U.S. charges Russian suspects with operating Z-Library e-Book siteAnton Napolsky (33) and Valeriia Ermakova (27), two Russian nationals, were charged with intellectual property crimes linked to...
Day: November 17, 2022
Everything You Need to Know to Avoid a Man-in-the-Middle Mobile Attack
Everything You Need to Know to Avoid a Man-in-the-Middle Mobile Attack Monkey in the middle, the beloved playground staple, extends beyond schoolyards into corporate networks, home...
What Is Internet Security?
What Is Internet Security? Internet security is a broad term that refers to a wide range of tactics that aim to protect activities conducted over the...
What Is Bloatware and How Can It Impact Security?
What Is Bloatware and How Can It Impact Security? The joy of purchasing a new device is liberating. Now you can work, learn, and play faster...
Microsoft urges devs to migrate away from .NET Core 3.1 ASAP
Microsoft urges devs to migrate away from .NET Core 3.1 ASAPMicrosoft has urged developers still using the long-term support (LTS) release of .NET Core 3.1 to migrate to the...
ESET rolls out new consumer offerings to improve home security
ESET rolls out new consumer offerings to improve home securityESET's newest consumer product release has taken a comprehensive approach to security to guard against a full...
F5 fixes two remote code execution flaws in BIG-IP, BIG-IQ
F5 fixes two remote code execution flaws in BIG-IP, BIG-IQF5 has released hotfixes for its BIG-IP and BIG-IQ products, addressing two high-severity flaws allowing attackers to...
Australian special forces member allegedly stole and published personal data of intelligence official
Australian special forces member allegedly stole and published personal data of intelligence officialADF is investigating alleged theft and use of cybertools to hack private accounts of...
Mobiles are ‘potential goldmines’ for hostile states, MPs warned
Mobiles are ‘potential goldmines’ for hostile states, MPs warnedCommons speaker suggests phones not be taken into meetings as UK cyber security centre issues 10 ‘top tips’...
Palo Alto Networks to Buy Cider Security for $300M: Report
Palo Alto Networks to Buy Cider Security for $300M: ReportPalo Alto's First Big M&A Since Early 2021 Will Help Secure Engineering ProcessesPalo Alto Networks will make...
Global Cyber Risk at Elevated Level
Global Cyber Risk at Elevated LevelNorth America Least Prepared for CyberattacksLeer másTrend Micro Research, News, PerspectivesNorth America Least Prepared for Cyberattacks
Smashing Security podcast #298: Housing market scams, Twitter 2FA, and the fesshole
Smashing Security podcast #298: Housing market scams, Twitter 2FA, and the fessholeElon Musk is still causing chaos at Twitter (and it's beginning to impact users), are...
Department of Financial Services Proposes Cybersecurity Regulation Updates
Department of Financial Services Proposes Cybersecurity Regulation UpdatesEarlier this month, Superintendent of Financial Services Adrienne A. Harris announced that the New York State Department of Financial...
Botnets, Trojans, DDoS From Ukraine and Russia Have Increased Since Invasion
Botnets, Trojans, DDoS From Ukraine and Russia Have Increased Since InvasionThe news comes from a report by Top10VPN and is based on data by the Shadowserver...
Iran-linked threat actors compromise US Federal Network
Iran-linked threat actors compromise US Federal NetworkIran-linked threat actors compromised a Federal Civilian Executive Branch organization using a Log4Shell exploit and installed a cryptomining malware. According...
Majority of Companies Reduce Cybersecurity Staff Over Holidays
Majority of Companies Reduce Cybersecurity Staff Over HolidaysCybereason’s latest report is based on a survey of more than 1200 cybersecurity professionalsLeer másCybereason’s latest report is based...
Higher Education Organization Improves Cybersecurity Posture with NodeZero
Higher Education Organization Improves Cybersecurity Posture with NodeZeroWhen the director of technology for a higher education organization went looking for a better way to identify and...
Scottish Embassy Guard in Berlin Caught Spying for Russia
Scottish Embassy Guard in Berlin Caught Spying for RussiaYou might wonder who in the world right now would be caught spying for Putin. Well have I...
Android Privacy Sandbox Beta to Roll Out By Early 2023
Android Privacy Sandbox Beta to Roll Out By Early 2023The project aims to bring new and more private advertising solutions to mobileLeer másThe project aims to...
Open banking: Tell me what you buy, and I’ll tell you who you are
Open banking: Tell me what you buy, and I’ll tell you who you areThe convenience with which you manage all your financial wants and needs may...
It’s Official. Tesla Has Reduced Driver Safety
It’s Official. Tesla Has Reduced Driver SafetyYou may recall that Elon Musk was a CEO fired from PayPal for his gross incompetence. Somehow he kept all...
Randall Munroe’s XKCD ‘Y2K And 2038’
Randall Munroe’s XKCD ‘Y2K And 2038’Randall Munroe’s XKCD ‘Y2K And 2038’ via the comic artistry and dry wit of Randall Munroe, resident at XKCD! Permalink The...
WWII British Soldiers Successfully Deployed God and Sugar to Defeat Nazi Disinformation
WWII British Soldiers Successfully Deployed God and Sugar to Defeat Nazi DisinformationIt’s really a footnote to stories about Nazi Germany losing the war in 1942, yet...
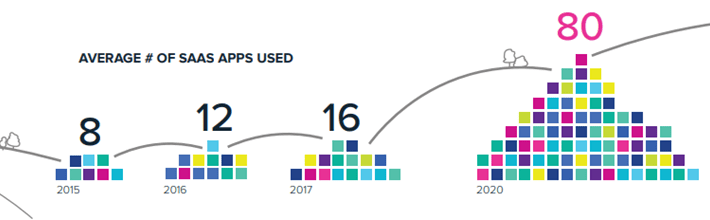
A Detailed Orientation To SaaS Application and its Security Aspect
A Detailed Orientation To SaaS Application and its Security AspectWith the enormous utilization of the internet and business goals to save additional expenses, SaaS applications are...
High Severity Vulnerabilities Reported in F5 BIG-IP and BIG-IQ Devices
High Severity Vulnerabilities Reported in F5 BIG-IP and BIG-IQ DevicesMultiple security vulnerabilities have been disclosed in F5 BIG-IP and BIG-IQ devices that, if successfully exploited, to...
Iranian Hackers Compromised a U.S. Federal Agency’s Network Using Log4Shell Exploit
Iranian Hackers Compromised a U.S. Federal Agency’s Network Using Log4Shell ExploitIranian government-sponsored threat actors have been blamed for compromising a U.S. federal agency by taking advantage...
North Korean Hackers Targeting Europe and Latin America with Updated DTrack Backdoor
North Korean Hackers Targeting Europe and Latin America with Updated DTrack BackdoorHackers tied to the North Korean government have been observed using an updated version of...