Source: socprime.com – Author: Steven Edwards
Loading legitimate system drivers from illegitimate or suspicious directories is a known tactic for persistence, evasion, or execution by adversaries. One high-value target in this category is clfs.sys — a legitimate Windows driver tied to the Common Log File System.
To detect this activity, Microsoft Defender for Endpoint supports advanced KQL-based detection logic. But to truly operationalize these queries, analysts need visibility into how they work. That’s exactly what Uncoder AI’s AI-generated Decision Tree delivers.
Use Case: clfs.sys Loaded From User or Temp Paths
This query identifies when clfs.sys is loaded from non-standard or user-controlled directories, which may include:
UsersPublicTemporary InternetWindowsTemp- Subfolders under
Userssuch asPictures,Contacts, orFavourites
These paths are rarely expected to host or initiate the loading of system-level drivers, making such activity highly suspicious.
Input we used (click to show the text)
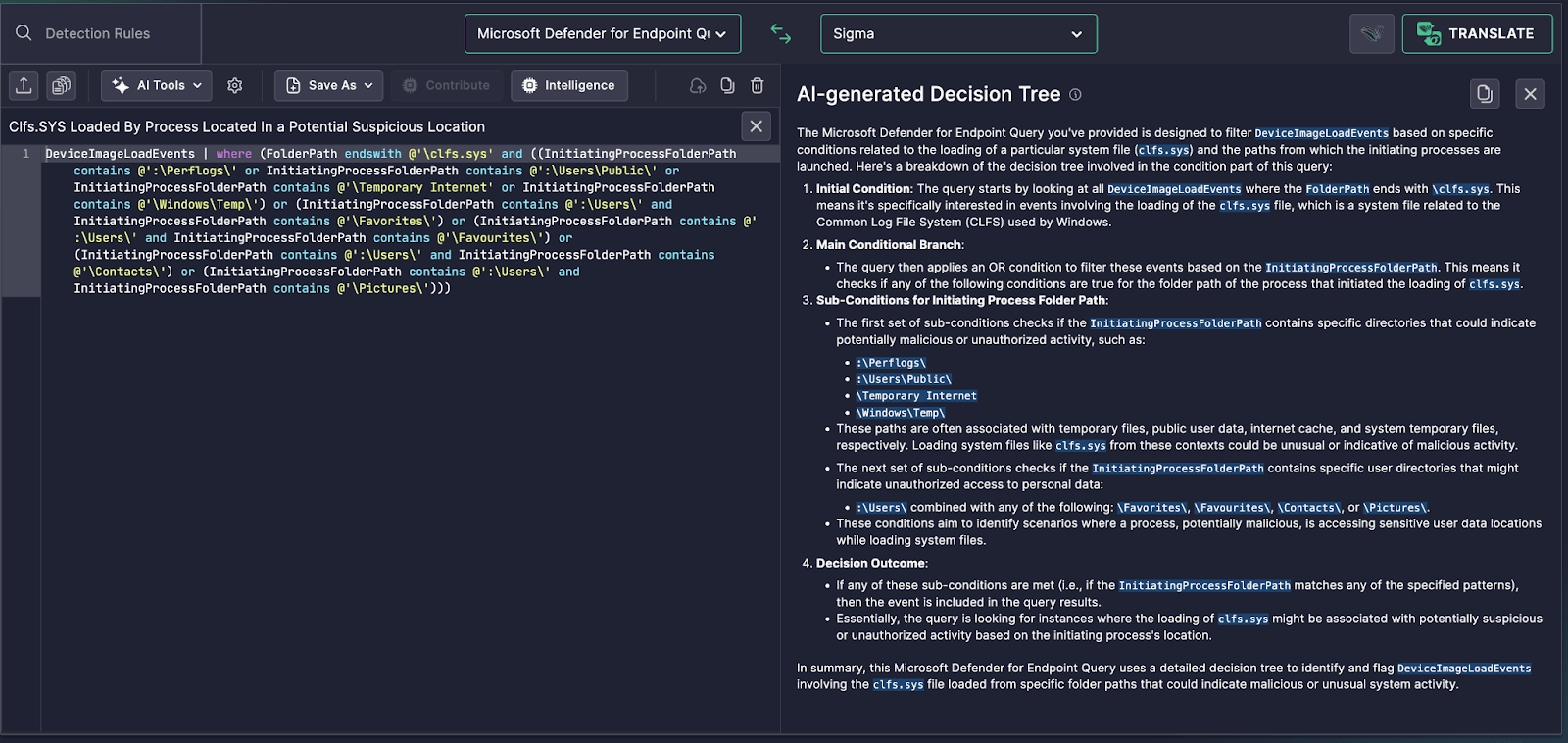
DeviceImageLoadEvents | where (FolderPath endswith @'clfs.sys' and ((InitiatingProcessFolderPath contains @':Perflogs' or InitiatingProcessFolderPath contains @':UsersPublic' or InitiatingProcessFolderPath contains @'Temporary Internet' or InitiatingProcessFolderPath contains @'WindowsTemp') or (InitiatingProcessFolderPath contains @':Users' and InitiatingProcessFolderPath contains @'Favorites') or (InitiatingProcessFolderPath contains @':Users' and InitiatingProcessFolderPath contains @'Favourites') or (InitiatingProcessFolderPath contains @':Users' and InitiatingProcessFolderPath contains @'Contacts') or (InitiatingProcessFolderPath contains @':Users' and InitiatingProcessFolderPath contains @'Pictures')))
Uncoder AI automatically transforms this detection logic into a human-readable decision tree structure, showing:
- Query Scope:
It filters fromDeviceImageLoadEventswhere the folder path ends withclfs.sys. - Folder Path Conditions:
The decision tree checks whether the initiating process’s folder path contains any unusual user or temporary storage locations. - Branching Conditions:
Sub-branches clarify which paths are considered:- Generic temp or cache folders
- User-specific locations that imply personal data access
- Combined conditions like
Users+FavouritesorPictures
Outcome:
If any one of these conditions is met, the event is marked as relevant—flagging a potential misuse of clfs.sys from suspicious origin paths.
AI Output (click to show the text)
The Microsoft Defender for Endpoint Query you've provided is designed to filter `DeviceImageLoadEvents` based on specific conditions related to the loading of a particular system file (`clfs.sys`) and the paths from which the initiating processes are launched. Here's a breakdown of the decision tree involved in the condition part of this query:
1. **Initial Condition**: The query starts by looking at all `DeviceImageLoadEvents` where the `FolderPath` ends with `clfs.sys`. This means it's specifically interested in events involving the loading of the `clfs.sys` file, which is a system file related to the Common Log File System (CLFS) used by Windows.
2. **Main Conditional Branch**:
- The query then applies an OR condition to filter these events based on the `InitiatingProcessFolderPath`. This means it checks if any of the following conditions are true for the folder path of the process that initiated the loading of `clfs.sys`.
3. **Sub-Conditions for Initiating Process Folder Path**:
- The first set of sub-conditions checks if the `InitiatingProcessFolderPath` contains specific directories that could indicate potentially malicious or unauthorized activity, such as:
- `:Perflogs`
- `:UsersPublic`
- `Temporary Internet`
- `WindowsTemp`
- These paths are often associated with temporary files, public user data, internet cache, and system temporary files, respectively. Loading system files like `clfs.sys` from these contexts could be unusual or indicative of malicious activity.
- The next set of sub-conditions checks if the `InitiatingProcessFolderPath` contains specific user directories that might indicate unauthorized access to personal data:
- `:Users` combined with any of the following: `Favorites`, `Favourites`, `Contacts`, or `Pictures`.
- These conditions aim to identify scenarios where a process, potentially malicious, is accessing sensitive user data locations while loading system files.
4. **Decision Outcome**:
- If any of these sub-conditions are met (i.e., if the `InitiatingProcessFolderPath` matches any of the specified patterns), then the event is included in the query results.
- Essentially, the query is looking for instances where the loading of `clfs.sys` might be associated with potentially suspicious or unauthorized activity based on the initiating process's location.
In summary, this Microsoft Defender for Endpoint Query uses a detailed decision tree to identify and flag `DeviceImageLoadEvents` involving the `clfs.sys` file loaded from specific folder paths that could indicate malicious or unusual system activity.
Why This Matters
- Elevated Context: Analysts no longer need to decipher layered OR conditions to understand risk coverage.
- Faster Triage: You can see in seconds whether the rule catches temp path misuse, user folder abuse, or both.
- Audit-Ready Logic: The tree-style breakdown supports easier documentation and SOC training efforts.
Ultimately, loading clfs.sys from outside its expected system directories may represent driver abuse, living-off-the-land tactics, or malware masquerading as legitimate processes.
From Folder Flags to Threat Defense
Uncoder AI’s Decision Tree takes verbose KQL and turns it into an intuitive, SOC-friendly format. Whether you’re tuning this rule, hunting for anomalies, or explaining detection logic to leadership—this feature makes it actionable.
Original Post URL: https://socprime.com/blog/soc-prime-platform/visualizing-clfs-sys-threat-activity-in-microsoft-defender-with-uncoder-ais-decision-tree/
Category & Tags: Blog,SOC Prime Platform,AI-generated Decision Tree,Microsoft Defender for Endpoint,Uncoder AI – Blog,SOC Prime Platform,AI-generated Decision Tree,Microsoft Defender for Endpoint,Uncoder AI
Views: 6



















































