hacker simulate an archiving software in the web browser to trick the victim as he tries to...
Insider risk management: Where your program resides shapes its focus – Source: www.csoonline.com
Source: www.csoonline.com – Author: Choosing which department should be responsible for protecting an organization from threats from within isn’t always straightforward. There’s no getting around it,...
AceCryptor: Cybercriminals’ Powerful Weapon, Detected in 240K+ Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . May 29, 2023Ravie LakshmananCyber Threat / Malware A crypter (alternatively spelled cryptor) malware dubbed AceCryptor has been used to pack numerous...
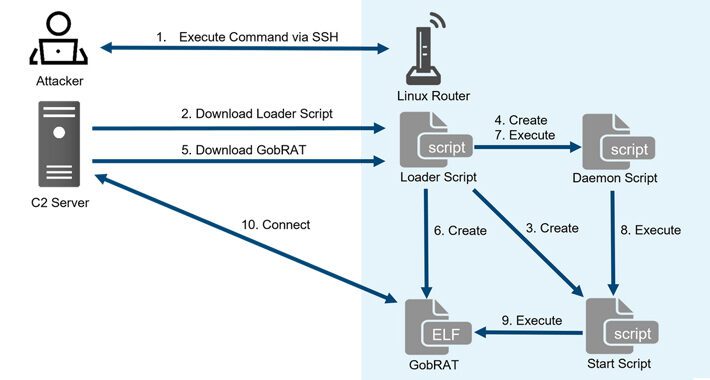
New GobRAT Remote Access Trojan Targeting Linux Routers in Japan – Source:thehackernews.com
Source: thehackernews.com – Author: . May 29, 2023Ravie LakshmananLinux / Network Security Linux routers in Japan are the target of a new Golang remote access trojan...
Don’t Click That ZIP File! Phishers Weaponizing .ZIP Domains to Trick Victims – Source:thehackernews.com
Source: thehackernews.com – Author: . A new phishing technique called “file archiver in the browser” can be leveraged to “emulate” a file archiver software in a...
PyPI Implements Mandatory Two-Factor Authentication for Project Owners – Source:thehackernews.com
Source: thehackernews.com – Author: . May 29, 2023Ravie LakshmananSupply Chain / Programming The Python Package Index (PyPI) announced last week that every account that maintains a...
Bad Magic’s Extended Reign in Cyber Espionage Goes Back Over a Decade – Source:thehackernews.com
Source: thehackernews.com – Author: . May 22, 2023Ravie LakshmananCyber Espionage / Malware New findings about a hacker group linked to cyber attacks targeting companies in the...
Are Your APIs Leaking Sensitive Data? – Source:thehackernews.com
Source: thehackernews.com – Author: . It’s no secret that data leaks have become a major concern for both citizens and institutions across the globe. They can...
U.K. Fraudster Behind iSpoof Scam Receives 13-Year Jail Term for Cyber Crimes – Source:thehackernews.com
Source: thehackernews.com – Author: . May 22, 2023Ravie LakshmananCyber Crime / Hacking A U.K. national responsible for his role as the administrator of the now-defunct iSpoof...
KeePass Exploit Allows Attackers to Recover Master Passwords from Memory – Source:thehackernews.com
Source: thehackernews.com – Author: . May 22, 2023Ravie LakshmananPassword Security / Exploit A proof-of-concept (PoC) has been made available for a security flaw impacting the KeePass...