Source: heimdalsecurity.com – Author: Livia Gyongyoși
Rust standard library flaw dubbed BatBadBut lets hackers target Windows systems in command injection attacks.
The vulnerability impacts all Rust versions before 1.77.2 on Windows, but only in case code or dependencies execute batch files with untrusted arguments. Rust Security urged users to upgrade to the latest version, 1.77.2. The new version includes patches that fix the BatBadBut vulnerability.
More about the Rust standard library flaw
The vulnerability is tracked as CVE-2024-24576 and is only effective when invoking batch files on Windows with untrusted arguments. The Rust standard library flaw got a severity score of 10.0, which means critical.
Researchers say the cause for this vulnerability is insufficient validation of arguments passed to Command::arg and Command::args APIs.
The problem is that:
the Rust standard library did not properly escape arguments when invoking batch files (with the bat and cmd extensions) on Windows using the Command API. An attacker able to control the arguments passed to the spawned process could execute arbitrary shell commands by bypassing the escaping.
Source – Rust Security Advisory
Rust credits RyotaK for revealing the vulnerability – which he dubbed BatBadBut, and Simon Sawicki for helping to fix the issue.
According to the security researcher who discovered and reported the Rust standard library flaw, the real cause of the problem is Windows.
The root cause of BatBadBut is the overlooked behavior of the CreateProcess function on Windows. When executing batch files with the CreateProcess function, Windows implicitly spawns cmd.exe because Windows can’t execute batch files without it.
Source – RyotaK’s blog post
Reddit discussions on programming and cybersecurity groups also point to a Windows problem causing the BatBadBut vulnerability.
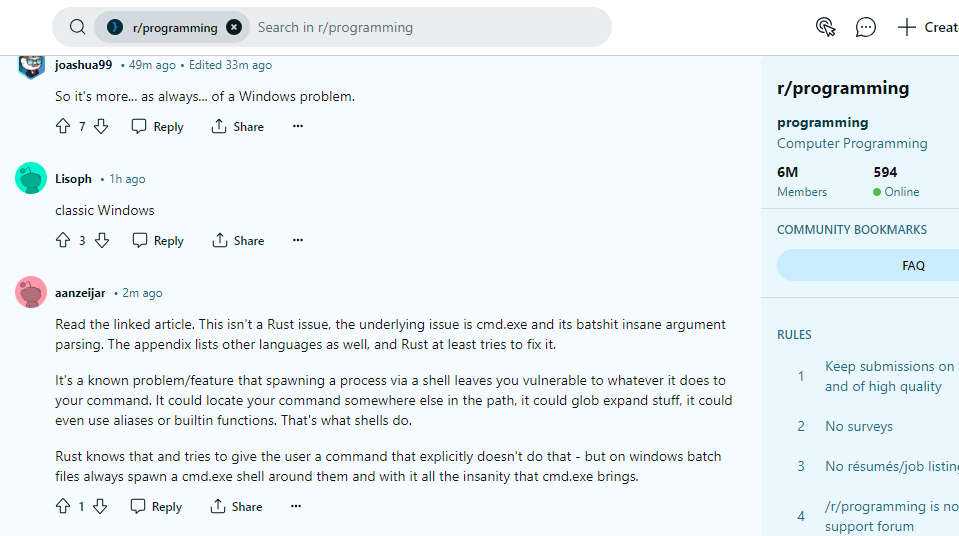
Source – r/programming
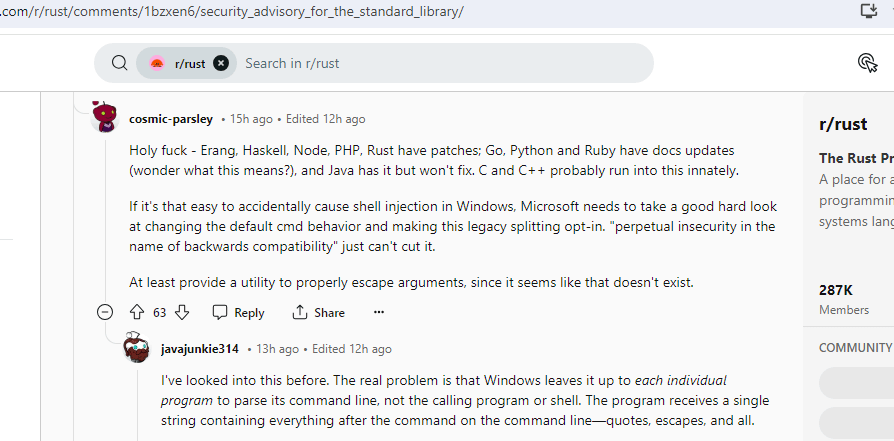
Source – r/Rust
What is Rust?
Rust is a programming language that hundreds of companies worldwide use in production. Firefox, Dropbox, and Cloudflare are among the Rust users.
The White House Office of the National Cyber Director (ONCD) recently quoted it as a memory safe programming language.
To stop potential hackers from exploiting the BatBadBut flaw, apply patches timely.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.
Newsletter
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in
your inbox.
Livia Gyongyoși is a Communications and PR Officer within Heimdal®, passionate about cybersecurity. Always interested in being up to date with the latest news regarding this domain, Livia’s goal is to keep others informed about best practices and solutions that help avoid cyberattacks.
Original Post URL: https://heimdalsecurity.com/blog/rust-standard-library-flaw-windows/
Category & Tags: Cybersecurity News – Cybersecurity News




















































