Source: levelblue.com – Author: hello@alienvault.com.
The old phrase “we’re only human, after all” is what cyber-adversaries are relying upon to gain access to intellectual property, data, and credentials. Adversaries prey on the humanity in us to read an unsolicited email, act out of a sense of urgency, or succumb to their scare tactics.
We are bombarded with social engineering scams daily. Why do some of us fall victim while others see through veiled attempts at getting us to relinquish something of value? At LevelBlue, we set about researching social engineering and the human element and came away with some telling data as well as the gaps where attackers thrive.
Here are a few highlights from the research. How is your organization dealing with social engineering? Do you have a plan for employee education? Do you have a culture of cybersecurity?
Download this new research now and use it as a starting point for your discussion on social engineering.
1. Build a culture of cybersecurity from the top. Only 43% of organizations have a strong cybersecurity culture. Leadership as it relates to cybersecurity means that all leaders have responsibility for cybersecurity including KPIs and metrics.
2. Invest in education. Deepfakes are problematic; 59% of organizations say their employees are unable to discern real from fake. And, only 26% of organizations make workforce training a primary area of focus. New types of attacks call for new types of training. Without awareness of social engineering tactics, well-meaning employees may fall to a cyber adversary.
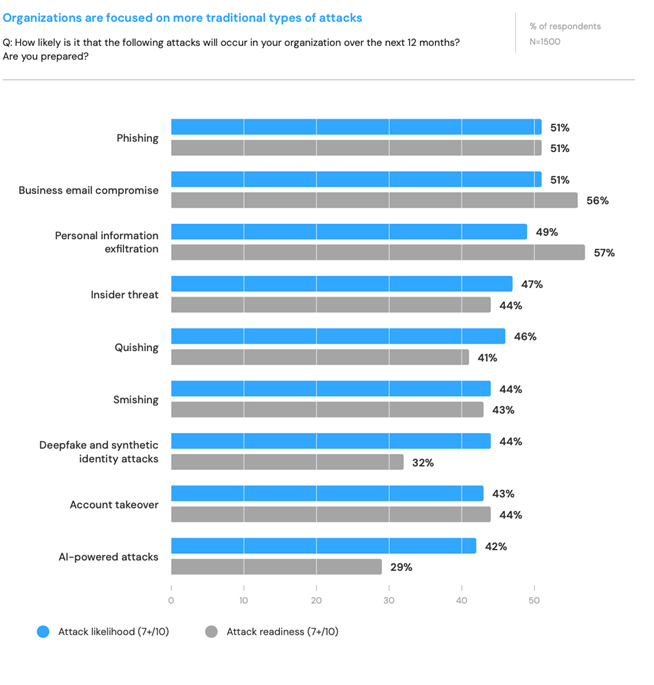
3. Prepare and understand emerging attack types. Adversaries want to stay one step ahead of us, and they do this by evolving their attack types. A majority of organizations, 56%, feel prepared for business email compromise (BEC) attacks. However, preparedness for deepfake (32%) and AI-driven (29%) drops sharply, despite those attack types seen as likely to occur.
Building a culture of cybersecurity, investing in workforce education, and preparing for emerging attack types targeted at humans prove that cybersecurity is not a technical issue – it is a business requirement.
The content provided herein is for general informational purposes only and should not be construed as legal, regulatory, compliance, or cybersecurity advice. Organizations should consult their own legal, compliance, or cybersecurity professionals regarding specific obligations and risk management strategies. While LevelBlue’s Managed Threat Detection and Response solutions are designed to support threat detection and response at the endpoint level, they are not a substitute for comprehensive network monitoring, vulnerability management, or a full cybersecurity program.
Original Post url: https://levelblue.com/blogs/security-essentials/we-are-the-weakest-link
Category & Tags: –
Views: 2




















































