Estonia Repels Biggest Cyber-Attack Since 2007Tiny Baltic nation riles Russia by removing monumentsLeer másTiny Baltic nation riles Russia by removing monuments
Day: August 20, 2022
Businesses Found to Neglect Cybersecurity Until it is Too Late
Businesses Found to Neglect Cybersecurity Until it is Too LateThe UK government report found that many leaders only review cybersecurity practices following an incidentLeer másThe UK...
Xiaomi Phone Bug Allowed Payment Forgery
Xiaomi Phone Bug Allowed Payment ForgeryMobile transactions could’ve been disabled, created and signed by attackers.Leer másThreatpostMobile transactions could’ve been disabled, created and signed by attackers.
U.K. Water Supplier Hit with Clop Ransomware Attack
U.K. Water Supplier Hit with Clop Ransomware AttackThe incident disrupted corporate IT systems at one company while attackers misidentified the victim in a post on its...
Apple Warns of Critical Security Risk in Safari For iPhones, iPads and Macs
Apple Warns of Critical Security Risk in Safari For iPhones, iPads and MacsThe vulnerability gave hackers the ability to infiltrate WebKit, the engine that powers SafariLeer...
New Deep Instinct partner program targets MSSPs fighting ransomware
New Deep Instinct partner program targets MSSPs fighting ransomwareCybersecurity firm Deep Instinct has rolled out a new partner program to provide its endpoint and application protection...
Microsoft: Cryptojackers Continue to Evolve to Be Stealthier and Spread Faster
Microsoft: Cryptojackers Continue to Evolve to Be Stealthier and Spread FasterCryptojackers take advantage of legitimate system binaries on more than 200,000 devices dailyLeer másCryptojackers take advantage...
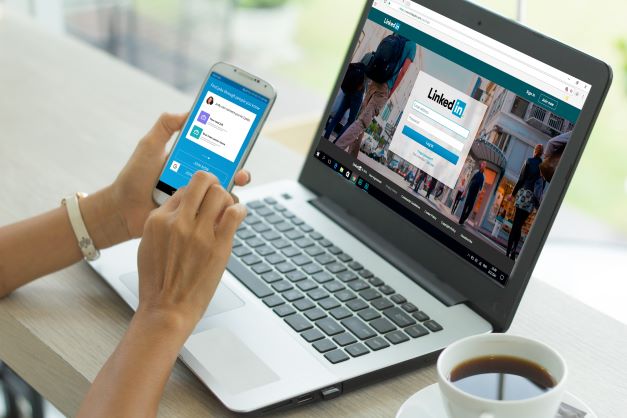
A step‑by‑step guide to enjoy LinkedIn safely
A step‑by‑step guide to enjoy LinkedIn safelyLinkedIn privacy settings are just as overwhelming as any other social media settings. There’s a lot of menus, a lot...
NIST CSF 2.0 Workshop emphasizes global appeal, metrics and assessment
NIST CSF 2.0 Workshop emphasizes global appeal, metrics and assessmentThe U.S. National Institute of Standards and Technology (NIST) hosted its first workshop yesterday on the Cybersecurity...
APT Lazarus Targets Engineers with macOS Malware
APT Lazarus Targets Engineers with macOS MalwareThe North Korean APT is using a fake job posting for Coinbase in a cyberespionage campaign targeting users of both...
China-backed APT41 Group Hacked at Least 13 Victims in 2021
China-backed APT41 Group Hacked at Least 13 Victims in 2021The majority of the attacks spotted relied primarily on SQL injections on targeted domainsLeer másThe majority of...
Google Cloud blocks largest HTTPS DDoS attack ever
Google Cloud blocks largest HTTPS DDoS attack everGoogle Cloud has claimed to have blocked the largest Layer 7 (HTTPS) DDoS attack to date after a Cloud...
Five things security pros want from CNAPP
Five things security pros want from CNAPPAccording to new research from ESG and the Information Systems Security Association (ISSA), 58% of organizations are consolidating or considering consolidating...
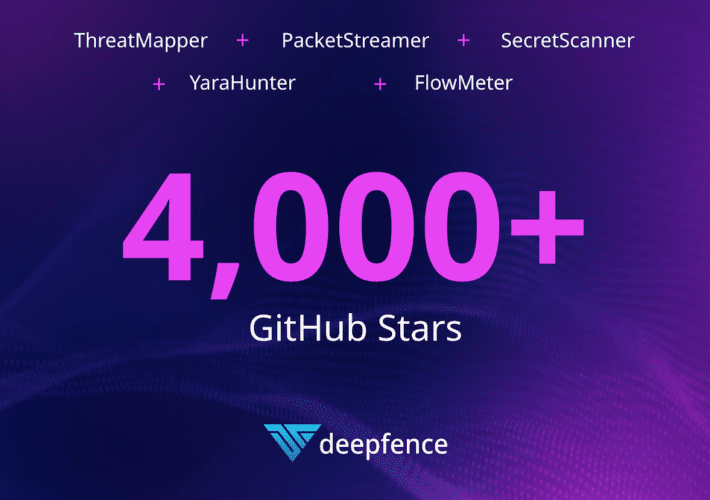
Deepfence Open Source Community Update – August 2022
Deepfence Open Source Community Update – August 2022We’ve seen some tremendous momentum since our last open source community update and are excited to share our most...
Understanding eBPF for API Security
Understanding eBPF for API Security Executive Summary API security is increasingly a top priority for security leaders and risk executives. eBPF has emerged as a potential...
BSidesTLV 2022 – Vera Mens’ ‘Total Flaw: Hacking Flow Computers For Fun And Free Gas’
BSidesTLV 2022 – Vera Mens’ ‘Total Flaw: Hacking Flow Computers For Fun And Free Gas’Our thanks to BSidesTLV for publishing their outstanding conference videos on the...
Black Hat Fireside Chat: Replacing VPNs with ZTNA that leverages WWII battlefield tactics
Black Hat Fireside Chat: Replacing VPNs with ZTNA that leverages WWII battlefield tacticsThe sunsetting of Virtual Private Networks is underway. Related: VPNs as a DIY tool...
Analysis of Clop’s Attack on South Staffordshire Water – UK
Analysis of Clop’s Attack on South Staffordshire Water – UKOn August 15, the Clop ransomware group announced on their leak website the breach of South Staffordshire...
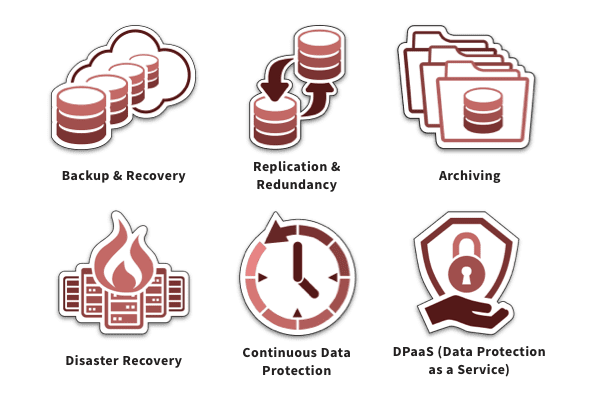
Data Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats
Data Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats “Data really powers everything that we do.” — Jeff Weiner, executive chairman of LinkedIn It...
Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio Hack
Nearly 1,900 Signal Messenger Accounts Potentially Compromised in Twilio HackPopular end-to-end encrypted messaging service Signal on Monday disclosed the cyberattack aimed at Twilio earlier this month...
Credential Theft Is (Still) A Top Attack Method
Credential Theft Is (Still) A Top Attack MethodCredential theft is clearly still a problem. Even after years of warnings, changing password requirements, and multiple forms of...
Microsoft Warns About Phishing Attacks by Russia-linked Hackers
Microsoft Warns About Phishing Attacks by Russia-linked HackersMicrosoft on Monday revealed it took steps to disrupt phishing operations undertaken by a "highly persistent threat actor" whose...
Russian State Hackers Continue to Attack Ukrainian Entities with Infostealer Malware
Russian State Hackers Continue to Attack Ukrainian Entities with Infostealer MalwareRussian state-sponsored actors are continuing to strike Ukrainian entities with information-stealing malware as part of what's...
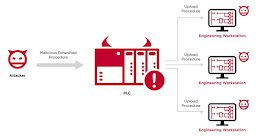
New Evil PLC Attack Weaponizes PLCs to Breach OT and Enterprise Networks
New Evil PLC Attack Weaponizes PLCs to Breach OT and Enterprise NetworksCybersecurity researchers have elaborated a novel attack technique that weaponizes programmable logic controllers (PLCs) to...
Friday Squid Blogging: The Language of the Jumbo Flying Squid
Friday Squid Blogging: The Language of the Jumbo Flying SquidThe jumbo flying squid (Dosidicus gigas) uses its color-changing ability as a language: In 2020, however, marine...
Unified Threat Management: The All-in-One Cybersecurity Solution
Unified Threat Management: The All-in-One Cybersecurity SolutionUTM (Unified threat management) is thought to be an all-in-one solution for cybersecurity. In general, it is a versatile software...
North Korea Hackers Spotted Targeting Job Seekers with macOS Malware
North Korea Hackers Spotted Targeting Job Seekers with macOS MalwareThe North Korea-backed Lazarus Group has been observed targeting job seekers with malware capable of executing on...
RubyGems Makes Multi-Factor Authentication Mandatory for Top Package Maintainers
RubyGems Makes Multi-Factor Authentication Mandatory for Top Package MaintainersRubyGems, the official package manager for the Ruby programming language, has become the latest platform to mandate multi-factor...
Malicious Browser Extensions Targeted Over a Million Users So Far This Year
Malicious Browser Extensions Targeted Over a Million Users So Far This YearMore than 1.31 million users attempted to install malicious or unwanted web browser extensions at...
July Tesla Sales Crashed in Germany and Norway: Not Even on Chart
July Tesla Sales Crashed in Germany and Norway: Not Even on ChartLooking at July I was at first surprised by German news about Fiat having a...