2023 IT Security Predictions From Professionals Who Live It Every DayTo beat the prediction rush, Radware reached out to several of our customers to find out...
Day: November 1, 2022
The Mirage of Mandiant: Post-Acquisition Follow-Up
The Mirage of Mandiant: Post-Acquisition Follow-UpRevisiting the strategic implications of Google Cloud and Mandiant following the Google Cloud Next conference. The post The Mirage of Mandiant:...
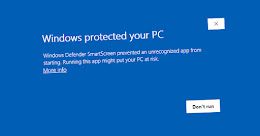
Unofficial Patch Released for New Actively Exploited Windows MotW Vulnerability
Unofficial Patch Released for New Actively Exploited Windows MotW VulnerabilityAn unofficial patch has been made available for an actively exploited security flaw in Microsoft Windows that...
Fodcha DDoS Botnet Resurfaces with New Capabilities
Fodcha DDoS Botnet Resurfaces with New CapabilitiesThe threat actor behind the Fodcha distributed denial-of-service (DDoS) botnet has resurfaced with new capabilities, researchers reveal. This includes changes...
Tips for Choosing a Pentesting Company
Tips for Choosing a Pentesting CompanyIn today's world of automated hacking systems, frequent data breaches and consumer protection regulations such as GDPR and PCI DSS, penetration...
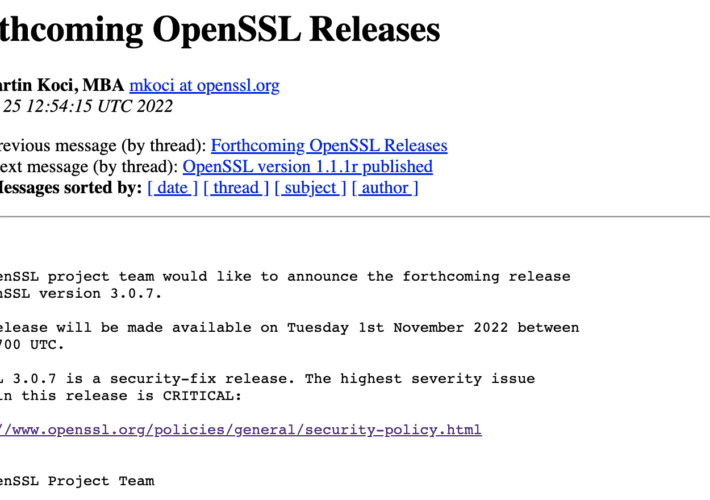
Undisclosed OpenSSL vulnerability: Free scripts for target scoping
Undisclosed OpenSSL vulnerability: Free scripts for target scoping Tomorrow is “patch Tuesday” and it's a notable one. The OpenSSL project team announced last week that they...
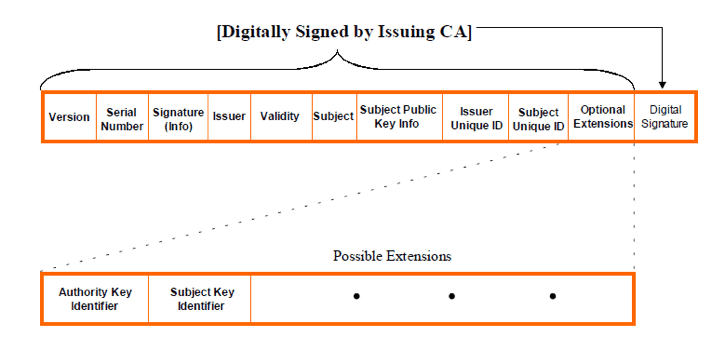
How Does a Browser Trust a Certificate?
How Does a Browser Trust a Certificate?How Does a Browser Trust a Certificate? Scott Carter Mon, 10/31/2022 - 17:00 6490 views Browsers prevent this type of...
Psychotherapy extortion suspect: arrest warrant issued
Psychotherapy extortion suspect: arrest warrant issuedWanted! Not only the extortionist who abused the data, but also the CEO who let it happen.Leer másNaked SecurityWanted! Not only...
Safeguards Rule: 9 Steps to Compliance for Auto Dealerships
Safeguards Rule: 9 Steps to Compliance for Auto DealershipsAutomobile dealerships collect and store large amounts of consumer data, including Social Security numbers, bank account information, and...
CISA releases cybersecurity performance goals to reduce risk and impact of adversarial threats
CISA releases cybersecurity performance goals to reduce risk and impact of adversarial threatsLast week, the US Cybersecurity and Infrastructure Security Agency (CISA) released voluntary cross-sector Cybersecurity...
Nearly a Third of Cybersecurity Leaders Considering Quitting
Nearly a Third of Cybersecurity Leaders Considering QuittingResearch commissioned by BlackFog shows that work life balance is most disliked part of the job for cybersecurity leaders....
Engineering workstation attacks on industrial control systems double: Report
Engineering workstation attacks on industrial control systems double: ReportEngineering workstation compromises were the initial attack vector in 35% of all operational technology (OT) and industrial control...
On Demand Subscription: Drive Immediate Value From SOC Prime Platform
On Demand Subscription: Drive Immediate Value From SOC Prime Platform A community-driven approach based on Detection-as-Code principles and cutting-edge technology leveraging Sigma language and MITRE ATT&CK®...
CVE-2022-40684 Detection: A Critical Fortinet Authentication Bypass Vulnerability Exploited in the Wild
CVE-2022-40684 Detection: A Critical Fortinet Authentication Bypass Vulnerability Exploited in the Wild Heads up! A new critical vulnerability is on the radar. Fortinet has recently disclosed...
Air New Zealand warns of an ongoing credential stuffing attack
Air New Zealand warns of an ongoing credential stuffing attackAir New Zealand suffered a security breach, multiple customers have been locked out of their accounts after...
Russia Suspected in Truss Phone Hacking Scandal
Russia Suspected in Truss Phone Hacking ScandalOne year’s worth of messages reportedly downloaded from former PM’s deviceLeer másOne year’s worth of messages reportedly downloaded from former...
Trick or treat? Stay so cyber‑safe it’s scary – not just on Halloween
Trick or treat? Stay so cyber‑safe it’s scary – not just on HalloweenGather around, folks, to learn about some of the ghastliest tricks used by criminals online...
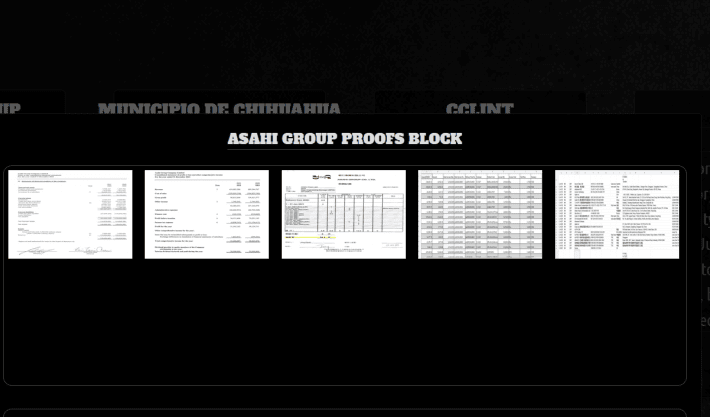
BlackByte ransomware group hit Asahi Group Holdings, a precision metal manufacturing and metal solution provider
BlackByte ransomware group hit Asahi Group Holdings, a precision metal manufacturing and metal solution providerThe BlackByte ransomware group claims to have compromised Asahi Group Holdings, a precision metal...
Hackers Target Australian Defense Communications Platform With Ransomware
Hackers Target Australian Defense Communications Platform With RansomwareThe firm is one of the defense department's external providers employed to run one of its websitesLeer másThe firm...
Europe’s Biggest Copper Producer Hit by Cyber-Attack
Europe's Biggest Copper Producer Hit by Cyber-AttackAurubis forced to take IT systems offlineLeer másAurubis forced to take IT systems offline
Most Online Shoppers Would Leave Retailer Following Breach
Most Online Shoppers Would Leave Retailer Following BreachAkamai study finds low levels of trust among consumersLeer másAkamai study finds low levels of trust among consumers
SOC Prime Threat Bounty — September 2022 Results
SOC Prime Threat Bounty — September 2022 Results September ‘22 Publications In September, members of the Threat Bounty Community submitted 441 rules for review by the...
Former British Prime Minister Liz Truss ‘s phone was allegedly hacked by Russian spies
Former British Prime Minister Liz Truss ‘s phone was allegedly hacked by Russian spiesAccording to the Daily Mail, Former British Prime Minister Liz Truss ‘s personal...
CISA, FBI, MS-ISAC Publish Guidelines For Federal Agencies on DDoS Attacks
CISA, FBI, MS-ISAC Publish Guidelines For Federal Agencies on DDoS AttacksThe guidance is for network defenders and leaders to understand and respond to DDoS attacksLeer másThe...
German BKA arrested the alleged operator of Deutschland im Deep Web darknet market
German BKA arrested the alleged operator of Deutschland im Deep Web darknet marketGerman police arrested a student that is suspected of being the administrator of ‘Deutschland...
Data Breach of Missile Maker MBDA May Have Been Real: CloudSEK
Data Breach of Missile Maker MBDA May Have Been Real: CloudSEKThe researchers were able to obtain the ZIP file containing the samples for the data breachLeer...
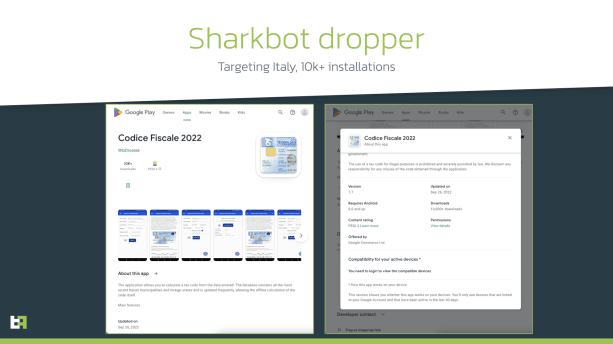
Malicious dropper apps on Play Store totaled 30.000+ installations
Malicious dropper apps on Play Store totaled 30.000+ installationsThreatFabric researchers discovered five malicious dropper apps on Google Play Store with more than 130,000 downloads. Researchers at...
Interview with Threat Bounty Developer: Wirapong Petshagun
Interview with Threat Bounty Developer: Wirapong Petshagun SOC Prime Threat Bounty Program keeps uniting enthusiastic and keen detection content developers who joined the community to contribute...
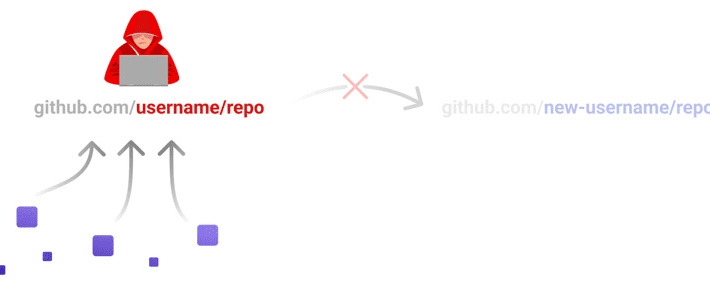
GitHub flaw could have allowed attackers to takeover repositories of other users
GitHub flaw could have allowed attackers to takeover repositories of other usersA critical flaw in the cloud-based repository hosting service GitHub could’ve allowed attackers to takeover...
Magniber Ransomware Detection: Threat Actors Spread JavaScript Files Targeting Windows Users
Magniber Ransomware Detection: Threat Actors Spread JavaScript Files Targeting Windows Users Throughout 2021-2022, ransomware continues to be one of the dominant trends in the cyber threat...