Pwn2Own contest concludes with nearly $1m paid out to ethical hackersWhich is pocket change compared to what criminals will pay for zero-days, but thankfully community spirit...
Day: December 20, 2022
Researchers smell a cryptomining Chaos RAT targeting Linux systems
Researchers smell a cryptomining Chaos RAT targeting Linux systemsSmells like Russian miscreants A type of cryptomining malware targeting Linux-based systems has added capabilities by incorporating an...
Apple should pay €6m to French data watchdog for tracking users without consent, says official
Apple should pay €6m to French data watchdog for tracking users without consent, says officialRecommendation from top CNIL advisor claims Cupertino broke EU privacy laws Apple...
Uber staff info leaks after supplier Teqtivity gets pwned
Uber staff info leaks after supplier Teqtivity gets pwnedThankfully no customer info – but the spotlight is back on third-party attacks Uber, which has suffered a...
LockBit threatens to leak confidential info stolen from California’s beancounters
LockBit threatens to leak confidential info stolen from California's beancountersDatabases, details of 'sexual proceedings in court' and more apparently pilfered from finance IT LockBit claims it...
Microsoft ain’t the only one squashing exploited-in-the-wild bugs this month
Microsoft ain't the only one squashing exploited-in-the-wild bugs this monthPlus there's a PoC for this unpatched Cisco bug Patch Tuesday For its final Patch Tuesday of...
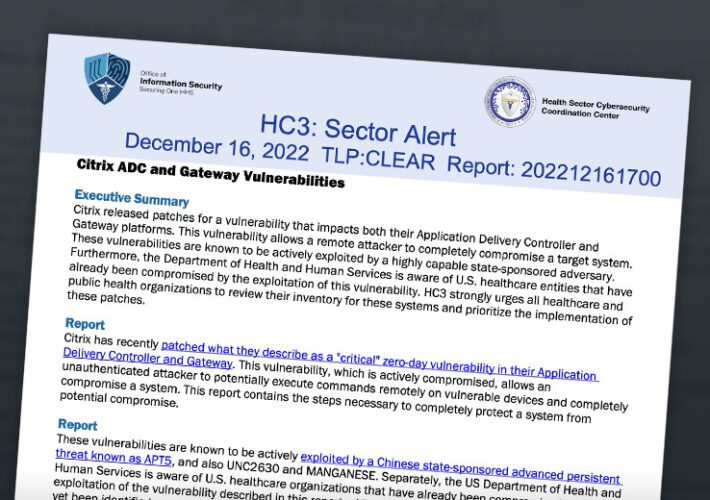
Citrix patches critical ADC flaw the NSA says is already under attack from China
Citrix patches critical ADC flaw the NSA says is already under attack from ChinaYet more pain for the software formerly known as NetScaler The China-linked crime...
Top 5 Tips for Choosing Endpoint Security
Top 5 Tips for Choosing Endpoint SecurityFollowing years now of digital transformation, cloud migration and deployment of hybrid workforces, enterprises have more endpoints than ever. Which...
Healthcare: Essential Defenses for Combating Ransomware
Healthcare: Essential Defenses for Combating RansomwareMove Infrastructure to the Cloud and Hone Incident Response Plans, Experts SayTo avoid having to even consider paying a ransom, experts...
EU takes another step towards US data-sharing agreement
EU takes another step towards US data-sharing agreementCampaigners say it's unlikely to pass a test in the courts, though The EU has issued a draft decision...
Chinese Hackers Exploit Citrix Vulnerabilities
Chinese Hackers Exploit Citrix VulnerabilitiesHealth Sector Entities Urged to Patch Citrix ADC, Gateway FlawsChinese hackers are exploiting known vulnerabilities in a Citrix networking appliance and virtual...
Microsoft Vulnerability Upgraded to Critical Due to RCE Risk
Microsoft Vulnerability Upgraded to Critical Due to RCE RiskCode-Execution Bug Has Broader Scope that Flaw Exploited by EternalBlue, IBM SaysMicrosoft upgraded a vulnerability first discovered in...
Patch Tuesday updates spark errors when creating Hyper-V VMs
Patch Tuesday updates spark errors when creating Hyper-V VMsSomething's broken, mom! Microsoft offers workaround while trying to think up a fix Updates to Windows Server that...
Nueva variante de Agenda Ransomware, escrita en Rust, dirigida a la infraestructura crítica
Nueva variante de Agenda Ransomware, escrita en Rust, dirigida a la infraestructura críticaSe ha observado una variante de Rust de una variedad de ransomware conocida como...
Phishing Targets Ukrainian Battlefield Awareness Tool Users
Phishing Targets Ukrainian Battlefield Awareness Tool UsersDigital Map Users Lured Into Installing Malware that Looked for Office FilesA phishing campaign against users of a Ukrainian battlefield...
Samba emite actualizaciones de seguridad para parchar múltiples vulnerabilidades de alta gravedad
Samba emite actualizaciones de seguridad para parchar múltiples vulnerabilidades de alta gravedadSamba ha lanzado actualizaciones de software para remediar múltiples vulnerabilidades que, si se explotan con...
TikTok could be banned from America, thanks to proposed bipartisan bill
TikTok could be banned from America, thanks to proposed bipartisan billIf you listen really closely, you can hear Mark Zuckerberg's excitement The US government's crackdown on...
AWS strains to make Simple Storage Service not so simple to screw up
AWS strains to make Simple Storage Service not so simple to screw upNot Amazon's fault buckets are exposed, but the loaded shotgun and your foot are...
Seven smuggled US military tech for Moscow, say Feds
Seven smuggled US military tech for Moscow, say FedsNuclear, hypersonic hardware is one thing, but you can probably keep the quantum computer stuff, Vlad The US...
Malicious Microsoft-signed Windows drivers wielded in cyberattacks
Malicious Microsoft-signed Windows drivers wielded in cyberattacksHandy tools to kill off security protections get Redmond's stamp of approval Microsoft says it has suspended several third-party developer...
Moving Containers: Uncovering Challenges. Finding Solutions.
Moving Containers: Uncovering Challenges. Finding Solutions. Get expert tips and best practices for securing containers in your business in our blog from Cloud Security experts, GuidePoint...
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgs
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgsContenido de la entradaLeer másProofpoint News Feed
On the 12th day of the Rackspace email disaster, it did not give to me …
On the 12th day of the Rackspace email disaster, it did not give to me …… a working Exchange inbox tree Updated There's no end –...
How to Address the Skills Gap Crisis with DCIM Software
How to Address the Skills Gap Crisis with DCIM SoftwareData centers are essential components of the modern business landscape, providing the critical infrastructure that enables businesses...
Agenda Ransomware Uses Rust to Target More Vital Industries
Agenda Ransomware Uses Rust to Target More Vital IndustriesThis year, various ransomware-as-a-service groups have developed versions of their ransomware in Rust, including Agenda. Agenda's Rust variant...
Lacework Stiffens Cloud Security Posture Management
Lacework Stiffens Cloud Security Posture Management Lacework has added additional cloud security posture management (CSPM) capabilities to its platform to make it possible to create fine-grained...
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgs
Iran-linked Charming Kitten espionage gang bares claws to pollies, power orgsIf you get email from 'Samantha Wolf', congrats: you're important enough to make a decent target...
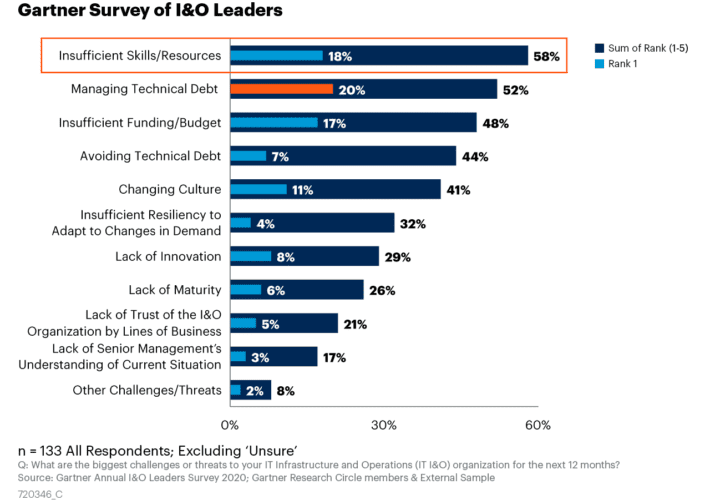
The security skills shortage is here, here’s how to prepare
The security skills shortage is here, here’s how to prepareCorporate security is near the top of the list of CIO concerns for 2023 — but a...
Two-Thirds of Security Pros Have Burnt Out in Past Year
Two-Thirds of Security Pros Have Burnt Out in Past YearExcessive workload is the most common contributing factorLeer másExcessive workload is the most common contributing factor
LogRhythm Partners with SentinelOne to Accelerate Prevention, Detection and Response for Enterprise Environments
LogRhythm Partners with SentinelOne to Accelerate Prevention, Detection and Response for Enterprise EnvironmentsNew integration empowers security teams to identify behavioral anomalies, internal and external threats, and...