Become a Cybersecurity Expert with 18 New Online Courses @ 98% OFFWith more data stored in the cloud than ever before, now is a good time...
Day: August 22, 2022
CISA Adds 7 New Actively Exploited Vulnerabilities to Catalog
CISA Adds 7 New Actively Exploited Vulnerabilities to CatalogThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday moved to add a critical SAP security flaw to its Known...
Hackers Stole Crypto from Bitcoin ATMs by Exploiting Zero-Day Vulnerability
Hackers Stole Crypto from Bitcoin ATMs by Exploiting Zero-Day VulnerabilityBitcoin ATM manufacturer General Bytes confirmed that it was a victim of a cyberattack that exploited a...
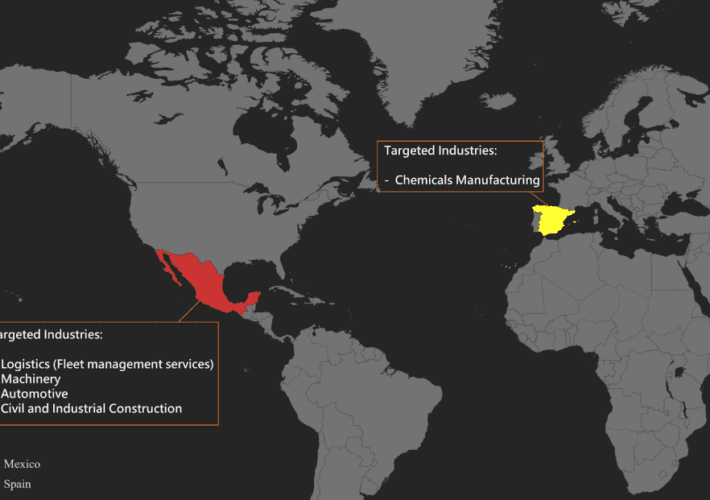
New Grandoreiro Banking Malware Campaign Targeting Spanish Manufacturers
New Grandoreiro Banking Malware Campaign Targeting Spanish ManufacturersOrganizations in the Spanish-speaking nations of Mexico and Spain are in the crosshairs of a new campaign designed to...
RTLS Systems Found Vulnerable to MiTM Attacks and Location Tampering
RTLS Systems Found Vulnerable to MiTM Attacks and Location TamperingResearchers have disclosed multiple vulnerabilities impacting Ultra-wideband (UWB) Real-time Locating Systems (RTLS), enabling threat actors to launch...
BSidesTLV 2022 – Gal Bitensky’s ‘SS-Oh No!’
BSidesTLV 2022 – Gal Bitensky’s ‘SS-Oh No!’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's YouTube channel. Permalink The post BSidesTLV 2022...
Hacktivism and DDOS Attacks Rise Dramatically in 2022
Hacktivism and DDOS Attacks Rise Dramatically in 20222022 has brought a surge in distributed denial-of-service attacks as well as a dramatic rise in patriotic hacktivism. What’s...
How to Mitigate Insider Threat Using Internal Controls
How to Mitigate Insider Threat Using Internal ControlsAs your company grows, you’ll want to reduce the chances for insider threat. Discover how internal controls can help...
BSidesTLV 2022 – Rotem Reiss’ ‘Code C.A.I.N – Keeping Your Source Code Under Control’
BSidesTLV 2022 – Rotem Reiss’ ‘Code C.A.I.N – Keeping Your Source Code Under Control’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's...
Vulnerability management – we’re doing it wrong
Vulnerability management – we’re doing it wrongSecurity professionals (and the people who measure our performance like auditors and regulators) have traditionally taken a stance that “all...
Robert M. Lee’s & Jeff Haas’ Little Bobby Comic – ‘WEEK 235’ (2019 Repost)
Robert M. Lee’s & Jeff Haas’ Little Bobby Comic – ‘WEEK 235’ (2019 Repost) via the respected security expertise of Robert M. Lee and the superlative...
BSidesTLV 2022 – Amichai’s And Stav Shulman’s ‘Now You C(&C), Now You Don’t’
BSidesTLV 2022 – Amichai’s And Stav Shulman’s ‘Now You C(&C), Now You Don’t’Our thanks to BSidesTLV for publishing their outstanding conference videos on the organization's YouTube...
Email and cybersecurity: Fraudsters are knocking
Email and cybersecurity: Fraudsters are knockingCan you remember your first email? Either sending one, or receiving it? I certainly remember explaining to people what email was,...
Multi-Factor Authentication Fatigue Attack, Signal Account Twilio Hack, Facebook and Instagram In-App Browser
Multi-Factor Authentication Fatigue Attack, Signal Account Twilio Hack, Facebook and Instagram In-App BrowserA Cisco employee was compromised by a ransomware gang using a technique called multi-factor...
More Password Cracking Tips: A Defcon 2022 Crack Me If You Can Roundup
More Password Cracking Tips: A Defcon 2022 Crack Me If You Can Roundup “We do not learn from experience... we learn from reflecting on experience.” -- John...
7 critical steps for successful security onboarding
7 critical steps for successful security onboardingJerich Beason, CISO, Commercial Bank at Capital One, equates the Great Resignation with the great onboarding. “If you are a...
6 best practices for blue team success
6 best practices for blue team successCybersecurity team conversations these days can feel like a rainbow, with mentions of red, blue and even purple teams. While...
Car Dealership Hit by Major Ransomware Attack
Car Dealership Hit by Major Ransomware AttackHoldcroft Motor Group says most systems back online nowLeer másHoldcroft Motor Group says most systems back online now
Hackers Target ATM Maker for Bitcoins
Hackers Target ATM Maker for BitcoinsGeneral Bytes confirms serious attack last weekLeer másGeneral Bytes confirms serious attack last week
DDoS Protection Weaponized to Deliver RATs
DDoS Protection Weaponized to Deliver RATsNew campaign disguised as fake Cloudflare pop-upLeer másNew campaign disguised as fake Cloudflare pop-up
CISA added 7 new flaws to its Known Exploited Vulnerabilities Catalog
CISA added 7 new flaws to its Known Exploited Vulnerabilities CatalogThe U.S. Cybersecurity and Infrastructure Security Agency (CISA) added 7 new flaws to its Known Exploited Vulnerabilities...
White hat hackers broadcasted talks and hacker movies through a decommissioned satellite
White hat hackers broadcasted talks and hacker movies through a decommissioned satelliteHackers took control of a decommissioned satellite and broadcasted hacking conference talks and hacker movies. ...
Security Affairs newsletter Round 380
Security Affairs newsletter Round 380A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in...
Grandoreiro banking malware targets Mexico and Spain
Grandoreiro banking malware targets Mexico and SpainA new Grandoreiro banking malware campaign is targeting organizations in Mexico and Spain, Zscaler reported. Zscaler ThreatLabz researchers observed a...
Threat actors are stealing funds from General Bytes Bitcoin ATM
Threat actors are stealing funds from General Bytes Bitcoin ATMThreat actors have exploited a zero-day vulnerability in the General Bytes Bitcoin ATM servers to steal BTC...
Fake DDoS protection pages on compromised WordPress sites lead to malware infections
Fake DDoS protection pages on compromised WordPress sites lead to malware infectionsThreat actors compromise WordPress sites to display fake Cloudflare DDoS protection pages to distribute malware. DDoS...
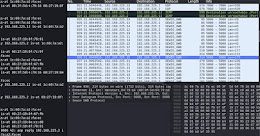
Donot Team cyberespionage group updates its Windows malware framework
Donot Team cyberespionage group updates its Windows malware frameworkThe Donot Team threat actor, aka APT-C-35, has added new capabilities to its Jaca Windows malware framework. The Donot Team has been...
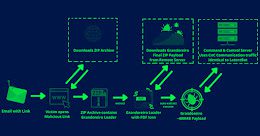
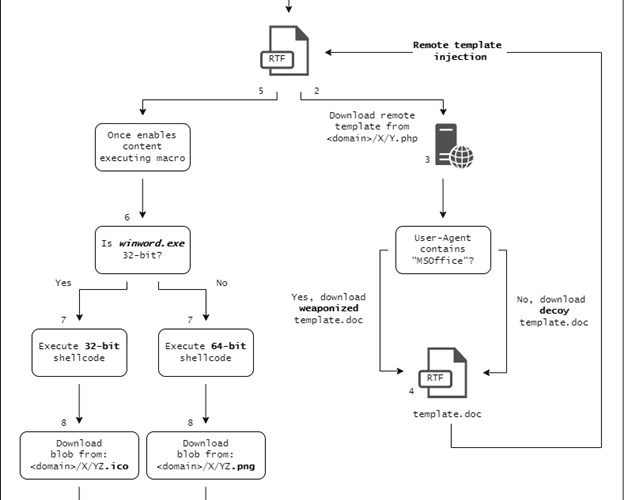
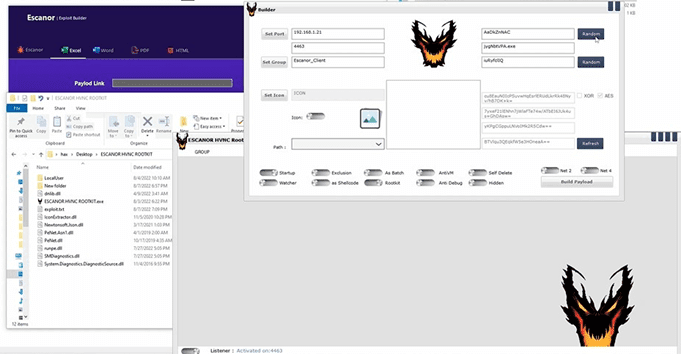
Escanor Malware delivered in Weaponized Microsoft Office Documents
Escanor Malware delivered in Weaponized Microsoft Office DocumentsResearchers spotted a new RAT (Remote Administration Tool) advertised in Dark Web and Telegram called Escanor Resecurity, a Los...
Zero-day Vulnerability Abused by Cybercriminals to Steal Crypto from Bitcoin ATMs
Zero-day Vulnerability Abused by Cybercriminals to Steal Crypto from Bitcoin ATMsMalicious actors have taken advantage of a zero-day flaw in General Bytes Bitcoin ATM servers to...
3 Ways Asset Management Companies Can Reduce Cyber Risk
3 Ways Asset Management Companies Can Reduce Cyber RiskFund managers should not get caught out thinking they are a low-priority target: here’s how to identify risks...