Source: socprime.com – Author: Steven Edwards
Adversaries frequently repurpose trusted tools like curl.exe to tunnel traffic through SOCKS proxies and even reach .onion domains. Whether it’s for data exfiltration or command-and-control communication, such activity often flies under the radar—unless you’re explicitly detecting for it.
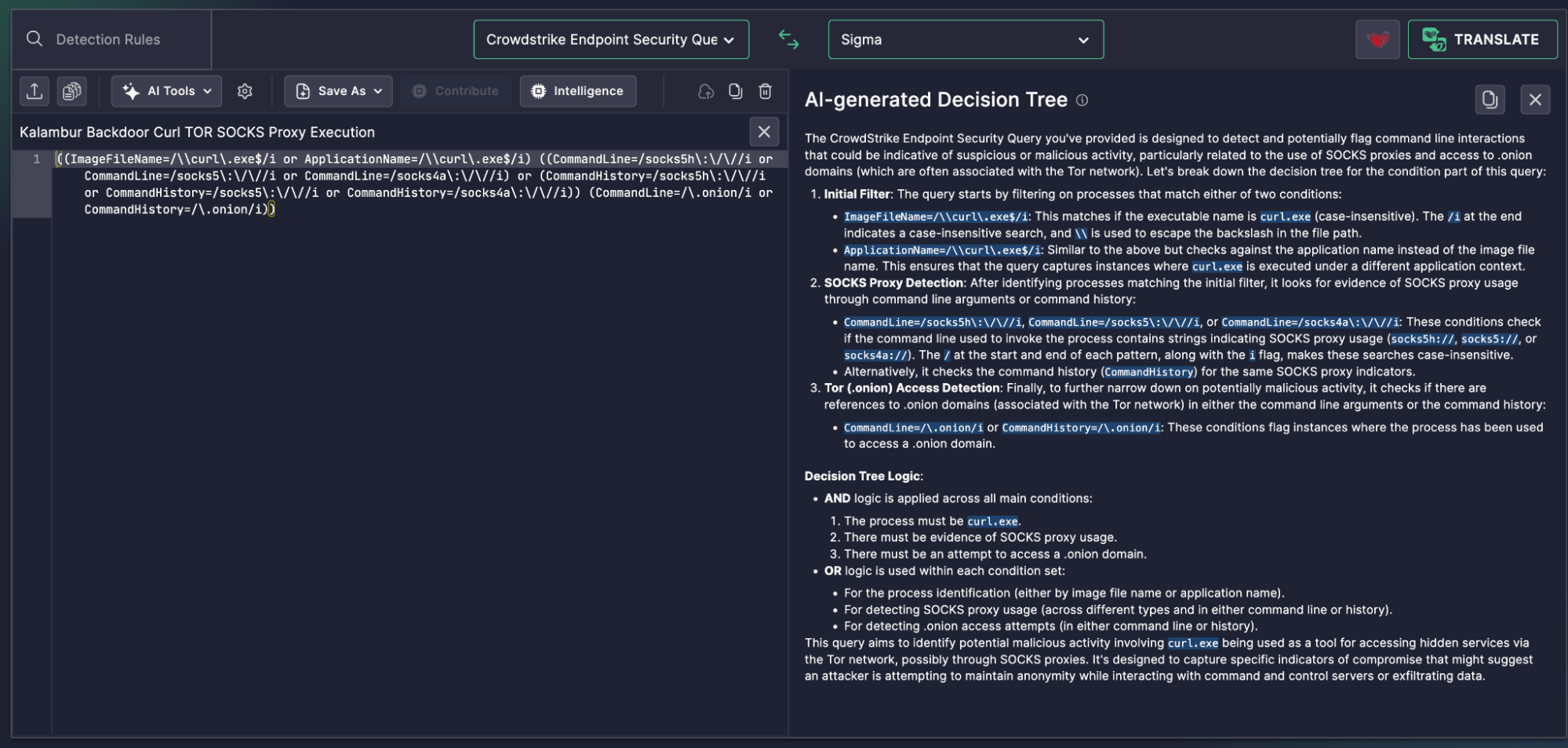
This is exactly what CrowdStrike Endpoint Security Query Language allows teams to do. But when logic grows dense, detection engineers and SOC analysts alike benefit from Uncoder AI’s AI-generated Decision Tree, which lays out every branch of the rule in a clean, visual format.
Detection Objective: curl.exe + TOR Proxy Indicators
The CrowdStrike detection rule monitors for:
- Process execution of curl.exe, checked via both ImageFileName and ApplicationName fields
- SOCKS proxy arguments, such as socks5h://, socks5://, or socks4a:// in:
- The command line
- The command history
- The command line
- Access to .onion domains, indicating dark web communication
This multi-faceted query uses both command-line and historical arguments to ensure thorough visibility into how curl.exe is being leveraged.
Input we used (click to show the text)
((ImageFileName=/\curl.exe$/i or ApplicationName=/\curl.exe$/i) ((CommandLine=/socks5h:///i or CommandLine=/socks5:///i or CommandLine=/socks4a:///i) or (CommandHistory=/socks5h:///i or CommandHistory=/socks5:///i or CommandHistory=/socks4a:///i)) (CommandLine=/.onion/i or CommandHistory=/.onion/i))
What the AI Decision Tree Revealed
Uncoder AI broke this into a clear sequence of logical conditions:
- Initial Process Match
- ImageFileName or ApplicationName must end with curl.exe (case-insensitive)
- ImageFileName or ApplicationName must end with curl.exe (case-insensitive)
- SOCKS Proxy Usage Evidence
- Detected via CommandLine or CommandHistory matching SOCKS patterns (socks5h, socks5, socks4a)
- Detected via CommandLine or CommandHistory matching SOCKS patterns (socks5h, socks5, socks4a)
- .onion Traffic Detection
- Detected again in both CommandLine and CommandHistory
- Detected again in both CommandLine and CommandHistory
The tree structure also separates AND logic from internal OR evaluations:
- You only trigger an alert when all three branches are satisfied: process match, proxy usage, and .onion domain reference.
Real-World Value
With this decision tree, defenders can instantly interpret what this detection targets and why:
- Identify backdoors like Kalambur or other implants using curl.exe to interact with hidden services.
- Monitor for abuse of proxies and anonymizing layers that may be used to bypass perimeter defenses.
Pinpoint post-exploitation activity that attempts to blend with legitimate admin behavior.
From Regex to Readable Logic
What once looked like dense CrowdStrike regex and nested conditions is now visually transparent, thanks to Uncoder AI. This empowers:
- Faster triage of curl-based alerts
- Easier tuning and validation of detection rules
- More accessible handoff between threat hunters and incident responders
Original Post URL: https://socprime.com/blog/visualizing-malicious-curl-proxy-activity-in-crowdstrike-with-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,AI-generated Decision Tree,CrowdStrike Endpoint Security,Uncoder AI – Blog,SOC Prime Platform,AI-generated Decision Tree,CrowdStrike Endpoint Security,Uncoder AI
Views: 8




















































