Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/usenix-enigma-2023-adrian-sanabria-myths-and-lies-in-infosec/ Category & Tags: Security Bloggers Network,appsec education,cybersecurity...
Day: May 12, 2023
How to Spot and Stop Active Directory Attacks Faster – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Zhang Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/how-to-spot-and-stop-active-directory-attacks-faster/ Category & Tags: Security Bloggers Network,Threat Detection...
Neutralize Identity Attacks, Stop SaaS Breaches – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog See and Secure the SaaS-Identity Attack Surface When a data breach occurs at a critical SaaS provider and gains...
Randall Munroe’s XKCD ‘Taxiing’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Technical Analysis of CryptNet Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Santiago Vicente Key Points CryptNet is a new ransomware-as-a-service that has been advertised in underground forums since at least April 2023 The...
USENIX Enigma 2023 – Moderator: Melanie Ensign, Panelists: Joseph Menn, Lily Hay Newman, Alfred Ng – ‘Panel: True Crime Journalism: Cyber’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Enigma 2023 – Moderator: Melanie Ensign, Panelists: Joseph Menn, Lily...
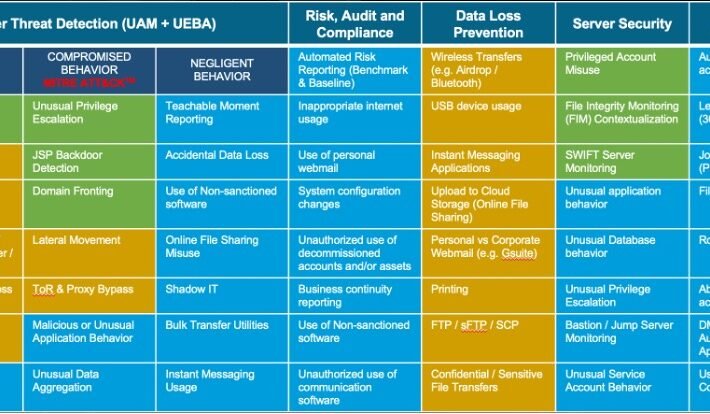
DTEX Insider Risk Assessment Development Strategy for Partners – Source: securityboulevard.com
Source: securityboulevard.com – Author: Brian Stoner Insider risk is the fastest growing area of cybersecurity today. Like the identity and access management projects of several years...
Ted Chiang on the Risks of AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Ted Chiang has an excellent essay in the New Yorker: “Will A.I. Become the New McKinsey?” The question we should...
How to Handle Secrets in Terraform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guest Expert Sponsorships Available Keshav Malik Keshav is a full-time Security Engineer who loves to build and break stuff. He is constantly...
WordPress Plugin Used in 1M+ Websites Patched to Close Critical Bug – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading WordPress plugins allow organizations to quickly extend the functionality of their websites without requiring any coding...
An Analyst View of XM Cyber’s Acquisition of Confluera – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jonathan Care, Contributing Writer, Dark Reading Industry analyst reaction was mixed after XM Cyber, a cyber threat intelligence and breach and attack...
Making Sure Lost Data Stays Lost – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer The stories are both infamous and legendary. Surplus computing equipment purchased at auction contains thousands of files with...
Malicious Chatbots Target Casinos in Southeast Asia – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A campaign dating back to October 2021 has turned its attention toward Southeast Asian gambling operations with...
New Competition Focuses on Hardening Cryptosystems – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Technology Innovation Institute (TII), a global scientific research center and the applied research pillar of Abu...
How Cybercriminals Adapted to Microsoft Blocking Macros by Default – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Ever since Microsoft decided to block Office macros by default, threat actors have been forced to...
‘Very Noisy:’ For the Black Hat NOC, It’s All Malicious Traffic All the Time – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading BLACK HAT ASIA – Singapore – When you’re in an environment where the overwhelming majority...
AI Is About to Be Everywhere: Where Will Regulators Be? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Steve Weber, Professor of the Graduate School, UC Berkeley School of Information Generative artificial intelligence (AI) is developing at breakneck speed. After...
Dragos Employee Hacked, Revealing Ransomware, Extortion Scheme – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading One might argue that security companies should be more prepared than most organizations to defend against a...
Building True Cyber Resilience in 2023 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Leadership & Executive Communication , Training & Security Leadership , Video CISO Amit Basu Shares Practical Steps to Test Cyber Resilience...
Closing Privacy ‘Loopholes’ in Reproductive Healthcare Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 A recently proposed federal rule would prohibit healthcare organizations from disclosing to law enforcement patient information related to obtaining or providing...
Toyota Exposed Auto Location of 2M Japanese Customers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Incident & Breach Response , Security Operations Undetected Cloud Misconfiguration Exposed Vehicle Information for Over Ten Years Jayant...
Live Webinar | Go From Hate to Great with Next Generation PSA – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Editors’ Panel: How Feds Hacked Russia’s ‘Snake’ Operation – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Also: APAC Privacy Law Trends; Another Company...
Safeguarding Cyberspace: Unleashing Mainframe’s Fortified Digital Trust through Advanced Authentication – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Broadcom’s Mary Ann Furno on Authentication Changes, How Orgs Adapt to Challenges May 12, 2023 Mary Ann Furno, senior...
Toyota: Data on More Than 2 Million Vehicles in Japan Were at Risk in Decade-Long Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A decade-long data breach in Toyota’s much-touted online service put some information on more than 2 million vehicles at risk,...
WordPress Plugin Vulnerability Exposed Ferrari Website to Hackers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A vulnerability discovered in the official website of luxury sports car maker Ferrari could have exposed potentially sensitive information, according...
Spain Arrests Hackers in Crackdown on Major Criminal Organization – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Spanish authorities this week announced the arrest of 40 individuals for their roles in a criminal organization that performed bank...
Leaked Babuk Code Fuels New Wave of VMware ESXi Ransomware – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybersecurity firm SentinelOne warns of an increase in the number of new ransomware families designed to target VMware ESXi that...
Organizations Informed of Over a Dozen Vulnerabilities in Rockwell Automation Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Rockwell Automation customers have been informed this week about potentially serious vulnerabilities found and patched in several products. The timing...
CISA, FBI: Ransomware Gang Exploited PaperCut Flaw Against Education Facilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have raised the alarm on a...