Source: www.securityweek.com – Author: Associated Press A former executive fired from TikTok’s parent company ByteDance made a raft of accusations against the tech giant Friday, including...
Day: May 13, 2023
Discord suffered a data after third-party support agent was hacked – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Discord disclosed a data breach, the security breach was caused by the compromise of a third-party support agent’s account. Discord,...
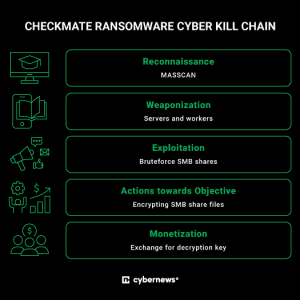
Russia-affiliated CheckMate ransomware quietly targets popular file-sharing protocol – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The CheckMate ransomware operators have been targeting the Server Message Block (SMB) communication protocol used for file sharing to compromise...
USENIX Enigma 2023 – Josiah Dykstra – ‘The Slippery Slope Of Cybersecurity Analogies’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/usenix-enigma-2023-josiah-dykstra-the-slippery-slope-of-cybersecurity-analogies/ Category & Tags: Security Bloggers Network,appsec education,cybersecurity...
Congrats on your SOC 2 Report! Here’s What to Do Next – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mimi Pham After tons of hard work, your company has successfully completed a SOC 2 audit and received a well-deserved SOC 2...
SafeBreach Coverage for US-CERT Alert (AA23-131A) – Exploit CVE-2023-27350 in PaperCut MF and NG – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On May 11th, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal...
Cybersecurity Insights with Contrast CISO David Lindner | 5/12 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 “Privacy is becoming a problem for many organizations. In a 2023 report by IAPP, 80%...
Uintah Basin Healthcare Data Breach Affects Over 100,000 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Healthcare , Industry Specific Hacking Incident Affects Patients Who Received Care Over a 10 Year Period Prajeet Nair...
Enigmatic Hacking Group Operating in Ukraine – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Attackers Target both Ukraine and pro-Russian Actors Anviksha More (AnvikshaMore) • May...
Uintah Basin Healthcare Data Breach Affects Over 100,000 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Healthcare , Industry Specific Hacking Incident Affects Patients Who Received Care Over a 10 Year Period Prajeet Nair...
Friday Squid Blogging: Giant Squid Video – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments MarkH • May 13, 2023 12:45 AM While reading a news story, my attention was caught by these...
Ted Chiang on the Risks of AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Ted Chiang has an excellent essay in the New Yorker: “Will A.I. Become the New McKinsey?” The question we should...
Multiple Ransomware Groups Adapt Babuk Code to Target ESXi VMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Over the past year, 10 different ransomware families have utilized leaked Babuk source code to develop...
Security Leaders Discuss Industry Trends at Dark Reading’s News Desk at RSAC 2023 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading RSA CONFERENCE 2023 — San Francisco — Cybersecurity leaders dug into a broad array of topics during their...
RapperBot Crew Drops DDoS/CryptoJacking Botnet Collab – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The RapperBot campaign is bringing in some fresh talent to its arsenal of malware beats,...
Leak of Intel Boot Guard Keys Could Have Security Repercussions for Years – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading The potential leak from MSI Gaming of signing keys for an important security feature in Intel-based firmware...
Enigmatic Hacking Group Operating in Ukraine – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Attackers Target both Ukraine and pro-Russian Actors Anviksha More (AnvikshaMore) • May...
Webinar | Using Machine Learning and Hyperscaled Cloud to Deliver Zero Trust – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Jason Georgi Global Field CTO, Prisma SASE, Palo Alto Networks Jason is the Global Field Chief Technology Officer for Prisma SASE...
Killer Use Cases for AI Dominate RSA Conference Discussions – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Attack Surface Management , Cybercrime Use Cases: Cybersecurity Offense, Defense and Safeguarding AI Itself, Experts...
Elementary Data Breach Questions Remain, My Dear Capita – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Beyond $25M in Estimated Cleanup Costs, The Game Remains Afoot...
Why Datadog and Rubrik Are In Talks to Buy Laminar for $200M – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Governance & Risk Management , Security Operations Laminar Has Landed Multiple M&A Suitors Just 18 Months After Emerging...
HIPAA Considerations for AI Tool Use in Healthcare Research – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 The potential use cases for generative AI technology in healthcare appear limitless, but they’re weighted with an array of potential privacy,...
Why Health Entities Need to Implement NIST Cyber Framework – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 NIST Standards , Standards, Regulations & Compliance Bob Bastani of HHS ASPR Describes Perks of a Strategic Approach to Managing Risk...
HHS OCR Leader: Agency Is Cracking Down on Website Trackers – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , HIPAA/HITECH , Privacy Director Melanie Fontes Rainer on Top HIPAA Rule-Making, Enforcement Priorities Marianne Kolbasuk McGee...
Closing Privacy ‘Loopholes’ in Reproductive Healthcare Data – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 A recently proposed federal rule would prohibit healthcare organizations from disclosing to law enforcement patient information related to obtaining or providing...
Live Masterclass | A Master Class on IT Security: Roger Grimes Teaches Ransomware Mitigation – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Anti-Phishing, DMARC , Business Email Compromise (BEC) , Fraud Management & Cybercrime Presented by KnowBe4 60 minutes ...
Building True Cyber Resilience in 2023 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Leadership & Executive Communication , Training & Security Leadership , Video CISO Amit Basu Shares Practical Steps to Test Cyber Resilience...
Live Webinar | Breaking Down Security Challenges so Your Day Doesn’t Start at 3pm – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Dana Torgersen Sr. Director, Security Product Marketing, Sumo Logic Dana leads product marketing for Sumo Logic security solutions. He is a...
Live Webinar | Go From Hate to Great with Next Generation PSA – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
NIST SP 800-39: Managing Information Security Risk – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 From heightened risks to increased regulations, senior leaders at all levels are pressured to improve their organizations’ risk management capabilities. But...