Source: securityboulevard.com – Author: John P. Gormally, SR Risk is an enabler of Analysis Paralysis. Organizations invest vast amounts of money, time, and human capital in...
Day: April 27, 2023
USENIX Enigma 2023 – Lana Ramjit, Cornell Tech – ‘Technology Abuse Clinics For Survivors Of Intimate Partner Violence’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No, only select logs (i.e., error, security, etc.) Yes, but logs stored in different places (different apps for different use...
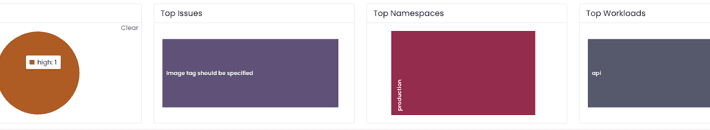
Building a Kubernetes Platform: How & Why to Apply Governance and Policy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Suderman A Platform, sometimes called an “internal developer platform,” is a unified infrastructure that allows development teams in a company to...
Bots-as-a-Service (BaaS): A New Era of Automated Bot Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers Bots-as-a-service (BaaS) is a cloud-based platform that offers pre-built bots to automate mundane tasks such as customer support, data entry,...
Randall Munroe’s XKCD ‘Definition of e’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No, only select logs (i.e., error, security, etc.) Yes, but logs stored in different places (different apps for different use...
Lessons and Takeaways from the FBI’s 2022 Internet Crime Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Spanning 32 pages and featuring statistics galore, there’s a lot to unpack in the FBI’s 2022 Internet Crime Report. The...
CAPTCHA 4WP version 7.2.0 is out now – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joel Barbara We are happy to announce the release of CAPTCHA 4WP version 7.2.0. This version adds some very useful features and...
Independent of their Apps, bad actors banned by various executive orders have pixels/trackers on everyday websites – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ivan Feroot Admin “[China can] manipulate content, and if they want to, to use it for influence operations” – FBI Director Chris...
What Is Break/Fix? Pros, Cons and Why It’s Declining in Popularity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kaseya Until a decade ago, IT service providers supported their clients using primarily a break/fix model. When called, they traveled to their...
How We Built a Supply Chain Security Watchtower: Meet SaaS-Sentinel – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Segura TL;DR: we have built SaaS-sentinel, the first (as far as we know!) SaaS watchtower. The platform allows you to be...
Security Risks of AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Security Risks of AI Stanford and Georgetown have a new report on the security risks of AI—particularly adversarial machine learning—based...
What Is a Ping Flood and How to Prevent It? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici Imagine sitting at your computer, ready to work or browse the internet, only to find that your connection is suddenly...
What Is Cyber Threat Hunting? Process, Types and Solutions – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cezarina Dinu Cyber threat hunting is a proactive search for malicious actors and contents in your system. Threat hunting is a must-have...
TP-Link High-Severity Flaw Added to Mirai Botnet Arsenal – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian A TP-Link Archer A21 (AX1800) consumer-grade WiFi router vulnerability has been used by Mirai botnet to launch DDoS attacks against...
Google ads are being used to spread malware
Malicious actors are using Google advertisements and SEO tactics to entice victims into clicking on links poisoned with malware. According to cyber security company Secureworks, malicious...
New LOBSHOT Malware Deployed Via Google Ads – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Google advertisements have been exploited to distribute various types of malware over the past few months. To trick unsuspecting users...
Chinese APT Alloy Taurus Is Back – Linux Variant of PingPull Malware Is Active – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Across Southeast Asia, Europe and Africa, a new Linux variant of the PingPull malware used by Chinese APT group Alloy...
What Is SOC-as-a-Service (SOCaaS) and How Could Your Company Benefit? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac When building an organization’s cybersecurity posture, there are many decisions that will ultimately lead you to the best result for...
Israel’s Prime Minister has his Facebook account hijacked, website knocked offline – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Yesterday was the official Independence Day of Israel, and the event was “celebrated” in typical style by malicious hackers. In...
Charming Kitten targets critical infrastructure in US and elsewhere with BellaCiao malware – Source: www.tripwire.com
Source: www.tripwire.com – Author: Graham Cluley Iranian state-sponsored hacking group Charming Kitten has been named as the group responsible for a new wave of attacks targeting...
Smashing Security podcast #319: The CEO who also ran IT, Strava strife, and TikTok tall tales – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley A boss is bitten in the bottom after being struck by one of the worst crimes in Finnish history, Strava’s...
RSA Conference 2023 – How AI will infiltrate the world – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Cameron Camp As all things (wrongly called) AI take the world’s biggest security event by storm, we round up of some of...
Google banned 173K developer accounts to block malware, fraud rings – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google says it banned 173,000 developer accounts in 2022 to block malware operations and fraud rings from infecting Android users’...
Linux version of RTM Locker ransomware targets VMware ESXi servers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas RTM Locker is the latest enterprise-targeting ransomware operation found to be deploying a Linux encryptor that targets virtual machines on...
Microsoft fixes Outlook issue blocking access to emails, calendars – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has addressed a known issue affecting Outlook for Microsoft 365 customers that prevented them from accessing group mailboxes and...
New Atomic macOS info-stealing malware targets 50 crypto wallets – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new macOS information-stealing malware named ‘Atomic’ (aka ‘AMOS’) is being sold to cybercriminals via private Telegram channels for a...
A ‘!password20231#’ password may not be as complex as you think – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software Modern IT system administrators know the importance of maintaining a strong password policy. In this article, we’ll explore...
Microsoft: Clop and LockBit ransomware behind PaperCut server hacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft has attributed recent attacks on PaperCut servers to the Clop and LockBit ransomware operations, which used the vulnerabilities to...
Access management made easy, boosting security with user provisioning – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: What is user provisioning? User provisioning enables management teams to control access to business resources, strengthening data security by...
Vietnamese Hackers Linked to ‘Malverposting’ Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A recent ‘malverposting’ campaign linked to a Vietnamese threat actor has been ongoing for months and is estimated to have infected over...