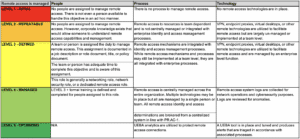
Measuring Up: How to Architect a Systematic Security Program – Part 2 In Part 1 of this series , we discussed how organizations can go about selecting...
Day: November 1, 2022
Last Years Open Source – Tomorrow’s Vulnerabilities
Last Years Open Source - Tomorrow's VulnerabilitiesLinus Torvalds, the creator of Linux and Git, has his own law in software development, and it goes like this:...
Critical RCE Vulnerability Reported in ConnectWise Server Backup Solution
Critical RCE Vulnerability Reported in ConnectWise Server Backup SolutionIT service management software platform ConnectWise has released Software patches for a critical security vulnerability in Recover and...
See Tickets Breach Sheds Light on the Blind-Side of Web Security
See Tickets Breach Sheds Light on the Blind-Side of Web SecurityDespite its name, leading ticketing service provider See Tickets was blind to a card skimming attack...
Researchers Disclose Details of Critical ‘CosMiss’ RCE Flaw Affecting Azure Cosmos DB
Researchers Disclose Details of Critical 'CosMiss' RCE Flaw Affecting Azure Cosmos DBMicrosoft on Tuesday said it addressed an authentication bypass vulnerability in Jupyter Notebooks for Azure Cosmos DB...
Chinese Hackers Using New Stealthy Infection Chain to Deploy LODEINFO Malware
Chinese Hackers Using New Stealthy Infection Chain to Deploy LODEINFO MalwareThe Chinese state-sponsored threat actor known as Stone Panda has been observed employing a new stealthy...
SHA-3 code execution bug patched in PHP – check your version!
SHA-3 code execution bug patched in PHP – check your version!As everyone waits for news of a bug in OpenSSL, here's a reminder that other cryptographic...
BSidesLV 2022 Lucky13 I Am The Cavalry (IATC) – Lily H. Newman’s, Joe Uchill’s, Suzanne Smalley’s ‘M33t The Press: CyberSafety Got Real: Now What?’
BSidesLV 2022 Lucky13 I Am The Cavalry (IATC) – Lily H. Newman’s, Joe Uchill’s, Suzanne Smalley’s ‘M33t The Press: CyberSafety Got Real: Now What?’Our sincere thanks...
Using Binary Analysis to Hunt Down OSS Vulnerabilities
Using Binary Analysis to Hunt Down OSS Vulnerabilities Having an SBOM and software inventory aids in identifying 3rd-party vulnerabilities and risk The post Using Binary Analysis...
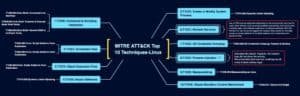
Using Sysmon for Linux to Monitor Against MITRE ATT&CK Techniques
Using Sysmon for Linux to Monitor Against MITRE ATT&CK TechniquesThere was a lot covered at this year’s 2022 RhythmWorld Security Conference! In one of our more...
The OSPO – the front line for secure open-source software supply chain governance
The OSPO – the front line for secure open-source software supply chain governanceOrganizations of every shape, size, and sector have embraced open-source software (OSS). The financial,...
Fraudulent Instruction Losses Spike in 2022
Fraudulent Instruction Losses Spike in 2022Insurer says claimants have risen in nearly every sectorLeer másInsurer says claimants have risen in nearly every sector
FTC Takes Enforcement Action Against EdTech Giant Chegg
FTC Takes Enforcement Action Against EdTech Giant CheggRegulator’s order requires firm to improve data security practicesLeer másRegulator’s order requires firm to improve data security practices
NCSC Issued 34 Million Cyber Alerts in Past Year
NCSC Issued 34 Million Cyber Alerts in Past YearUK security agency helps organizations with early warning serviceLeer másUK security agency helps organizations with early warning service
LockBit Dominates Ransomware Campaigns in 2022: Deep Instinct
LockBit Dominates Ransomware Campaigns in 2022: Deep InstinctThe figures come from the 2022 Interim Cyber Threat Report by Deep InstinctLeer másThe figures come from the 2022...
CISA Publishes Multi-Factor Authentication Guidelines to Tackle Phishing
CISA Publishes Multi-Factor Authentication Guidelines to Tackle PhishingThe guidelines describe methods threat actors use to steal MFA credentials and how to defend against themLeer másThe guidelines...
Osaka Hospital Halts Services After Ransomware Attack
Osaka Hospital Halts Services After Ransomware AttackEmergency operations are continuing, but the hospital system failed and cannot be accessedLeer másEmergency operations are continuing, but the hospital...
Instagram Bug Causes Users’ Accounts Suspension
Instagram Bug Causes Users’ Accounts SuspensionInstagram users might have taken the greatest Halloween scare ever yesterday after they found themselves unable to access their accounts for...
Samsung Galaxy Store flaw could have allowed installing malicious apps on target devices
Samsung Galaxy Store flaw could have allowed installing malicious apps on target devicesA security flaw in the Galaxy Store app for Samsung devices could have potentially...
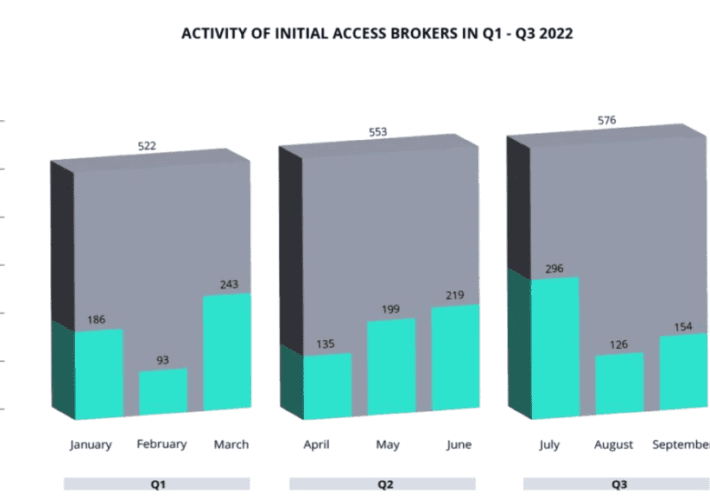
Ransomware activity and network access sales in Q3 2022
Ransomware activity and network access sales in Q3 2022Ransomware activity report: Threat actors are selling access to hundreds of organizations, with a cumulative requested price of...
Multiple Vulnerabilities Discovered in Juniper Junos OS
Multiple Vulnerabilities Discovered in Juniper Junos OSA series of severe security flaws have been disclosed to affect Juniper Networks devices, some of which might end up being...
Experts warn of critical RCE in ConnectWise Server Backup Solution
Experts warn of critical RCE in ConnectWise Server Backup SolutionConnectWise has addressed a critical remote code execution vulnerability impacting Recover and R1Soft Server Backup Manager (SBM)....
Denmark’s Journey to Becoming the Most Cyber-Secure Country
Denmark’s Journey to Becoming the Most Cyber-Secure CountryDenmark is one of the most digitalized countries worldwide, with technologies used in the private and public sectors as...
$4 Million in Exchange for Access to 576 Corporate Networks
$4 Million in Exchange for Access to 576 Corporate NetworksAccording to a new report published by cybersecurity researchers, hackers are selling access to 576 corporate networks...
Detect CVE-2021-39144: Critical Remote Code Execution Vulnerability in VMware Cloud Foundation via XStream Open Source Library
Detect CVE-2021-39144: Critical Remote Code Execution Vulnerability in VMware Cloud Foundation via XStream Open Source Library Another day, another exploit emerges in the wild to cause...
Actively exploited Windows MoTW zero-day gets unofficial patch
Actively exploited Windows MoTW zero-day gets unofficial patchA free unofficial patch has been released for an actively exploited zero-day that allows files signed with malformed signatures...
Iran’s Digital Surveillance Tools Leaked
Iran’s Digital Surveillance Tools LeakedIt’s Iran’s turn to have its digital surveillance tools leaked: According to these internal documents, SIAM is a computer system that works...
New Azov data wiper tries to frame researchers and BleepingComputer
New Azov data wiper tries to frame researchers and BleepingComputerA new and destructive 'Azov Ransomware' data wiper is being heavily distributed through pirated software, key generators,...
Google ad for GIMP.org served info-stealing malware via lookalike site
Google ad for GIMP.org served info-stealing malware via lookalike siteSearching for 'GIMP' on Google as recently as last week would show visitors an ad for 'GIMP.org,' the official website of...
The Worst Black Friday and Cyber Monday Scams – And How to Avoid Them
The Worst Black Friday and Cyber Monday Scams – And How to Avoid Them On Black Friday and Cyber Monday, the deals roll out. So do...