FBI Charges 6, Seizes 48 Domains Linked to DDoS-for-Hire Service PlatformsThe U.S. Department of Justice (DoJ) on Wednesday announced the seizure of 48 domains that offered...
Day: December 20, 2022
Three Steps Towards a More Secure OT Infrastructure
Three Steps Towards a More Secure OT InfrastructureBy Jason Weber, Vice President of Product, Veracity Industrial Networks Years ago, the biggest concern from the plant […]...
Threat Actors Target Ukraine’s DELTA Military System with Info-Stealing Malware
Threat Actors Target Ukraine’s DELTA Military System with Info-Stealing MalwareHackers used an email account belonging to the Ukrainian Ministry of Defense for launching a phishing campaign...
US Gov warns of BEC attacks to hijack shipments of food products
US Gov warns of BEC attacks to hijack shipments of food productsUS government is warning of business email compromise (BEC) attacks aimed at hijacking shipments of...
Mobile App Users at Risk as API Keys of Email Marketing Services Exposed
Mobile App Users at Risk as API Keys of Email Marketing Services ExposedLeaked API keys allow threat actors to perform a variety of unauthorized actionsLeer másLeaked...
Experts spotted a variant of the Agenda Ransomware written in Rust
Experts spotted a variant of the Agenda Ransomware written in RustResearchers spotted a new variant of the Agenda ransomware which is written in the cross-platform programming...
Meta Takes Down Over 200 Covert Influence Operations Since 2017
Meta Takes Down Over 200 Covert Influence Operations Since 2017The most common location for influence operations was Russia, according to MetaLeer másThe most common location for...
Ransomware Groups to Increase Zero-Day Exploit-Based Access Methods in the Future
Ransomware Groups to Increase Zero-Day Exploit-Based Access Methods in the FutureTrend Micro’s latest research paper analyzed ways in which ransomware groups could evolve to stay on...
Old vulnerabilities in Cisco products actively exploited in the wild
Old vulnerabilities in Cisco products actively exploited in the wildIT giant Cisco is warning of threat actors exploiting many old vulnerabilities in attacks in the wild....
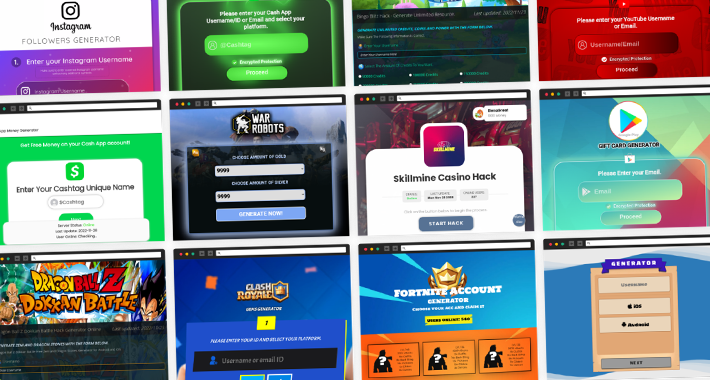
Hackers Bombard Open Source Repositories with Over 144,000 Malicious Packages
Hackers Bombard Open Source Repositories with Over 144,000 Malicious PackagesNuGet, PyPi, and npm ecosystems are the target of a new campaign that has resulted in over...
Ukraine’s Delta Military Intel System Hit by Attacks
Ukraine's Delta Military Intel System Hit by AttacksPhishing campaign spotted by CERT-UALeer másPhishing campaign spotted by CERT-UA
Top 5 Web App Vulnerabilities and How to Find Them
Top 5 Web App Vulnerabilities and How to Find ThemWeb applications, often in the form of Software as a Service (SaaS), are now the cornerstone for...
Fortnite Dev to Pay $520m in Record-Breaking Settlement
Fortnite Dev to Pay $520m in Record-Breaking SettlementFTC reveals gaming firm's privacy violations and design tricksLeer másFTC reveals gaming firm's privacy violations and design tricks
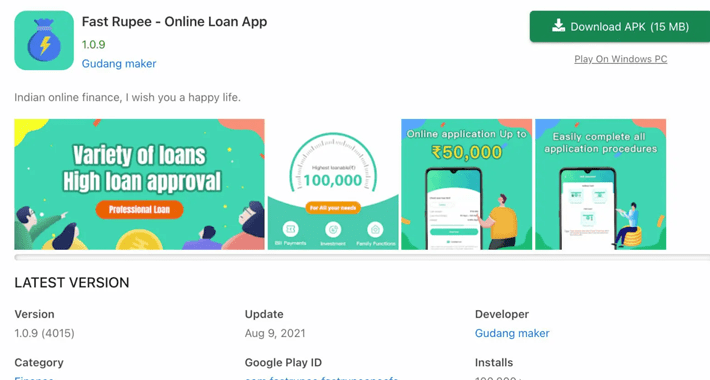
Android Malware Campaign Leverages Money-Lending Apps to Blackmail Victims
Android Malware Campaign Leverages Money-Lending Apps to Blackmail VictimsA previously undocumented Android malware campaign has been observed leveraging money-lending apps to blackmail victims into paying up...
UK Privacy Regulator Names and Shames Breached Firms
UK Privacy Regulator Names and Shames Breached FirmsICO publishes detailed list of complaints and investigationsLeer másICO publishes detailed list of complaints and investigations
Specific IoT and OT security predictions for North America for 2023
Specific IoT and OT security predictions for North America for 2023The year 2023 will see a significant shift in the way cyberattacks are engineered and that...
How to enable event collection in Windows Server
How to enable event collection in Windows ServerEvent logs register information about software and hardware events that occur in a system, and they are a key...
DoD supply chain lessons learned
DoD supply chain lessons learned A July 2022 survey of 300 U.S. Department of Defense (DoD) IT contractors shows a woeful lack of information security in...
OneCoin scammer Sebastian Greenwood pleads guilty, “Cryptoqueen” still missing
OneCoin scammer Sebastian Greenwood pleads guilty, “Cryptoqueen” still missingThe Cryptoqueen herself is still missing, but her co-conspirator, who is said to have pocketed over $20m a...