Source: heimdalsecurity.com – Author: Livia Gyongyoși
A jump server is a computer that acts as a safe bridge between networks in different security zones. It’s a hardened device that administrators use to safely bypass firewalls that isolate public networks from private ones. Another name for a jump server is a jump box or jump host.
By using a jump server, a System Administrator can safely manage access to an internal or private network from an external network. For example, they can use it to set up web or email servers in a DMZ from their workstation on a private VLAN.
A DMZ (Demilitarized Zone) is a separate network that acts as a buffer between an organization’s internal network and the public internet. DMZs host public-facing services, like websites and email servers. If hackers compromise an email account or a website, running web and email servers in a DMZ will prevent them from infecting the internal network too.
A VLAN (Virtual Local Area Network) allows network segmentation without needing separate hardware. Network admins use it to manage which devices and servers can communicate directly. This practice helps reduce the attack surface.
Key takeaways
- jump servers are attractive targets for hackers
- apply patches and other security best practices to keep jump servers safe
- never keep sensitive data on a jump server
- jump servers don’t replace privileged access management tools
How does a jump server work?
A jump server acts like a security gatekeeper between the internet and a more protected internal network. It’s the first stop for anyone trying to access an internal network from outside.
Before accessing a network in a different security zone, the user must authenticate. Best practices require using multi-factor authentication.
After that, the user can connect to internal resources, while the jump server keeps a close watch. One of its functions is to log all activity. The jump server also enforces tight security rules to restrict what users can do and see.
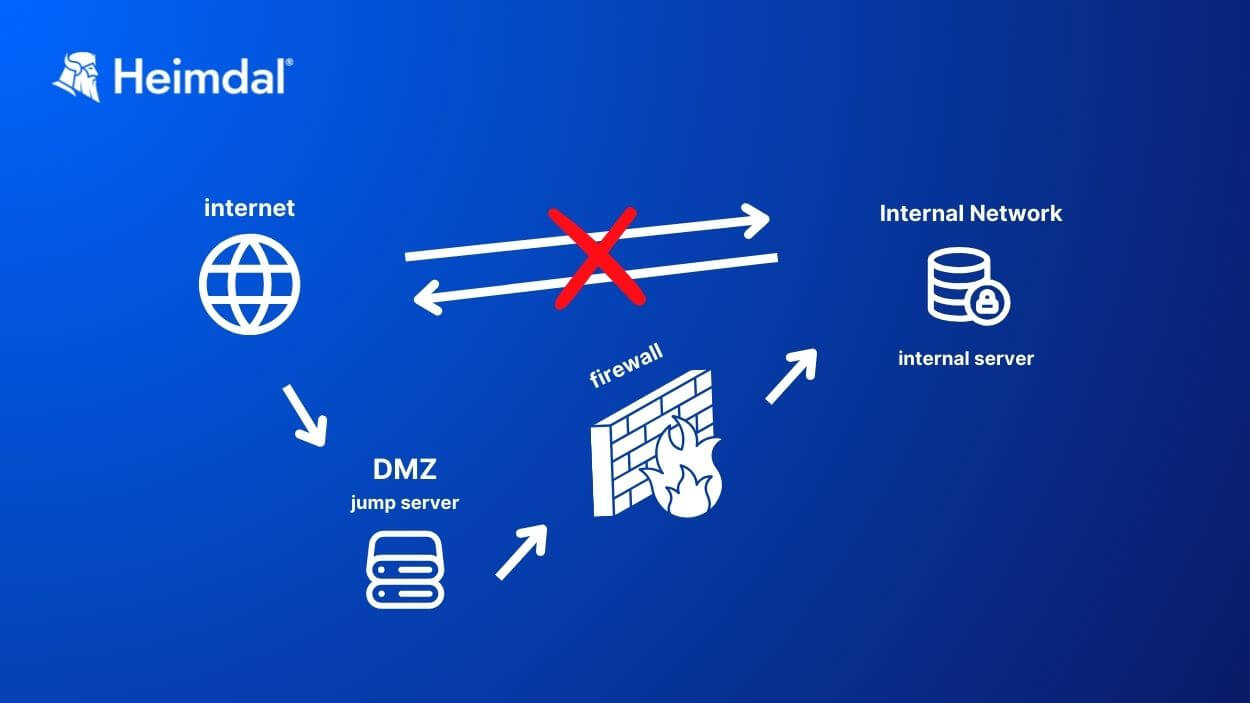
This configuration helps keep the internal network safe from external threats by controlling access and monitoring interactions. Think of a jump server like the bouncer at the door. It checks IDs and keeps an eye on things to make sure everything inside stays secure.
How to set a jump server
Setting up a jump server involves several key steps and security best practices. Since it is a secure gateway to your network, you want to make sure you configured it properly. Here’s how you do it:
Choose between hardware or a virtual environment
Depending on your needs, you can set up the jump server on a physical device or within a virtual machine (VM). In most cases, VMs offer enough capability and easier scalability.
Install the Operating System (OS)
Linux and Windows are the two main OS options. Linux is usually credited as safer in front of malware. Most network admins use it for their administrative environment. But in the end, it all depends on your needs.
Linux is your best choice if you need command line access only. One of its benefits is you’ll be able to use various open-source tools for implementing MFA.
On the other hand, you might need to run Windows applications or access other Windows machines. In that case, using Windows will make things more straightforward.
Configure network settings
Place the jump server in a demilitarized zone (DMZ) if possible. A DMZ sits between your internal network and the internet. A jump server should have two network interfaces: one facing the Internet and one facing the internal network.
Install a remote connectivity protocol
Depending on which OS you choose, install one of the two main protocols that enable network connection to and from jump servers
- SSH (Secure Shell), usually for Linux – uses TCP port 22
- RDP (Remote Desktop Protocol) for Windows – uses TCP port 3389. Remote Desktop Protocol has a GUI for remote systems and comes with default encryption for administrator connections.
Harden the jump server’s security
Jump servers are a target for hackers, just like VPNs. They are not safe unless you keep them safe. To bolster defense, follow these cybersecurity best practices:
Enable multi-factor authentication
One of the jump servers’ main advantages is that they require user authentication. The safest bet is to install a multi-factor authentication (MFA) system.
The Cybersecurity & Infrastructure Security Agency (CISA) repeatedly advised enabling MFA to bolster security:
Using Multi-Factor Authentication (MFA) is a powerful way to protect yourself and your organization. The use of MFA on your accounts makes you 99% less likely to be hacked.
Source – CISA advisory on cybersecurity best practices
Use Google Authenticator or hardware tokens for example.
Apply patches
Keep the server safe by closing known vulnerabilities. Use an automated patch management solution to apply patches and updates in time.
Enforce the principle of least functionality
Only install the software the jump server needs to perform its main job. Disable all other services and close unused ports. There’s no such thing as vulnerability-proof software. So, less software means fewer potential vulnerabilities in your system. The same goes for ports. Closing unused ports lowers the chances that your jump server falls victim to a port scan attack.
Use the jump server for one task only: safely connecting to remote networks. Don’t store sensitive data on it, like:
- user files
- configuration file backups
- databases
Configure access controls and permissions
Set up access controls to define what authenticated users can do. Go by the principle of the least privilege. Only allow the privileges that the user needs for accomplishing their tasks. Restrict any other commands. If you owned a hotel, you wouldn’t give a guest the keys to every room or the administrative spaces, would you?
Applying the principle of the least privilege reduces the risk of insider threat, lateral movement, or privilege escalation in case hackers compromise a user account.
To save time and increase security, use a privileged access management tool. It will allow and revoke permissions in time and to the right people.
Enable logging and monitoring
Configure logging to record all sessions happening through the jump server. You need this for auditing and monitoring, so you can detect and track in time any suspicious behavior.
Test the jump server’s configuration
Just like with other cybersecurity processes, test before going live. Make sure everything works as you want it to and that the security measures are in place.
Jump servers vs VPNs. Which one’s safer?
Jump servers and Virtual Private Networks (VPNs) are both common methods for secure remote access.
While jump servers work like intermediary points between users and target systems, VPNs create encrypted tunnels between a user’s device and the target network.
Hackers target jump servers and VPNs alike, so none is safe unless you configure it properly.
Virtual Private Networks (VPNs) and Remote Desktops / Jump servers frequently have a significant attacker opportunity as they are exposed to the internet to provide remote access and the maintenance of these systems is frequently neglected. While they only have a few network ports exposed, attackers only need access to one unpatched service for an attack.
John Flores, Technical Writer at Microsoft
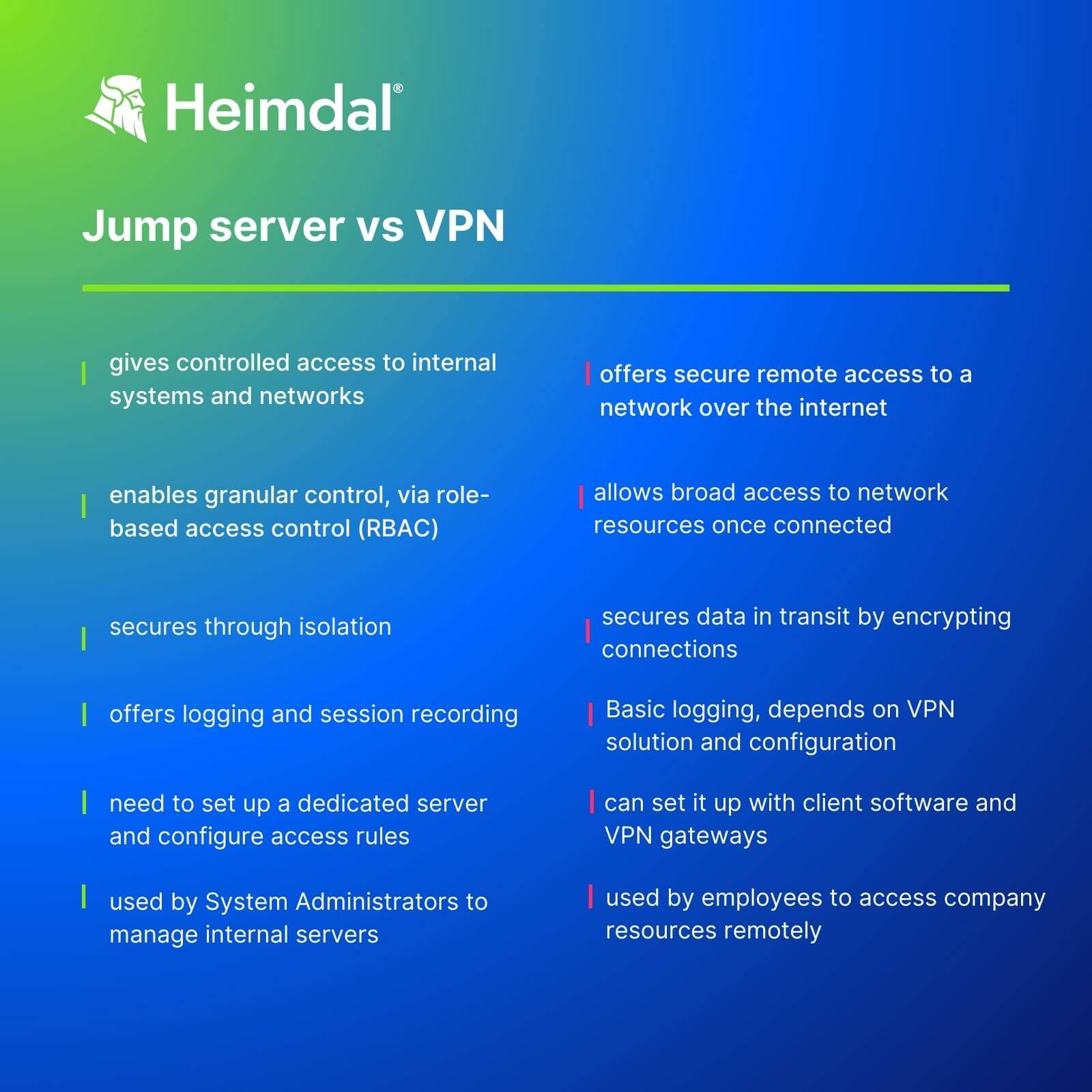
VPNs and jump servers are not stand-alone security tools, but part of a system. So, no matter which one you choose, you’ll still need to take additional safety measures to avoid security risks.
However, using a jump server forces you to authenticate twice:
- to the jump server
- to the target system
This double authentication process adds a layer of security to jump servers compared to VPNs. But there’s more to deciding which one to use. Here are some pros and cons for each method.
Jump server Pros
- requires user authentication before it grants access to other security zones and servers
- helps IT teams manage and monitor activities on servers and user endpoints easier, from a single control center
- offers activity logging and auditing capabilities
- reduces the attack surface by limiting access to sensitive data
Jump server Cons
- if hackers manage to gain access to a jump server, they’ll get to all the other devices on the remote network
- requires continuous maintenance to avoid security risks
- limited scalability
VPN Pros
- a VPN is easier to setup, as it works like a tunnel through the connection
- secures remote access by encrypting the users’ connections
- allows connecting to the network from various places and devices
VPN Cons
- enables access to any device or server, regardless of privilege level, once a user authenticates. A compromised device using a VPN to access another system could further spread the malware
- if misconfigured, a VPN can pose security risks
System admins waste 30% of their time manually managing user
rights or installations
Heimdal® Privileged Access
Management
Is the automatic PAM solution that makes everything
easier.
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
How to secure privileged accounts and sessions with Heimdal®
A jump server enhances overall security by authenticating those who request access to more sensitive areas of your network. However, it does not grant or track permissions and privileges. Also, a jump server is not a security tool.
Heimdal’s Privileged Account and Session Management (PASM) enables your IT team to:
- safeguard critical credentials with a minimal effort, by using Heimdal PASM’s Enterprise Credential Vault and Multi-Factor Authentication
- get safe, 1-click-direct access to remote servers without plugins, or additional software
- grant user privileges according to customized user role, thus avoiding over-privileged account risks
- benefit a just-in-time access request system which makes sure everybody gets the needed permissions for the necessary amount of time
- get real-time session monitoring for audit, compliance, and forensic activities
Conclusion
A jump server helps safeguard sensitive data by restricting access to the company’s private network. As long as you configure it with security in mind, it’s a safe and useful tool.
Hackers know that compromising a jump server means gaining the key to a company’s most treasured assets. So, yes, they’ll target jump servers in their attacks.
As always, securing the IT infrastructure is a matter of layers. To make access to critical data and infrastructure safer:
- use a just-in-time access system
- apply the principle of least privilege
- enforce a zero-trust policy
The best privileged access management tools can help you do all that in only a few clicks, with minimum input from your crew.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
Newsletter
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in
your inbox.
Livia Gyongyoși is a Communications and PR Officer within Heimdal®, passionate about cybersecurity. Always interested in being up to date with the latest news regarding this domain, Livia’s goal is to keep others informed about best practices and solutions that help avoid cyberattacks.
Original Post URL: https://heimdalsecurity.com/blog/what-is-a-jump-server/
Category & Tags: Cybersecurity Basics – Cybersecurity Basics
Views: 0