A Modern Database Meets a Modern DevOps Data PlatformA Modern Database Meets a Modern DevOps Data Platform jasonaxelrod Fri, 08/12/2022 - 12:50 Delphix and Cockroach Labs...
Month: August 2022
S3 Ep95: Slack leak, Github onslaught, and post-quantum crypto [Audio + Text]
S3 Ep95: Slack leak, Github onslaught, and post-quantum crypto [Audio + Text]Latest episode - listen now! (Or read the transcript if you prefer.)Leer másNaked SecurityLatest episode...
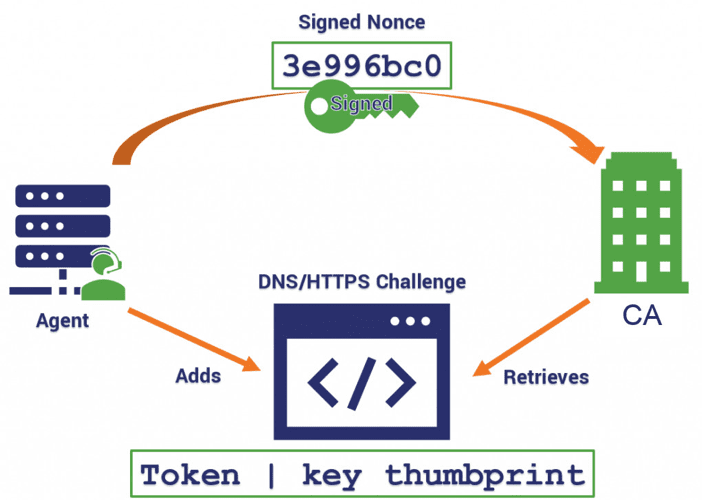
What is the Automated Certificate Management Environment (ACME) Protocol?
What is the Automated Certificate Management Environment (ACME) Protocol?What is the Automated Certificate Management Environment (ACME) Protocol? kdobieski Fri, 08/12/2022 - 17:00 4104 views How does...
US Unmasks Suspected Conti Ransomware Actor
US Unmasks Suspected Conti Ransomware ActorState Department offers $10m reward for info on notorious groupLeer másState Department offers $10m reward for info on notorious group
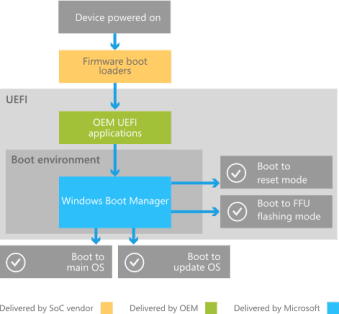
New exploits can bypass Secure Boot and modern UEFI security protections
New exploits can bypass Secure Boot and modern UEFI security protectionsTwo teams of researchers have revealed vulnerabilities this week in Unified Extensible Firmware Interface (UEFI) implementations...
#BHUSA: What has Changed in the Post-Stuxnet Era?
#BHUSA: What has Changed in the Post-Stuxnet Era?Investigative journalist Kim Zetter explains that Stuxnet continues to serves as a precedent for attacks happening nowLeer másInvestigative journalist...
#BHUSA: Bug Bounty Botox – Why You Need a Security Process First
#BHUSA: Bug Bounty Botox – Why You Need a Security Process FirstKatie Moussouris explains why simply having a bug bounty program isn't enough to fix security...
Facebook’s In-app Browser on iOS Tracks ‘Anything You Do on Any Website’
Facebook’s In-app Browser on iOS Tracks ‘Anything You Do on Any Website’Researcher shows how Instagram and Facebook’s use of an in-app browser within both its iOS...
Safety first: how to tweak the settings on your dating apps
Safety first: how to tweak the settings on your dating appsTinder, Bumble or Grindr - popular dating apps depend heavily on your location, personal data, and...
Feds: Zeppelin Ransomware Resurfaces with New Compromise, Encryption Tactics
Feds: Zeppelin Ransomware Resurfaces with New Compromise, Encryption TacticsThe CISA has seen a resurgence of the malware targeting a range of verticals and critical infrastructure organizations...
Black Hat 2022‑ Cyberdefense in a global threats era
Black Hat 2022‑ Cyberdefense in a global threats eraOur Security evangelist's take on this first day of Black Hat 2022, where cyberdefense was on every mind....
#BHUSA: Failure to Challenge is a Social Engineering Risk
#BHUSA: Failure to Challenge is a Social Engineering RiskThe UK Ministry of Defence is actively training staff to confront individuals that are engaged in risky behavioursLeer...
SolidBit Ransomware Group Recruiting New Affiliates on Dark Web
SolidBit Ransomware Group Recruiting New Affiliates on Dark Web20% of the earned profit from the distribution of the ransomware will be paid to the affiliatesLeer más20%...
The potential consequences of data breach, and romance scams – Week in security with Tony Anscombe
The potential consequences of data breach, and romance scams – Week in security with Tony AnscombeThe NHS was victim of a potential cyberattack, which raises the...
Meta Tests Encrypted Backups and End-to-End Encryption in Facebook Messenger
Meta Tests Encrypted Backups and End-to-End Encryption in Facebook MessengerMeta is also introducing an encrypted backup feature called Secure StorageLeer másMeta is also introducing an encrypted...
The US offers a $10M rewards for info on the Conti ransomware gang’s members
The US offers a $10M rewards for info on the Conti ransomware gang’s membersThe U.S. State Department announced a $10 million reward for information related to five individuals...
Three flaws allow attackers to bypass UEFI Secure Boot feature
Three flaws allow attackers to bypass UEFI Secure Boot featureResearchers discovered a flaw in three signed third-party UEFI boot loaders that allow bypass of the UEFI...
Weekly Update 308
Weekly Update 308It was all a bit last minute today after travel, office works and then a quick rebuild of desk and PC before doing this...
The Most Relevant Ransomware Statistics and Facts of 2022
The Most Relevant Ransomware Statistics and Facts of 2022The state of ransomware remains, more or less, unchanged; my choice of words would be unchallenged. For the...
Armageddon APT aka UAC-0010 Uses GammaLoad and GammaSteel Malware in Targeted Cyber-Attacks on Ukraine
Armageddon APT aka UAC-0010 Uses GammaLoad and GammaSteel Malware in Targeted Cyber-Attacks on Ukraine With the outbreak of the global cyber war, the malicious activity of...
Ransomware attack blamed for closure of all 7-Eleven stores in Denmark
Ransomware attack blamed for closure of all 7-Eleven stores in DenmarkRansomware is to blame for the closure of all 175 7-Eleven stores in Denmark on Monday....
Twitter Exposes Personal Information for 5.4 Million Accounts
Twitter Exposes Personal Information for 5.4 Million AccountsTwitter accidentally exposed the personal information—including phone numbers and email addresses—for 5.4 million accounts. And someone was trying to...
A Taxonomy of Access Control
A Taxonomy of Access ControlMy personal definition of a brilliant idea is one that is immediately obvious once it’s explained, but no one has thought of...
Friday Squid Blogging: SQUID Acronym for Making Conscious Choices
Friday Squid Blogging: SQUID Acronym for Making Conscious ChoicesI think the U is forced: SQUID consists of five steps: Stop, Question, Understand, Imagine, and Decide. As...
Sounding the Alarm on Emergency Alert System Flaws
Sounding the Alarm on Emergency Alert System FlawsThe Department of Homeland Security (DHS) is urging states and localities to beef up security around proprietary devices that...
Back to School: Tech Savvy vs. Cyber Savvy
Back to School: Tech Savvy vs. Cyber Savvy The first day of school is right around the corner. The whole family is gearing up for a...
Identity and Access Management at NIST: A Rich History and Dynamic Future
Identity and Access Management at NIST: A Rich History and Dynamic FutureDigital identity for access control is a fundamental and critical cybersecurity capability that ensures the...
Chinese hackers backdoor chat app with new Linux, macOS malware
Chinese hackers backdoor chat app with new Linux, macOS malwareVersions of a cross-platform instant messenger application focused on the Chinese market known as 'MiMi' have been...
Microsoft: We Don’t Want to Zero-Day Our Customers
Microsoft: We Don't Want to Zero-Day Our CustomersThe head of Microsoft's Security Response Center defends keeping its initial vulnerability disclosures sparse — it is, she says,...
Best penetration testing tools: 2022 buyer’s guide
Best penetration testing tools: 2022 buyer’s guideSecurity professionals need penetration testing tools to understand the security posture of every software environment. Check out our list of...