Encrypted Messaging Service Hack Exposes Phone Numbers Many people opt for encrypted messaging services because they like the additional layers of privacy they offer. They allow...
Day: August 20, 2022
Heimdal® Is a Finalist at the Computing Security Awards 2022 in Eight Categories
Heimdal® Is a Finalist at the Computing Security Awards 2022 in Eight CategoriesWe are thrilled to announce that Heimdal®’s cybersecurity solutions were selected as finalists for...
Data breaches on gaming sites are becoming more common
Data breaches on gaming sites are becoming more commonWith a number of gaming sites falling victim to data breaches in July of this year, CS Hub...
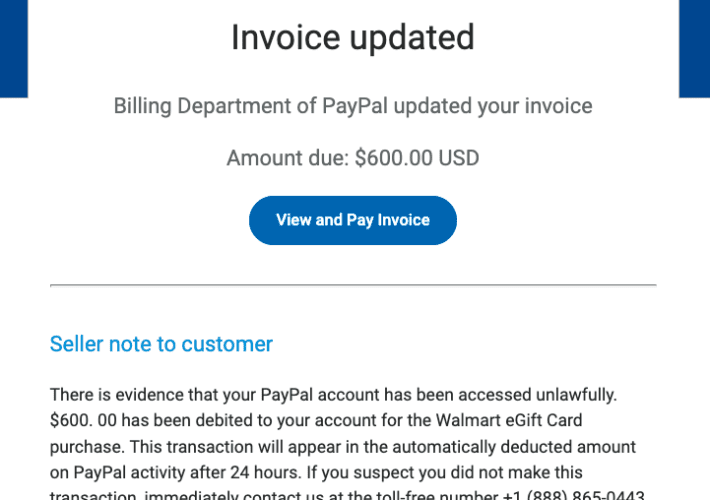
PayPal Phishing Scam Uses Invoices Sent Via PayPal
PayPal Phishing Scam Uses Invoices Sent Via PayPalScammers are using invoices sent through PayPal.com to trick recipients into calling a number to dispute a pending charge....
USB “Rubber Ducky” Attack Tool
USB “Rubber Ducky” Attack ToolThe USB Rubber Ducky is getting better and better. Already, previous versions of the Rubber Ducky could carry out attacks like creating...
Friday Squid Blogging: The Language of the Jumbo Flying Squid
Friday Squid Blogging: The Language of the Jumbo Flying SquidThe jumbo flying squid (Dosidicus gigas) uses its color-changing ability as a language: In 2020, however, marine...
BlackByte ransomware v2 is out with new extortion novelties
BlackByte ransomware v2 is out with new extortion noveltiesA new version of the BlackByte ransomware appeared in the threat landscape, version 2.0 uses extortion techniques similar to...
Entrust Allegedly Hit with LockBit Ransomware
Entrust Allegedly Hit with LockBit RansomwareThe LockBit ransomware group has declared that it was behind the American software company Entrust incident that occurred in June. At...
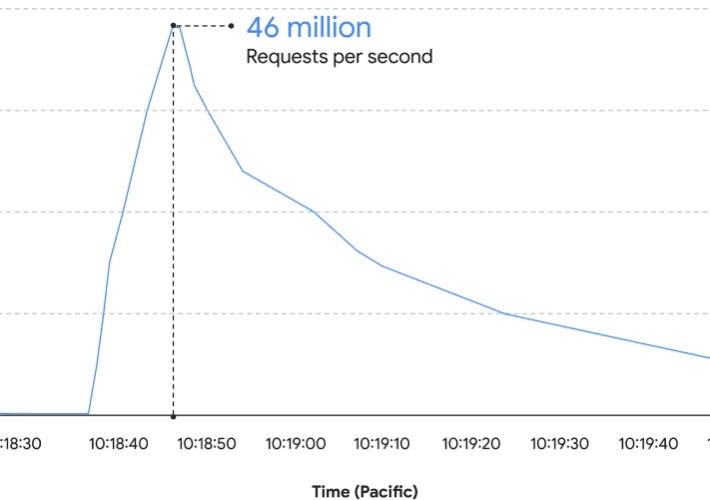
Google blocked the largest Layer 7 DDoS reported to date
Google blocked the largest Layer 7 DDoS reported to dateGoogle announced to have blocked the largest ever HTTPs DDoS attack, which reached 46 million requests per...
Safari 15.6.1 addresses a zero-day flaw actively exploited in the wild
Safari 15.6.1 addresses a zero-day flaw actively exploited in the wildApple released Safari 15.6.1 for macOS Big Sur and Catalina to address a zero-day vulnerability actively...
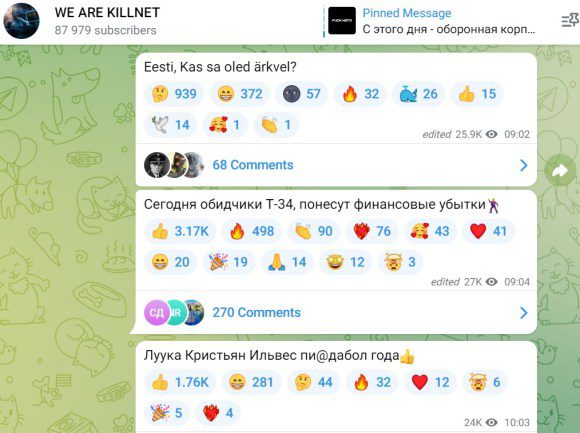
Estonia blocked cyberattacks claimed by Pro-Russia Killnet group
Estonia blocked cyberattacks claimed by Pro-Russia Killnet groupEstonia announced to have blocked a wave of cyber attacks conducted by Russian hackers against local institutions. Undersecretary for...
Cisco fixes High-Severity bug in Secure Web Appliance
Cisco fixes High-Severity bug in Secure Web ApplianceCisco addressed a high-severity escalation of privilege vulnerability (CVE-2022-20871) in AsyncOS for Cisco Secure Web Appliance. Cisco Secure Web Appliance (formerly Secure Web Appliance (WSA)) offers protection...
Zero Trust: Security Model for A Fluid Perimeter
Zero Trust: Security Model for A Fluid PerimeterBy Debanjali Ghosh, Technical Evangelist, ManageEngine The concept of a network being fully enclosed within a building, and […]...
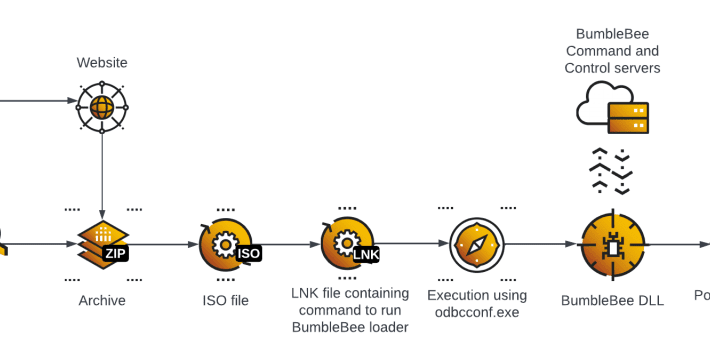
Bumblebee attacks, from initial access to the compromise of Active Directory Services
Bumblebee attacks, from initial access to the compromise of Active Directory ServicesThreat actors are using the Bumblebee loader to compromise Active Directory services as part of...
A flaw in Amazon Ring could expose user’s camera recordings
A flaw in Amazon Ring could expose user’s camera recordingsAmazon addressed a high-severity flaw in its Ring app for Android that could have exposed sensitive information...
Russia-linked Cozy Bear uses evasive techniques to target Microsoft 365 users
Russia-linked Cozy Bear uses evasive techniques to target Microsoft 365 usersRussia-linked APT group Cozy Bear continues to target Microsoft 365 accounts in NATO countries for cyberespionage...
Weekly Update 309
Weekly Update 309Right off the back of a visit to our wedding venue (4 weeks and counting!) and a few hours before heading to the snow...
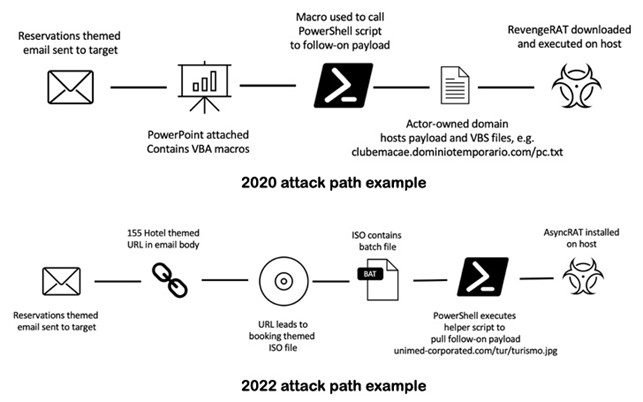
TA558 cybercrime group targets hospitality and travel orgs
TA558 cybercrime group targets hospitality and travel orgsTA558 cybercrime group is behind a malware campaign targeting hospitality, hotel, and travel organizations in Latin America Researchers from Proofpoint...
Threat Group Ramps-Up Attacks on Travel Sector in 2022
Threat Group Ramps-Up Attacks on Travel Sector in 2022Corporate and customer data at risk, warns ProofpointLeer másCorporate and customer data at risk, warns Proofpoint
Exposed VNC instances threatens critical infrastructure as attacks spike
Exposed VNC instances threatens critical infrastructure as attacks spikeNew research from threat intelligence and cybersecurity company Cyble has identified a peak in attacks targeting virtual network...
Quarter of All Gambling Sites Hit by DDoS Attacks in June
Quarter of All Gambling Sites Hit by DDoS Attacks in JuneThe attacks reportedly increased in conjunction with the start of the Wimbledon tennis tournamentLeer másThe attacks...
Safe Security debuts two free risk assessment tools for businesses
Safe Security debuts two free risk assessment tools for businessesCybersecurity risk assessment company Safe Security on Tuesday rolled out two new online risk assessment tools for...
“Evil PLC Attack” weaponizes PLCs to infect engineering workstations
"Evil PLC Attack" weaponizes PLCs to infect engineering workstationsMost attack scenarios against industrial installations, whether in manufacturing or in critical infrastructure, focus on compromising programmable logic...
ATMZOW JS Sniffer Campaign Linked to Hancitor Malware
ATMZOW JS Sniffer Campaign Linked to Hancitor MalwareATMZOW infected at least 483 websites across four continents since the beginning of 2019Leer másATMZOW infected at least 483...
Hackers Deploy Bumblebee Loader to Breach Target Networks
Hackers Deploy Bumblebee Loader to Breach Target NetworksMost Bumblebee infections started by end-users executing LNK filesLeer másMost Bumblebee infections started by end-users executing LNK files
Ransomware safeguards for small- to medium-sized businesses
Ransomware safeguards for small- to medium-sized businessesThe Institute for Security and Technology (IST) recently released a “Blueprint for Ransomware Defense.” The guide includes recommendations of defensive...
Cyber Tops Staff Retention as Biggest Business Risk
Cyber Tops Staff Retention as Biggest Business RiskPwC report finds execs are paying more attention to risk managementLeer másPwC report finds execs are paying more attention...
What is zk-SNARK?
What is zk-SNARK?Zk-SNARK, which stands for zero-knowledge succinct non-interactive argument or knowledge, is the most popular zero-knowledge protocol. This a space of increasing importance, as zero...
Google updates Chronicle with enhanced threat detection
Google updates Chronicle with enhanced threat detectionGoogle Cloud Wednesday announced the general availability of what it calls “curated detection” for its Chronicle security analysis platform. The...
UK Carrier Claims to Block One Million Vishing Calls Per Day
UK Carrier Claims to Block One Million Vishing Calls Per DayEE says AI tech is stopping international scamsLeer másEE says AI tech is stopping international scams