Source: heimdalsecurity.com – Author: Cristian Neagu
What Is Vulnerability Management?
Vulnerability management is an ongoing risk-based approach to discovering, prioritizing, and mitigating vulnerabilities and misconfigurations.
The purpose of vulnerability management is to reduce the organization’s overall risk exposure caused by vulnerabilities. Given the great number of potential vulnerabilities and the limited resources available for remediation, this can prove to be a challenging task.
Vulnerability Management vs. Patch Management
As explained previously, vulnerability management is a proactive process designed for identifying, preventing, mitigating, and classifying vulnerabilities. Based on the nature of the vulnerability or threat, different approaches are required to take care of it. This is where patch management comes in, as it is the technique of resolving software vulnerabilities in a network by deploying patches. Patch management, in this sense, is an essential component of vulnerability management. I have previously written an article where I go more in-depth on the differences between the two processes, which you can check out here.
Vulnerability Management vs. Vulnerability Assessment
Typically, a vulnerability assessment is a piece of the vulnerability management process. Typically, to gain more useful information on the health of the system, organizations will run multiple vulnerability assessments to come up with an effective vulnerability management program.
Vulnerability Management vs. Risk-Based Vulnerability Management
Risk-based vulnerability management (RBVM) is a cybersecurity strategy that allows organizations to use security intelligence to identify, prioritize, and address the most serious vulnerabilities based on the context of their risk. This concept is also met under the name of Vulnerability Risk Management. Unlike vulnerability management, RBVM is a risk-based approach that focuses on the likelihood of a vulnerability being exploited, rather than just on the severity of potential consequences if it is exploited.
How Are Vulnerabilities Ranked?
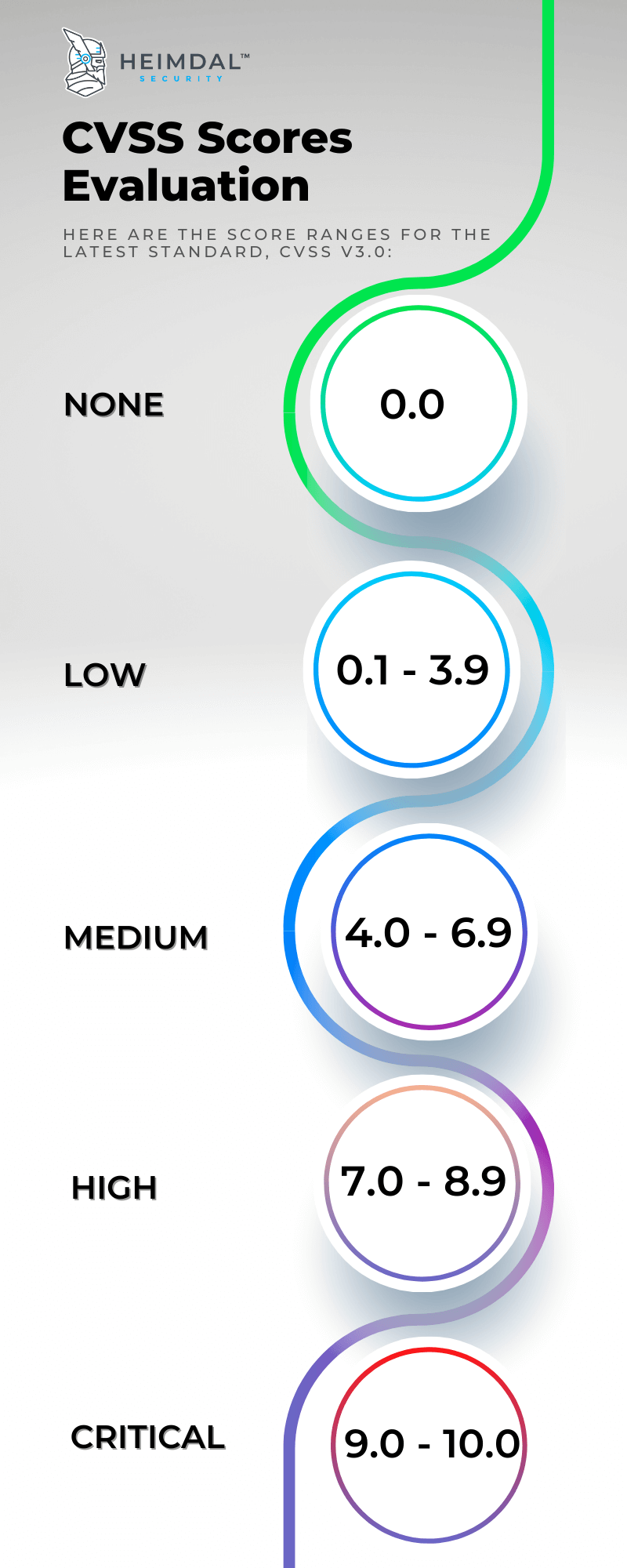
Many cybersecurity organizations use the Common Vulnerability Scoring System (CVSS) to assess and convey software vulnerabilities’ severity and characteristics. It is a free and open industry standard. The CVSS Base Score ranges from 0.0 to 10.0, and CVSS scores are given a severity grade by the National Vulnerability Database (NVD).
The NVD also contains vulnerability data that automated vulnerability management solutions and IT staff pull from.
The Vulnerability Management Process
- Asset Discovery: the first step in the process is to create an inventory of your organization’s assets, including software, hardware, operating systems, and services. This step will help you keep better track of the current versions and previously applied patches on your assets. Revisit the list periodically to update it when you add new assets or move to a different version.
- Asset Prioritization And Categorization: when you have the directory completed, the next step is to classify your assets based on their risk level and importance to business operations.
- Vulnerability Assessment: now, with the baseline risk profiles established, and the priority level determined, it is time for vulnerability assessment. The process should consider each asset’s classification, its criticality, and exposure to vulnerabilities.
- Reporting: determine the various levels of risk associated with each asset based on the results of the assessment. After that, document your security plan and report known vulnerabilities.
- Remediation: the most important part of a vulnerability management process is actually remediating vulnerabilities through patching.
- Reassessment: when vulnerabilities are fixed, it is indicated to conduct another vulnerability assessment to ensure the mitigation or remediation efforts worked.
- Verification And Monitoring: use regular audits and process follow-ups to ensure that threats have been eliminated.
With our Heimdal® Patch & Asset Management module, patching can be fully automated, allowing you to schedule the process according to your own needs.
Benefits of Vulnerability Management
Improved Security and Control
By regularly scanning for vulnerabilities and pathing them in a timely manner, organizations can make it harder for threat actors to gain access to their systems. Additionally, with a robust vulnerability management program in place, organizations can easily identify weaknesses in their security posture before attackers notice them.
Cost-Effectiveness
As you can see, vulnerability management is essential for safeguarding your company from the acts of threat actors that might try to compromise your systems.
One of the top benefits of vulnerability management is its cost-effectiveness. An automated solution will save your organization from ineffective patching and will also contribute to a reduction of technical debt.
Simply said, vulnerability management aids in the organization’s security posture’s structure and clarity, strengthening its justification to stakeholders who will therefore be more willing to support vulnerability programs.
Quick Response to Threats
Threat actors don’t rest or take vacations! Every day, vulnerabilities are discovered when we least expect them. Organizations can transition from a reactive to a proactive reaction with the aid of vulnerability management.
Setting up a continuous patch management strategy makes guarantees that major vulnerabilities are quickly identified, given priority, and have the resources to be fixed. By doing this, it creates the framework for a quicker and more efficient reaction to threats as they materialize.
Enhances Visibility and Reporting
Having visibility into a project helps stakeholders understand the return on investment in security and can benefit subsequent projects. The resulting reports provide senior management with key metrics and indicators, which are helpful in the process of making informed decisions on key initiatives.
The result of the reports also helps the team with actionable dashboards and trend reports, which helps them in measuring the performance and state of the program.
Operational Efficiency
Maintaining team and system alignment with project objectives and results is crucial, particularly when highly sensitive security for an organization is involved.
Vulnerability management aims to specify the procedure for locating vulnerabilities and resolving them in order to maintain alignment. It also has the potential to reduce manual workflow, and besides this, it also provides continuous monitoring, alerting, and remediation solutions.
Vulnerability Management Best Practices
- Conduct Asset Discovery And Inventory: include all the devices and software owned and managed by your organization, as well as those owned by third-party vendors. This is a crucial practice in the vulnerability management process as organizations can determine which assets pose the most significant risk, and thus prioritize vulnerability scanning accordingly.
- Classify Assets And Assign Tasks: classify the identified assets based on their vulnerability risk to the organization. Risk classification will help you determine the frequency of vulnerability scanning and the priority of remediation efforts. Also, assigning ownership of assets to system owners who are ultimately responsible for the risks and liability of the assets if those become compromised is important.
- Conduct Vulnerability Scannings Frequently: vulnerability management should be a continuous protection process, and taking into consideration the speed with which vulnerabilities are discovered, conducting vulnerability scannings regularly is mandatory. New vulnerabilities can be discovered daily, with many of them being exploited by threat actors within days or hours after they’re discovered. This is why we recommend opting for an automated vulnerability management solution.
- Prioritize the Vulnerabilities And Take Action: organisations must prioritise vulnerabilities depending on their impact on the organisation after the scan is finished, and take appropriate corrective action.
- Set Up a Comprehensive Vulnerability Management Strategy: establish a strategy that includes the people, processes, and technology in your organization to manage vulnerabilities effectively. It is important to plan ahead and establish clear KPIs to guide the security team moving on, and assess ROI.
How Can Heimdal® Help Your Organization?
Vulnerability management is a continuous process, that if handled manually can put a lot of stress on your IT team and block resources for extended periods. Nevertheless to say that dealing with vulnerability management manually also has a high error rate. Opting for an automated solution seems to be the way to go nowadays, and luckily, Heimdal® Patch & Asset Management solution comes in handy for your organization.
With our solution, you will be able to:
- Patch Windows, Linux, macOS, Third-Party, and even proprietary apps, all in one place;
- Generate software and assets inventories;
- Easily achieve compliance with automatically generated detailed reports (GDPR, UK PSN, HIPAA, PCI-DSS, NIST);
- Automatically conduct vulnerability and risk management processes;
- Close vulnerabilities, mitigate exploits, deploy updates both globally and locally, anytime, from anywhere in the world;
- Customize your solution based to perfectly fit the needs of your organization.
Enjoy a fully customizable, hyper-automated solution, that you govern! Additionally, we deliver to your endpoints locally utilising HTTPS transfers encrypted packages that have been repackaged and are ad-free.
Install and Patch Software. Close Vulnerabilities. Achieve Compliance.
Heimdal® Patch & Asset Management
Remotely and automatically install Windows, Linux and 3rd party patches and manage your software inventory.
- Create policies that meet your exact needs;
- Full compliance and CVE/CVSS audit trail;
- Gain extensive vulnerability intelligence;
- And much more than we can fit in here…
If you want to keep up to date with everything we post, don’t forget to follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/vulnerability-management/
Category & Tags: Patch management,Vulnerability,vulnerability management – Patch management,Vulnerability,vulnerability management
Views: 1





















































