OPSWAT Presents New Malware Analysis Capabilities for Operational Technology at Black Hat USA 2022Product enhancements to offer full IT and OT threat intelligence services for OPSWAT...
Day: August 11, 2022
Three Sentenced for Operating the "Reboot” Store on Hydra
Three Sentenced for Operating the "Reboot” Store on HydraThree drug dealers were sentenced to prison in Russia for operating a store on the Hydra darkweb marketplace....
Mimecast Announces Mimecast X1™ Platform Providing Customers With Email and Collaboration Security
Mimecast Announces Mimecast X1™ Platform Providing Customers With Email and Collaboration SecurityPlatform engineered to let organizations mitigate risk and manage complexities.Leer másDark ReadingPlatform engineered to let...
GUEST ESSAY: How to detect if a remote job applicant is legit — or a ‘Deepfake’ candidate
GUEST ESSAY: How to detect if a remote job applicant is legit — or a ‘Deepfake’ candidateTechnology provides opportunities to positively impact the world and improve...
Rethinking Software in the Organizational Hierarchy
Rethinking Software in the Organizational HierarchyLeast privilege is a good defense normally applied only to users. What if we limited apps' access to other apps and...
Many ZTNA, MFA Tools Offer Little Protection Against Cookie Session Hijacking Attacks
Many ZTNA, MFA Tools Offer Little Protection Against Cookie Session Hijacking AttacksMany of the technologies and services that organizations are using to isolate Internet traffic from...
VMware Announces Advanced Workload Security for AWS
VMware Announces Advanced Workload Security for AWSPublic Cloud Introduces Unique Security Challenges As cloud adoption continues to grow, it is no surprise that in the last...
VMware Announces Advanced Workload Security for AWS
VMware Announces Advanced Workload Security for AWSPublic Cloud Introduces Unique Security Challenges As cloud adoption continues to grow, it is no surprise that in the last...
VMware Explore 2022 US – The Security Mindset: Changing the Way You Think About Enterprise Security
VMware Explore 2022 US – The Security Mindset: Changing the Way You Think About Enterprise SecurityPeople are at the heart of the modern IT organization. People...
VMware Explore 2022 US – The Security Mindset: Changing the Way You Think About Enterprise Security
VMware Explore 2022 US – The Security Mindset: Changing the Way You Think About Enterprise SecurityPeople are at the heart of the modern IT organization. People...
Deepfake Attacks and Cyber Extortion are the Focus of New VMware Report
Deepfake Attacks and Cyber Extortion are the Focus of New VMware ReportOn day one of Black Hat USA 2022, we at VMware published our eighth annual...
Deepfake Attacks and Cyber Extortion are the Focus of New VMware Report
Deepfake Attacks and Cyber Extortion are the Focus of New VMware ReportOn day one of Black Hat USA 2022, we at VMware published our eighth annual...
Sales Director – Federal (US)
Sales Director – Federal (US)Our Perfect Candidate You are a self-starter with strong attention to detail and the ability to work in a fast-paced environment. You...
Sales Director – Government (US)
Sales Director – Government (US)Our Perfect Candidate You are a self-starter with strong attention to detail and the ability to work in a fast-paced environment. You...
How To Get Your Head Around Your Kids’ Online Gaming Life
How To Get Your Head Around Your Kids’ Online Gaming Life Let’s be honest – many of us parents aren’t big fans of gaming. In fact,...
SOC Prime Announces the Appointment of New Chief Operating Officer to Strengthen Its Executive Team
SOC Prime Announces the Appointment of New Chief Operating Officer to Strengthen Its Executive Team SOC Prime, Inc., provider of the world’s largest and most advanced...
More Dangers of Cyberbullying Emerge—Our Latest Connected Family Report
More Dangers of Cyberbullying Emerge—Our Latest Connected Family Report Earlier this year, our global Connected Family Study revealed the online habits of parents and their children....
CVE-2022-30333 Detection: New Security Hole in the UnRAR Utility
CVE-2022-30333 Detection: New Security Hole in the UnRAR Utility The US Critical Infrastructure Security Agency (CISA) expands its catalog of Known Exploited Vulnerabilities by documenting several...
The Security Pros and Cons of Using Email Aliases
The Security Pros and Cons of Using Email AliasesOne way to tame your email inbox is to get in the habit of using unique email aliases...
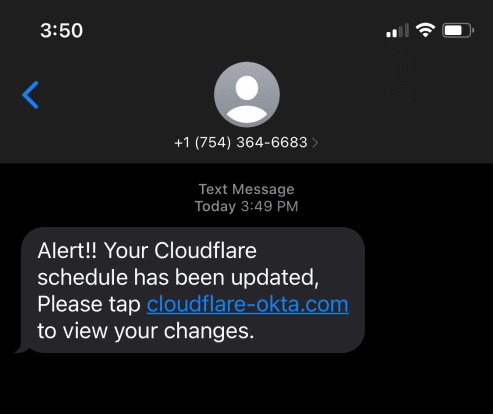
Hackers behind Twilio data breach also targeted Cloudflare employees
Hackers behind Twilio data breach also targeted Cloudflare employeesCloudflare revealed that at least 76 employees and their family members were targeted by smishing attacks similar to...
Experts found 10 malicious packages on PyPI used to steal developers’ data
Experts found 10 malicious packages on PyPI used to steal developers’ data10 packages have been removed from the Python Package Index (PyPI) because they were found...
Cisco was hacked by the Yanluowang ransomware gang
Cisco was hacked by the Yanluowang ransomware gangCisco discloses a security breach, the Yanluowang ransomware group breached its corporate network in late May and stole internal...
Risky Business: Enterprises Can’t Shake Log4j flaw
Risky Business: Enterprises Can’t Shake Log4j flaw70% of Large enterprises that previously addressed the Log4j flaw are still struggling to patch Log4j-vulnerable assets. INTRODUCTION In December...
Cisco fixed a flaw in ASA, FTD devices that can give access to RSA private key
Cisco fixed a flaw in ASA, FTD devices that can give access to RSA private keyCisco addressed a high severity flaw, tracked as CVE-2022-20866, affecting Adaptive...
Ex Twitter employee found guilty of spying for Saudi Arabian government
Ex Twitter employee found guilty of spying for Saudi Arabian governmentA former Twitter employee was found guilty of spying on certain Twitter users for Saudi Arabia....
Cisco Event Response: Corporate Network Security Incident
Cisco Event Response: Corporate Network Security IncidentContenido de la entradaLeer másCisco Event Responses
Emotet Tops List of July’s Most Widely Used Malware
Emotet Tops List of July's Most Widely Used MalwareThe Emotet botnet continues to evolve and now includes a credit card stealer moduleLeer másThe Emotet botnet continues...
Chinese APT group uses multiple backdoors in attacks on military and research organizations
Chinese APT group uses multiple backdoors in attacks on military and research organizationsSince early this year, a known APT group of Chinese origin has been targeting...
Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP Reports
Cyber-criminals Shift From Macros to Shortcut Files to Hack Business PCs, HP ReportsThe report shows an 11% rise in archive files containing malware, including LNK filesLeer...
DeathStalker’s VileRAT Continues to Target Foreign and Crypto Exchanges
DeathStalker's VileRAT Continues to Target Foreign and Crypto ExchangesThe campaign is not only ongoing, the threat actors increased its efforts to compromise targets using VileRATLeer másThe...