Source: www.bleepingcomputer.com – Author: Bill Toulas

A new version of the BiBi Wiper malware is now deleting the disk partition table to make data restoration harder, extending the downtime for targeted victims.
BiBi Wiper attacks on Israel and Albania are linked to a suspected Iranian hacking group named ‘Void Manticore’ (Storm-842), which is believed to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS).
BiBi Wiper was first spotted by Security Joes in October 2023, with its activities prompting an alert from Israel’s CERT in November 2023 about large-scale offensive cyber operations using it against critical organizations in the country.
A new report from Check Point Research uncovers newer variants of the BiBi wiper and two other custom wipers used by the same threat group, namely Cl Wiper and Partition Wiper.
The report also highlights operational overlaps between Void Manticore and ‘Scarred Manticore,’ another Iranian threat group, suggesting cooperation between the two.
Fake personas and cooperative attacks
CheckPoint suspects Void Manticore hides behind the ‘Karma’ hacktivism group on Telegram, which appeared following the Hamas attack on Israel in October.
Karma has claimed attacks against over 40 Israeli organizations, publishing stolen data or evidence of wiped drives on Telegram to amplify the damage of their operations.
A persona used for the Albanian attacks is named ‘Homeland Justice,’ which leaked some of the stolen files on Telegram.
This strategy is very similar to the approach Sandworm (APT44) has followed, who, according to Mandiant, hides behind hacktivist-branded Telegram channels like XakNet Team, CyberArmyofRussia_Reborn, and Solntsepek.
Another interesting finding is that Void Manticore appears to have handed over control of compromised infrastructure by Scarred Manticore in some instances.
Scarred Manticore focuses on establishing initial access, primarily by leveraging the Microsoft Sharepoint CVE-2019-0604 flaw, performing SMB lateral movement, and harvesting emails.
The compromised organizations are then handed off to Void Manticore, which conducts the payload injection stages, lateral movement on the network, and the deployment of the data wipers.
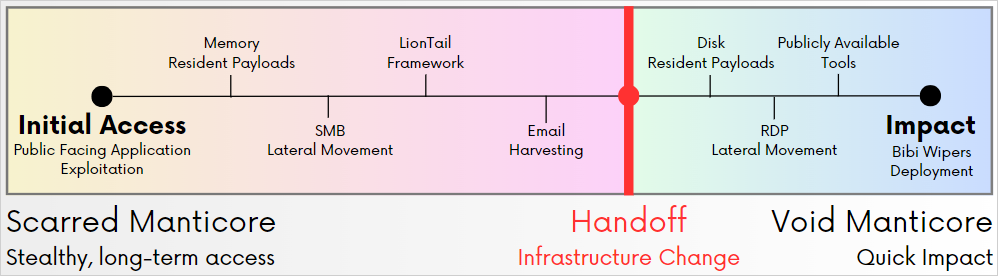
Source: Check Point
Void Manticore tools
Void Manticore uses various tools to carry out its destructive operations, including web shells, manual deletion tools, custom wipers, and credential verification tools.
Karma Shell is the first payload to be deployed on a compromised web server, which is a custom web shell disguised as an error page that can list directories, create processes, upload files, and manage services.
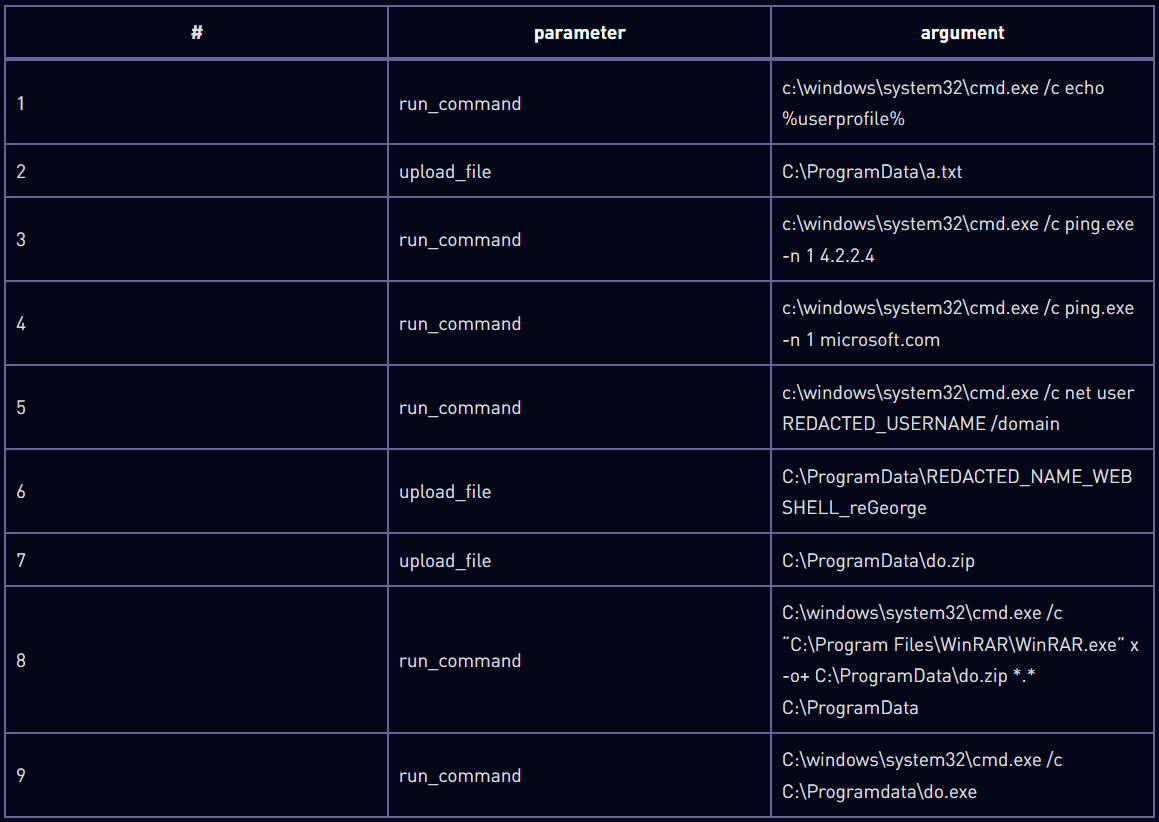
Source: Check Point
The newer versions of the BiBi Wiper seen by Check Point corrupt non-system files with random data and append a randomly generated extension containing the “BiBi” string.
BiBi has both a Linux and a Windows variant, with some unique characteristics and minor operational differences reserved for each.
For example, on Linux, BiBi will spawn several threads based on the number of available CPU cores to speed up the wiping process. On Windows, BiBi will skip .sys, .exe, and .dll files to avoid rendering the system unbootable.
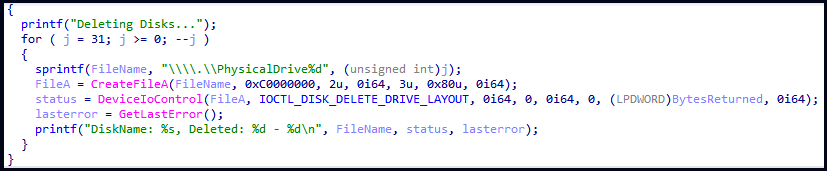
Compared to past malware versions, the newer variants are configured only to target Israeli systems and do not delete shadow copies or disable the system’s Error Recovery screen. However, they now remove partition information from the disk, making it more difficult to recover data.
Source: Check Point
The CI Wiper, first seen in attacks against Albanian systems, employs the ‘ElRawDisk’ driver to perform wiping operations, overwriting physical drive contents with a predefined buffer.
Partition Wipers specifically target the system’s partition table, so the disk layout cannot be recovered, complicating the data restoration efforts and maximizing the damage done.
Attacks from those wipers often result in victims getting a blue screen of death (BSOD) or system crashes upon reboot, as they affect both the Master Boot Record (MBR) and GUID Partition Table (GPT) partitions.
Original Post URL: https://www.bleepingcomputer.com/news/security/new-bibi-wiper-version-also-destroys-the-disk-partition-table/
Category & Tags: Security – Security
Views: 0