A school district’s guide to vendor risk managementVendor security is an important concern for school districts as students become digitally native at young ages. Educators can...
Day: November 17, 2022
Critical Infrastructure’s Open Source Problem
Critical Infrastructure’s Open Source Problem Open source has a security problem, and that could have real-world impact when it affects critical infrastructure. According to research from...
Cybercrime is the New Covid
Cybercrime is the New CovidCovid-19 is sooo 2020! Data breaches, ransomware, and cybercrime are trending this year, and sadly, it doesn’t seem like they are slowing...
GRIT Ransomware Report: October 2022
GRIT Ransomware Report: October 2022 October demonstrated an interesting month in the ransomware environment. Lockbit, the most prolific ransomware group in 2022, saw a massive […]...
Introducing Recon to Stay Ahead of Attackers
Introducing Recon to Stay Ahead of Attackers API security can feel impossible to master. That's because you need to know how many APIs you have, the...
Vendor Lock-In, or Just Too Sticky?
Vendor Lock-In, or Just Too Sticky?What’s vendor lock-in? Vendor lock-in refers to your inability to easily switch from one vendor’s service or products to another’s. A...
Dell Appliance Uses Machine Learning to Automate Data Protection
Dell Appliance Uses Machine Learning to Automate Data Protection Dell Technologies today unveiled an integrated Dell PowerProtect Data Manager Appliance that increases cyberresilience by using machine...
Data Privacy and Remote Work: Three Things Businesses Need to Know
Data Privacy and Remote Work: Three Things Businesses Need to Know Due to the COVID-19 pandemic, a large-scale and abrupt shift in employee work habits from...
People Are People: Gender Equality at Praetorian
People Are People: Gender Equality at PraetorianEarly this Summer, we shared our thoughts on the industry-wide shortage of cybersecurity talent to meet an ever-growing demand. One...
100 Apps, Endless Security Checks
100 Apps, Endless Security ChecksOn average, organizations report using 102 business-critical SaaS applications, enabling operations of most departments across an organization, such as IT and Security, Sales, Marketing,...
Chinese Spy Gets 20 Years for Aviation Espionage Plot
Chinese Spy Gets 20 Years for Aviation Espionage PlotUS authorities land a rare win in fight against state-backed info-theftLeer másUS authorities land a rare win in...
FBI-Wanted Leader of the Notorious Zeus Botnet Gang Arrested in Geneva
FBI-Wanted Leader of the Notorious Zeus Botnet Gang Arrested in GenevaA Ukrainian national who has been wanted by the U.S for over a decade has been...
Chinese Hackers Using 42,000 Imposter Domains in Massive Phishing Attack Campaign
Chinese Hackers Using 42,000 Imposter Domains in Massive Phishing Attack CampaignA China-based financially motivated group is leveraging the trust associated with popular international brands to orchestrate...
Black Friday and retail season – watch out for PayPal “money request” scams
Black Friday and retail season – watch out for PayPal “money request” scamsDon't let a keen eye for bargains lead you into risky online behaviour...Leer másNaked...
US: Iranian Hackers Breached Government with Log4Shell
US: Iranian Hackers Breached Government with Log4ShellThreat actors installed crypto-miner and achieved persistenceLeer másThreat actors installed crypto-miner and achieved persistence
FBI issues warning over impersonation scam; New phishing campaign encourages targets to call malicious actors
FBI issues warning over impersonation scam; New phishing campaign encourages targets to call malicious actorsPhishing emails continue to be sent in high volumes. Earthweb has identified...
Google wins lawsuit against alleged Russian botnet herders
Google wins lawsuit against alleged Russian botnet herdersJudge tells tale of two men, their lawyer, and a 'willful campaign... to mislead the court' A New York...
Android security: Which smartphones can enterprises trust?
Android security: Which smartphones can enterprises trust?Google’s Android operating system dominates smartphone usage throughout the world — in every region except North America and Oceania, in...
PCI Council Launches Flexible Mobile Payments Standard
PCI Council Launches Flexible Mobile Payments StandardAnnouncement recognizes growing volume of smartphone paymentsLeer másAnnouncement recognizes growing volume of smartphone payments
Cybersecurity Industry Must Maintain Public Faith in Technology, Says NCSC Founder
Cybersecurity Industry Must Maintain Public Faith in Technology, Says NCSC FounderThe NCSC's founding CEO, Ciaran Martin, explains why the cyber industry is now a public goodLeer...
MFA Fatigue Attacks Are on the Rise
MFA Fatigue Attacks Are on the RiseMFA Fatigue seems to be hackers` favorite tool this fall, as we have lately witnessed an increase in numbers of...
More Than Half of Black Friday Spam Emails Are Scams
More Than Half of Black Friday Spam Emails Are ScamsNew research analyzes email scam techniques in the build-up to this year's Black FridayLeer másNew research analyzes...
Hundreds of Amazon RDS Snapshots Discovered Leaking Users’ Data
Hundreds of Amazon RDS Snapshots Discovered Leaking Users' DataThe discovery was made by security researchers at MitigaLeer másThe discovery was made by security researchers at Mitiga
How to Prevent Privilege Escalation Attacks?
How to Prevent Privilege Escalation Attacks?Privilege escalation, like any cyberattack, takes advantage of flaws in network services and applications, especially those with weak access control systems....
Massive Wave of TrojanOrders Attacks Target Magento Stores
Massive Wave of TrojanOrders Attacks Target Magento StoresA significant increase in “TrojanOrders” attacks against Magento 2 websites is being attributed to at least seven hacker groups....
Tank, the leader of the Zeus cybercrime gang, was arrested by the Swiss police
Tank, the leader of the Zeus cybercrime gang, was arrested by the Swiss policeA suspected leader of the Zeus cybercrime gang, Vyacheslav Igorevich Penchukov (aka Tank), was...
A U.S. Federal Agency Was the Victim of Iranian Government-Sponsored Hackers
A U.S. Federal Agency Was the Victim of Iranian Government-Sponsored HackersState-supported Iranian cybercriminals are suspected in an incident that led to a breach in a U.S....
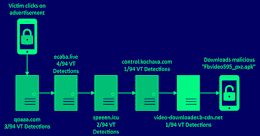
Emotet Targets New Victims: Amazon, DHL, and the Ukrainian War
Emotet Targets New Victims: Amazon, DHL, and the Ukrainian WarAlthough other malware families are still prevalent and dangerous, Emotet has climbed to the top of the...
Suspected Leader of Zeus Cybercrime Gang Arrested in Switzerland
Suspected Leader of Zeus Cybercrime Gang Arrested in SwitzerlandOne of the leaders of the renowned JabberZeus cybercrime group, Vyacheslav Igorevich Penchukov (aka Tank), was detained in...
Microsoft fixes bug behind Windows 10 freezes, desktop issues
Microsoft fixes bug behind Windows 10 freezes, desktop issuesMicrosoft has resolved a known issue triggering errors and temporarily causing the taskbar and desktop to disappear on...