Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading Distributed denial-of-service (DDoS) is the attack method businesses are most concerned about, believing it will have...
Month: April 2023
Windows 11 KB5025305 adds prioritized Windows updates setting – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has released the optional April 2023 non-security cumulative updates for all editions of Windows 11 22H2 with a new...
New SLP bug can lead to massive 2,200x DDoS amplification attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new reflective Denial-of-Service (DoS) amplification vulnerability in the Service Location Protocol (SLP) allows threat actors to launch massive denial-of-service...
Google Authenticator now backs up your 2FA codes to the cloud – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Google Authenticator app has received a critical update for Android and iOS that allows users to back up their...
TP-Link Archer WiFi router flaw exploited by Mirai malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Mirai malware botnet is actively exploiting a TP-Link Archer A21 (AX1800) WiFi router vulnerability tracked as CVE-2023-1389 to incorporate...
Mobile device security policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: PURPOSE This Mobile Device Security Policy from TechRepublic Premium provides guidelines for mobile device security needs in order to protect businesses and...
Pro-Russia hackers attack European air traffic control website, but don’t panic! Flights continue as normal – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Eurocontrol, the European air traffic control agency, has revealed that it has been under cyber attack for the last week,...
Yellow Pages Canada Suffered a Cyberattack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Yellow Pages Group, a Canadian entity that specializes in directory publishing, has officially confirmed that it has fallen victim to...
PaperCut Flaw Exploited to Hijack Servers, Fix Released – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Attackers are taking advantage of critical flaws in the widely used PaperCut MF/NG print management software to install Atera remote...
What Is Identity and Access Management (IAM)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andra Andrioaie Identity and access management is a key component in ensuring the security of data. It can be used to protect...
What Is Privileged Account and Session Management (PASM)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Vladimir Unterfingher Privileged Account and Session Management (PASM) is a new PAM (Privileged Access Management) that focuses on privileged account monitoring and...
SLP flaw allows DDoS attacks with an amplification factor as high as 2200 times – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A flaw in the Service Location Protocol (SLP), tracked as CVE-2023-29552, can allow to carry out powerful DDoS attacks. A...
VMware addressed two zero-day flaws demonstrated at Pwn2Own Vancouver 2023 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini VMware addressed zero-day flaws that can be chained to achieve arbitrary code execution on Workstation and Fusion software hypervisors. VMware...
A new Mirai botnet variant targets TP-Link Archer A21 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Mirai botnet started exploiting the CVE-2023-1389 vulnerability (aka ZDI-CAN-19557/ZDI-23-451) in TP-Link Archer A21 in recent attacks. Last week, the Zero...
Google researchers found multiple security issues in Intel TDX – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google Cloud Security and Project Zero researchers, working with Intel experts, discovered multiple vulnerabilities in the Intel Trust Domain Extensions...
Browser Makers and EU Face Off Over QWACs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Security Operations , Standards, Regulations & Compliance EU Set to Approve Revised ID Framework to Digitize...
US Deputy AG: Aiding Victims Takes Precedence Over Arrests – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Cybercrime , Fraud Management & Cybercrime Lisa Monaco Says Justice Department Values Stopping Cybercrime Over Court Victories Michael Novinson (MichaelNovinson) •...
Webinar | Putting Privileged Access Management, Just-in-Time Access, and Identity Security Together – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
ISMG Editors: Opening Day Overview of RSA Conference 2023 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Events , RSA Conference , Video Emerging AI Tech, Identity Concerns and Latest Threats Are Among the Hot Topics Anna Delaney...
US Indicts Chinese National for Laundering DPRK Crypto – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Cryptocurrency Fraud , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime OFAC Adds Men to List of Specially Designated Nationals...
Most Common Connected Devices That Pose Risk to Hospitals – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1. Endpoint Security , Healthcare , Industry Specific Study: Unpatched Nurse Call Systems, Printers and IP Cameras Top the List Marianne Kolbasuk...
Cyberweapons Manufacturer QuaDream Shuts Down
Following a report on its activities, the Israeli spyware company QuaDream has shut down. This was QuadDream: Key Findings Based on an analysis of samples shared...
Cyber security technology integration, intrapreneurship & beyond
In this edited interview excerpt from The Women in Technology Podcast, Check Point Global Cyber Security Warrior and Evangelist Micki Boland speaks with Becky Schneider about...
RSAC Fireside Chat: Turning full attention to locking down the security of ‘open source’
By Byron V. Acohido Software composition analysis — SCA – is a layer of the security stack that, more so than ever, plays a prominent role...
The ESG Manager role & the importance of Environmental, Social & Governance strategy
In this exclusive CyberTalk.org interview, Idan Eden, the ESG Manager for Check Point, shares her expertise on the rapidly growing importance of ESG in corporate decision-making....
#RSAC: US DoJ Prioritizes Victim Support in Cybercrime Crackdown
The US Department of Justice’s (DoJ) approach to disrupting and preventing cybercrime was laid bare by Lisa Monaco, Deputy Attorney General of the United States, during...
Google Authenticator App now supports Google Account synchronization – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Google announced that its Authenticator app for Android and iOS now supports Google Account synchronization. Google announced that its Google...
Peugeot leaks access to user information in South America – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Peugeot, a French brand of automobiles owned by Stellantis, exposed its users in Peru, a South American country with a...
North Korea-linked BlueNoroff APT is behind the new RustBucket Mac Malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. North Korea-linked APT group BlueNoroff (aka Lazarus) was spotted targeting Mac users with new RustBucket malware. Researchers from security firm...
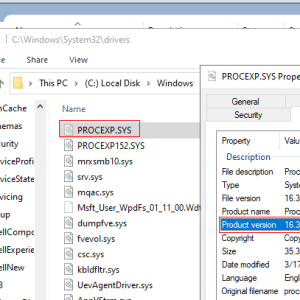
AuKill tool uses BYOVD attack to disable EDR software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini. Ransomware operators use the AuKill tool to disable EDR software through Bring Your Own Vulnerable Driver (BYOVD) attack. Sophos researchers...