Security and Cheap ComplexityI’ve been saying that complexity is the worst enemy of security for a long time now. (Here’s me in 1999.) And it’s been...
Day: August 26, 2022
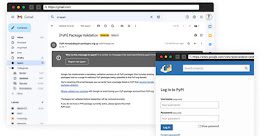
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing Attacks
PyPI Repository Warns Python Project Maintainers About Ongoing Phishing AttacksThe Python Package Index, PyPI, on Wednesday sounded the alarm about an ongoing phishing campaign that aims...
U.S. Government Spending Billions on Cybersecurity
U.S. Government Spending Billions on CybersecurityIn recent months, the House of Representatives has been hard at work drafting various spending bills for the 2023 fiscal year....
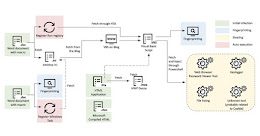
Researchers Uncover Kimusky Infra Targeting South Korean Politicians and Diplomats
Researchers Uncover Kimusky Infra Targeting South Korean Politicians and DiplomatsThe North Korean nation-state group Kimusky has been linked to a new set of malicious activities directed...
Cybercrime Groups Increasingly Adopting Sliver Command-and-Control Framework
Cybercrime Groups Increasingly Adopting Sliver Command-and-Control FrameworkNation-state threat actors are increasingly adopting and integrating the Sliver command-and-control (C2) framework in their intrusion campaigns as a replacement for Cobalt...
Okta Hackers Behind Twilio and Cloudflare Breach Hit Over 130 Organizations
Okta Hackers Behind Twilio and Cloudflare Breach Hit Over 130 OrganizationsThe threat actor behind the attacks on Twilio and Cloudflare earlier this month has been linked to a broader phishing...
Microsoft Uncovers New Post-Compromise Malware Used by Nobelium Hackers
Microsoft Uncovers New Post-Compromise Malware Used by Nobelium HackersThe threat actor behind the SolarWinds supply chain attack has been linked to yet another "highly targeted" post-exploitation...
Hackers Breach LastPass Developer System to Steal Source Code
Hackers Breach LastPass Developer System to Steal Source CodePassword management service LastPass confirmed a security incident that resulted in the theft of certain source code and...
Cybersecurity Insights with Contrast CISO David Lindner | 8/26
Cybersecurity Insights with Contrast CISO David Lindner | 8/26 Insight #1 " If you are struggling with the adoption of MFA across your organization, it’s time...
What I wish I knew about security when I started programming
What I wish I knew about security when I started programming It’s critical for developers to understand basic security concepts and best practices to build secure...
Insurers May Not Cover ‘State-Sponsored’ Cyberattacks
Insurers May Not Cover ‘State-Sponsored’ Cyberattacks Many of the more expensive cyberattacks and ransomware attacks, including the Solar Winds and Colonial Pipeline attacks, have been attributed...
Confidential Computing Beats Homomorphic Encryption for Data Security
Confidential Computing Beats Homomorphic Encryption for Data Security For the enterprise, data is like the air we breathe. At the same time, data seems to be...
Cybersecurity News Round-Up: Week of August 22, 2022
Cybersecurity News Round-Up: Week of August 22, 2022Twitter's Ex-CSO accuses the company of cybersecurity negligence, Hackers continue to attack hospitals and critical infrastructure The post Cybersecurity...
S3 Ep97: Did your iPhone get pwned? How would you know? [Audio + Text]
S3 Ep97: Did your iPhone get pwned? How would you know? [Audio + Text]Latest episode - listen now! (Or read the transcript if you prefer the...
Firefox 104 is out – no critical bugs, but update anyway
Firefox 104 is out – no critical bugs, but update anywayTwo trust-spoofing bugs were the main culprits this month - but neither one was a zero-day.Leer...
LastPass attackers steal source code, no evidence users’ passwords compromised
LastPass attackers steal source code, no evidence users’ passwords compromisedLastPass, the popular password manager used by millions of people around the world, has announced that it...
The 4 Best Open Source PKI Software Solutions (And Choosing the Right One)
The 4 Best Open Source PKI Software Solutions (And Choosing the Right One)In the never-ending battle between business success and cybersecurity threats, enterprises have discovered a...
TSA Requirements: A Snapshot of Growing Attention to Pipeline Cybersecurity
TSA Requirements: A Snapshot of Growing Attention to Pipeline CybersecurityThe post TSA Requirements: A Snapshot of Growing Attention to Pipeline Cybersecurity appeared first on Nozomi Networks....
What Is a TLS/SSL Port?
What Is a TLS/SSL Port?What Is a TLS/SSL Port? 97thfloor Fri, 08/26/2022 - 09:15 1 view What TCP Ports Are Used Most Frequently? Managing TLS/SSL...
DNS data indicates increased malicious domain activity, phishing toolkit reuse
DNS data indicates increased malicious domain activity, phishing toolkit reuseNew research from cybersecurity vendor Akamai has revealed that 12.3% of monitored devices communicated with domains associated...
Up to 35% more CVEs published so far this year compared to 2021
Up to 35% more CVEs published so far this year compared to 2021A new report from Trustwave SpiderLabs has revealed that the number of CVEs published...
What is doxing and how to protect yourself
What is doxing and how to protect yourselfDoxing can happen to anyone – here’s how you can reduce the odds that your personal information will be...
French hospital crippled by cyberattack – Week in security with Tony Anscombe
French hospital crippled by cyberattack – Week in security with Tony AnscombeAs another hospital falls victim to ransomware, Tony weighs in on the much-debated issue of...
Ransomware Attack Forces French Hospital to Transfer Patients to Other Facilities
Ransomware Attack Forces French Hospital to Transfer Patients to Other FacilitiesCenter Hospitalier Sud Francilien (CHSF), was the victim of a ransomware attack that forced the medical...
Iran-linked Mercury APT exploited Log4Shell in SysAid Apps for initial access
Iran-linked Mercury APT exploited Log4Shell in SysAid Apps for initial accessAn Iran-linked Mercury APT group exploited the Log4Shell vulnerability in SysAid applications for initial access to...
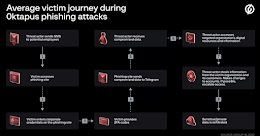
Massive “0ktapus” Phishing Attack Hits Over 130 Organizations
Massive “0ktapus” Phishing Attack Hits Over 130 OrganizationsOver 130 organizations were compromised in the “0ktapus” phishing campaign and the credential of 9,931 employees were stolen. Hackers...
Cyber EO One Year Later: Feds Weigh in On Progress, Areas For Improvement
Cyber EO One Year Later: Feds Weigh in On Progress, Areas For ImprovementBy Brittany Johnston, Research Director, MeriTalk In May 2021, President Biden issued the Executive...
Cyber Risk Management: The Right Approach Is a Business-Oriented Approach
Cyber Risk Management: The Right Approach Is a Business-Oriented ApproachBy Michael Maggio, CEO & Chief Product Officer of Reciprocity As rates of cyberattacks continue to increase...
LastPass hackers steal source code, no evidence of users’ passwords compromised
LastPass hackers steal source code, no evidence of users’ passwords compromisedLastPass, the popular password manager trusted by millions of people around the world, has announced that...
Man-in-the-Middle Phishing Attack
Man-in-the-Middle Phishing AttackHere’s a phishing campaign that uses a man-in-the-middle attack to defeat multi-factor authentication: Microsoft observed a campaign that inserted an attacker-controlled proxy site between...