Source: www.darkreading.com – Author: Curtis Franklin, Senior Analyst, Omdia Cybersecurity awareness training has always, at one level, been about risk. Whether you subscribe to the notion...
Day: May 24, 2023
Microsoft: BEC Attackers Evade ‘Impossible Travel’ Flags With Residential IP Addresses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Attackers have found a new way to avoid detection in business email compromise (BEC) and account takeover attacks by...
Bridgestone CISO: Lessons From Ransomware Attack Include Acting, Not Thinking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading As a CISO that helped his company navigate through the aftermath of a crippling ransomware attack...
US Sanctions N. Korean Entities for Sending Funds to Regime – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime One Worker Also Sanctioned for Transferring IT Earnings to North...
EU Committee Probes TikTok, UK’s Updated GDPR – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 General Data Protection Regulation (GDPR) , Governance & Risk Management , Privacy LIBE Committee Hears From Heads of UK and Irish...
Panel | The Four Steps to Build a Modern Data Protection Platform – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Salah Nassar Sr. Director Product Marketing, Zscaler Salah is a passionate and customer-centric marketer with a diverse background in networking and...
Sharp Decline in Crypto Hacks in Q1 2023 Unlikely to Last – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Finance & Banking , Fraud Management & Cybercrime Law Enforcement, Regulatory Action in US Likely Led to 70%...
North Korea’s BlueNoroff Group Targets macOS Systems – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cryptocurrency Fraud , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime BlueNoroff Changed Attack Tactics in 2023 After Its TTPs...
Suzuki motorcycle plant shut down by cyber attack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley The Indian manufacturing plant responsible for manufacturing Suzuki motorcycles has been forced to shut down following a cyber attack. Since...
The previously undocumented GoldenJackal APT targets Middle East, South Asia entities – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A previously undocumented APT group tracked as GoldenJackal has been targeting government and diplomatic entities in the Middle East and...
Google announced its Mobile VRP (vulnerability rewards program) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google introduced Mobile VRP (vulnerability rewards program), a new bug bounty program for reporting vulnerabilities in its mobile applications. Google...
German arms manufacturer Rheinmetall suffered Black Basta ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The German automotive and arms manufacturer Rheinmetall announced it was victim of a Black Basta ransomware attack that took place last month. Rheinmetall...
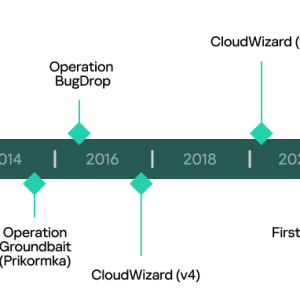
A deeper insight into the CloudWizard APT’s activity revealed a long-running activity – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of a threat actor, tracked as CloudWizard APT, that is targeting organizations involved in the region of the Russo-Ukrainian...
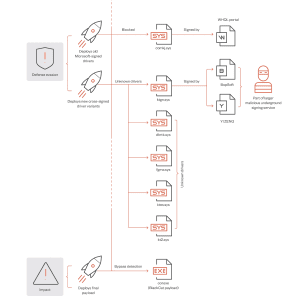
BlackCat Ransomware affiliate uses signed kernel driver to evade detection – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts spotted the ALPHV/BlackCat ransomware group using signed malicious Windows kernel drivers to evade detection. Trend Micro researchers shared details...
Axiado releases new security processors for servers and network appliances – Source: www.csoonline.com
Source: www.csoonline.com – Author: The new TCUs released by Axiado are built within a single SoC, with AI as added layer of security. Getty Images Security...
Teleport releases Teleport 13 with automatic vulnerability patching, enhanced DevOps security – Source: www.csoonline.com
Source: www.csoonline.com – Author: Teleport 13 features include Transport Layer Security routing and the ability to import applications/groups from Okta and AWS OpenSearch support for secure...
Think security first when switching from traditional Active Directory to Azure AD – Source: www.csoonline.com
Source: www.csoonline.com – Author: With the final release of Windows 10, the use of traditional Active Directory may be waning, and Azure AD on the rise....