Source: securityboulevard.com – Author: Michael Toback

Introduction
The concept of “BYOD Policy for Small Business” is gaining unprecedented momentum. The integration of personal devices in the workplace is not just a trend. It is truly a reflection of the evolving work culture. Small businesses are recognized for their adaptability and innovation. They are increasingly embracing Bring Your Own Device (BYOD) policies. Businesses see these policies as a gateway to enhanced productivity and employee satisfaction.
The infographic illustrates the remarkable journey of BYOD policies. It highlights their inception, adoption rates, and the profound impact they have on small businesses. It provides a snapshot of the explosive growth of the BYOD market. Following that, the accelerated adoption due to the COVID-19 pandemic, and the tangible benefits reaped by businesses. However, it also sheds light on the concerns and challenges. It emphasizes the importance of navigating the BYOD landscape with caution and responsibility.
In this article, we will delve deeper into the intricacies of BYOD policies. We will explore their significance, components, benefits, and the considerations small businesses must bear in mind to implement them successfully. This piece will equip you with the knowledge and insights to understand and formulate a robust BYOD policy. Thus, fostering a secure and harmonious work environment.
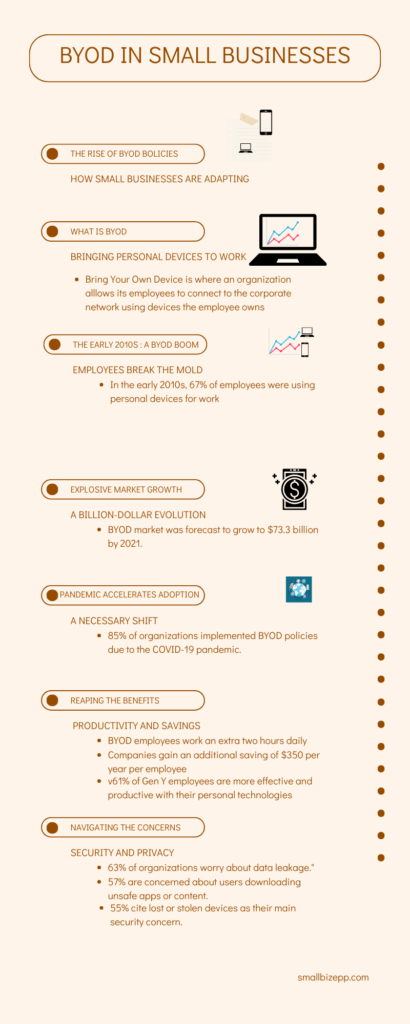
The BYOD Phenomenon: A Double-Edged Sword
The BYOD phenomenon is sweeping across the business landscape, creating waves of change, especially among small businesses. It’s a revolutionary concept allowing employees to use their personal devices—be it smartphones, tablets, or laptops—for work purposes. This fusion of the personal and professional realms is reshaping the way we perceive and interact with our work environment.
Growing Popularity among Small Businesses
Small businesses, with their dynamic nature and nimbleness, are particularly drawn to BYOD policies. The allure lies in the flexibility and convenience it offers to employees, fostering a more comfortable and productive work setting. It’s no longer about being chained to a desk; it’s about breaking free and embracing mobility and accessibility. This shift is not just about convenience; it’s a strategic move aimed at enhancing operational efficiency and employee satisfaction.
Benefits of BYOD
The advantages of implementing a BYOD policy are manifold. It propels productivity as employees, using their own devices, often work faster and longer. It also leads to significant cost savings as businesses no longer bear the brunt of procuring and maintaining hardware. Moreover, employee morale receives a boost as they enjoy the freedom to work on devices they are familiar with. Thus, reducing the learning curve associated with new technology.
- Enhanced Productivity: Employees tend to be more comfortable and proficient with their own devices, leading to increased efficiency and output.
- Cost Efficiency: The financial burden on the company diminishes as employees use their own devices.
- Employee Satisfaction: The flexibility and familiarity of using personal devices enhance job satisfaction and morale among employees.
Potential Risks and Concerns
However, the BYOD phenomenon is not without its share of challenges and risks, primarily revolving around security. The integration of personal devices into company networks opens up avenues for security breaches and data leaks. When a device falls into the wrong hands or when an employee leaves the company, the risk of sensitive company data being exposed escalates. Additionally, the diversity in devices and operating systems can pose compatibility and management challenges, necessitating robust mobile device management solutions.
- Security Risks: The mingling of personal and work data can lead to potential security breaches. This is especially true if devices are lost or stolen.
- Data Leakage: The risk of sensitive company data falling into the wrong hands is heightened.
- Management Challenges: The diversity in devices necessitates comprehensive management solutions to ensure compatibility and security.
Balancing Act
Embracing BYOD is like walking a tightrope. While the benefits are substantial, the potential risks cannot be overlooked. It’s crucial for small businesses to weigh the pros and cons and implement stringent policies and security measures to mitigate risks. Create a well-structured BYOD policy, coupled with employee education and awareness. That can help in harnessing the potential of BYOD while safeguarding against its pitfalls.
In the subsequent sections, we will delve into the components of a sound BYOD policy. We will provide insights on how small businesses can navigate this double-edged sword effectively. Thus, ensuring security and compliance while reaping the benefits of flexibility and productivity.
Why Small Businesses Can’t Ignore BYOD in 2023
In the evolving landscape of the business world, the relevance of BYOD policies is more pronounced than ever. This is especially true for small businesses striving to maintain operational fluidity and employee satisfaction. The year 2023 marks a pivotal moment for small businesses to acknowledge and adapt to the BYOD phenomenon. This phenomenon has become an integral component of organizational culture and operational efficiency.
The adoption of BYOD is not just a fleeting trend but a reflection of a transformative shift in work dynamics. Small businesses, with their inherent need for flexibility and adaptability, find BYOD policies particularly beneficial. It allows employees the comfort of using their own devices. This can foster a sense of familiarity and ease, which, in turn, enhances productivity and job satisfaction.
A study by VMware underscores the significance of BYOD in enhancing employee satisfaction. 61% of participants in this survey reported being happier in their jobs when they could use their personal devices for work. This statistic is not just a number. This statistic is a testament to the positive impact of BYOD on the workforce’s morale and contentment. It illustrates how the freedom to use personal devices for work-related tasks can contribute to a more satisfied and, consequently, more productive workforce.
The Challenges of Using BYOD in Business
However, embracing BYOD is not without its challenges. Small businesses must navigate the complexities of security risks, data management, and legal implications associated with personal devices used for work purposes. It necessitates a meticulous approach to implementing BYOD policies. Thus, ensuring the safeguarding of both company and personal data while maintaining a balance between flexibility and control.
Now when remote working and digital reliance are the norms, ignoring BYOD is not an option for small businesses. It’s imperative to integrate BYOD policies strategically to leverage the benefits while mitigating the risks. By doing so, small businesses can foster a conducive work environment. Optimizing operational efficiency and allowing businesses to stay ahead in the competitive business landscape.
This section is not just a call to action. It is also a reminder of the transformative potential of BYOD in reshaping the work environment. Further BYOD can enhance the overall work experience for employees in small businesses. It’s a journey of embracing change, fostering innovation, and unlocking new possibilities in the realm of workplace dynamics.
Navigating the Security Minefield: Risks of BYOD
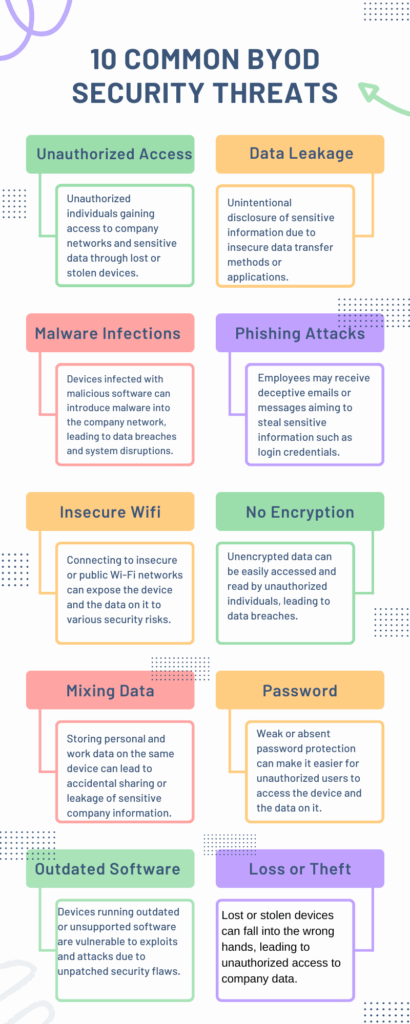
The convergence of personal and professional domains brings forth a plethora of security risks and challenges. The flexibility and convenience of using personal devices for work are undeniable. However, it is imperative to navigate the security minefield meticulously to prevent detrimental repercussions. Below is a detailed analysis of the security risks and challenges inherent to BYOD, illustrated by the accompanying infographic.
Unauthorized Access
The risk of unauthorized access is heightened when personal devices are used to access company networks and sensitive data. This is especially true for devices lacking robust security measures. A lost or stolen device can become a gateway for unauthorized individuals. This gateway will allow them to infiltrate company systems. This can lead to potential data breaches and compromising the integrity of company information.
Data Leakage
Data leakage is a formidable risk, often stemming from the use of insecure data transfer methods or applications. The unintentional disclosure of sensitive information can have far-reaching consequences. This can impact the confidentiality and security of company data and potentially leading to financial and reputational damage.
Malware Infections
Malware infections pose a significant threat, with infected devices acting as conduits to introduce malicious software into company networks. This can result in extensive data breaches, system disruptions, and operational downtime. This further necessitates stringent security measures to detect and mitigate malware threats.
Phishing Attacks
Phishing attacks are deceptive maneuvers aimed at tricking employees into divulging sensitive information such as login credentials. The repercussions of successful phishing attacks can be severe, leading to unauthorized access, data theft, and potential financial loss.
Insecure Wi-Fi Connections
The use of insecure or public Wi-Fi networks exposes devices and the data contained within to a myriad of security risks. The vulnerability associated with such connections can be exploited to intercept data transfers, compromise sensitive information, and infiltrate company networks.
Lack of Encryption
The absence of encryption renders data susceptible to unauthorized access and interpretation. Unencrypted data transmitted over networks can be easily intercepted. This data can be read, leading to data breaches and the exposure of sensitive information.
Outdated Software
Devices operating on outdated or unsupported software are vulnerable to attacks due to unpatched security flaws. The exploitation of such vulnerabilities can lead to system compromises, data breaches, and the disruption of business operations.
Device Loss or Theft
The loss or theft of devices is a prevalent risk. It has the potential to lead to unauthorized access to company data. The information stored on lost or stolen devices can fall into the wrong hands, posing substantial security risks.
Insufficient Password Protection
Weak or nonexistent password protection facilitates unauthorized access to devices and the data stored within. The lack of robust password policies can compromise the security of both personal and company data. This emphasizes the need for stringent password protocols.
Mixing Personal and Work Data
The amalgamation of personal and work data on the same device poses risks of accidental sharing or leakage of sensitive company information. The coexistence of diverse data necessitates meticulous management and segregation to prevent unintended disclosures.
Conclusion
The integration of BYOD policies within organizational structures is a double-edged sword. It offers numerous benefits but also presenting a multitude of security risks and challenges. The detailed analysis of these risks underscores the importance of implementing comprehensive security measures. This is done through robust BYOD policies and continuous employee education. These measures will help to safeguard against the pitfalls of BYOD while harnessing its potential benefits.
Crafting a Bulletproof BYOD Policy: Key Components
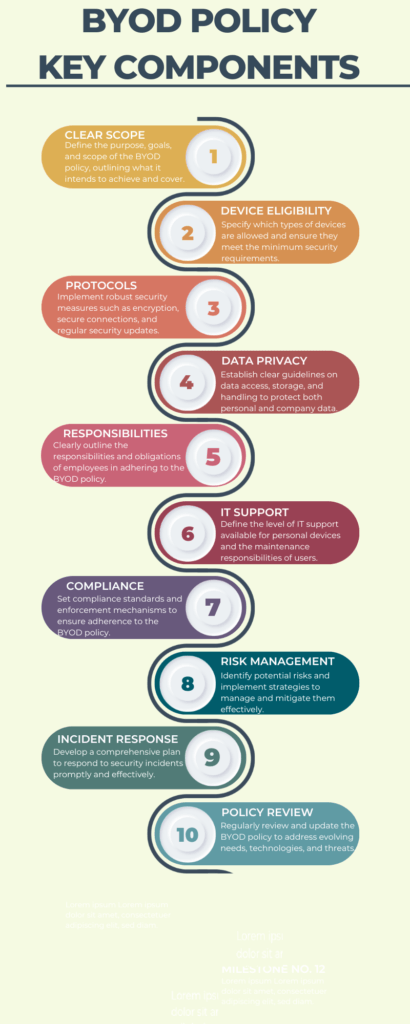
Crafting a robust BYOD policy is pivotal for mitigating risks. This policy also ensures the secure and efficient use of personal devices within the organizational framework. A well-structured BYOD policy serves as a cornerstone for balancing flexibility and security. The policy enables businesses to leverage the benefits of BYOD while safeguarding against potential vulnerabilities. The accompanying infographic illustrates the key components essential for crafting a bulletproof BYOD policy.
Clear Scope and Objectives
A BYOD policy should commence with a clear definition of its scope and objectives. It is crucial to delineate what the policy intends to achieve and the areas it will cover. Doing so will establish a foundation for its subsequent components and implementation.
Device Eligibility
Specifying the types of devices eligible under the BYOD policy is paramount. It ensures that only devices meeting the stipulated security and compatibility requirements are incorporated. Thus, mitigating risks associated with insecure or incompatible devices.
Security Protocols
The implementation of stringent security protocols is non-negotiable. Robust security measures such as encryption and secure connections are imperative to protect data integrity and confidentiality. These measures prevent unauthorized access and data breaches.
Data Privacy
Data privacy is at the core of BYOD policies. Establishing meticulous guidelines on data access, storage, and handling is essential to safeguard both personal and company data from unauthorized access and leakage.
User Responsibilities
Outlining user responsibilities provides clarity on the expectations and obligations of employees in adhering to the BYOD policy. It fosters accountability and compliance, ensuring the responsible use of personal devices within the organizational context.
IT Support and Maintenance
Defining the extent of IT support and maintenance available for personal devices clarifies the boundaries of organizational responsibility and user obligation in maintaining device functionality and security.
Compliance and Enforcement
Setting compliance standards and enforcement mechanisms is crucial for ensuring adherence to the BYOD policy. It reinforces the importance of compliance and provides a framework for addressing violations and non-compliance.
Risk Management
Effective risk management involves the identification and mitigation of potential risks associated with BYOD. Implementing proactive strategies to manage risks is essential for preventing security incidents and mitigating their impact.
Incident Response Plan
Having a comprehensive incident response plan in place is crucial for addressing security incidents promptly and effectively. It provides a structured approach to managing incidents, minimizing damage, and facilitating recovery.
Policy Review and Update
Regular reviews and updates of the BYOD policy are necessary to adapt to evolving technologies, needs, and threats. It ensures the continued relevance and effectiveness of the policy in addressing the dynamic landscape of BYOD.
Conclusion
Crafting a bulletproof BYOD policy is a meticulous process. It involves the integration of various components aimed at achieving security, flexibility, and compliance. The key components outlined in the infographic serve as a roadmap for developing a BYOD policy. This policy will stand resilient against the multifaceted challenges posed by the integration of personal devices in the professional domain.
Remote Working and BYOD: A Symbiotic Relationship
The advent of remote working has significantly amplified the relevance of Bring Your Own Device (BYOD) policies. These policies forge a symbiotic relationship that is reshaping the professional landscape. This synergy is not merely a coincidence. It is a reflection of the evolving needs and preferences of the modern workforce and organizations.
Enhanced Productivity and Flexibility
A study by Forbes reveals that 70% of employees who use their own devices at work are more productive. This enhanced productivity is a testament to the flexibility and convenience afforded by the amalgamation of remote working and BYOD. Doing so allows employees to leverage familiar and preferred devices, reducing the learning curve and fostering a conducive working environment.
Increased Adoption and Organizational Benefits
The synergy between remote working and BYOD is evident in the increased adoption of BYOD policies. Cisco reported that 69% of IT decision-makers favor BYOD. Doing so recognizes the time savings for workers and the resultant gains in organizational productivity. This mutual enhancement is a strategic alignment. It enables organizations to optimize resources, reduce operational costs, and adapt to the dynamic professional ecosystem.
Future of Work: Remote and BYOD
The future of work is undeniably leaning towards remote working. Upwork projected that 36.2 million Americans will be working remotely by 2025. This trend underscores the pivotal role of BYOD in facilitating remote work. Remote work serves as a catalyst for the transformation of work models and the realization of a balanced and inclusive professional paradigm.
Conclusion
The symbiotic relationship between remote working and BYOD is a harmonious integration. It reflects the convergence of technological advancements and evolving work preferences. It is a collaboration that promises enhanced productivity, flexibility, and inclusivity. By doing so it paves the way for a future where work is not confined to physical spaces or specific devices but is a seamless and empowering experience.
Empowering Employees: Education and Training
In the realm of BYOD policies, the role of employee education and training is paramount. It is the cornerstone that ensures the secure and responsible use of personal devices within the professional environment. The integration of personal devices in the workplace brings forth a myriad of benefits. It also opens the door to potential security vulnerabilities. It is through comprehensive education and training that employees can navigate this landscape safely and efficiently.
The Essence of Employee Training
Employee training is not just a formality; it is an essential component in the implementation of BYOD policies. It empowers employees with the knowledge and skills needed to protect both personal and company data from security risks and data breaches. By understanding the intricacies of security protocols and best practices, employees become active participants in the organization’s cybersecurity framework, contributing to a safer and more secure digital environment.
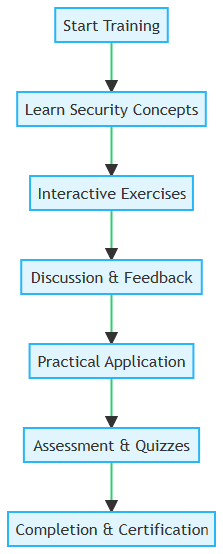
Interactive and Engaging Learning
The training program, as visualized in the provided diagram, is designed to be interactive and engaging. It incorporates a variety of learning methods, including practical exercises, discussions, and feedback sessions, allowing employees to grasp and apply security concepts effectively. This multifaceted approach caters to different learning preferences, ensuring that every employee, regardless of their technical proficiency, can comprehend and implement the learned security measures.
Practical Application and Assessment
Beyond theoretical knowledge, the training emphasizes practical application, allowing employees to implement the learned security practices in real-world scenarios. This hands-on approach is complemented by assessments and quizzes designed to evaluate the employees’ understanding and application of security protocols. It ensures that the knowledge acquired is not merely superficial but is ingrained and reflexive, enabling employees to respond promptly and appropriately to security threats.
Completion and Continuous Learning
The culmination of the training program is marked by completion and certification, symbolizing the employees’ proficiency in BYOD security best practices. However, the learning journey does not end here. The dynamic nature of the cybersecurity landscape necessitates continuous learning and adaptation. Employees are encouraged to stay abreast of the latest security trends and updates, fostering a culture of vigilance and proactive learning within the organization.
Conclusion
Empowering employees through education and training is a critical step in realizing the full potential of BYOD policies. It transforms employees from potential security liabilities into informed and responsible guardians of digital security. By instilling a deep understanding of security principles and fostering a commitment to best practices, organizations can ensure that the integration of personal devices is not a gateway to vulnerabilities but a conduit for innovation, flexibility, and enhanced productivity.
Endpoint and IoT Security: Safeguarding the Gateways
The amalgamation of the Internet of Things (IoT) and endpoint security is crucial for businesses aiming to secure their digital domains. This fusion of technologies has transformed operational methodologies, unlocking unparalleled opportunities for innovation and development. Nonetheless, it has also unveiled a plethora of security dilemmas requiring stringent protective strategies.
Endpoint and IoT Security Working Together
Our previous article provides an in-depth exploration of the essence of IoT endpoint security. It emphasizes the urgent necessity for businesses to bolster their defenses against the escalating cyber threats emerging amidst technological progress. It accentuates the significance of comprehending the intricate weave of IoT and endpoint security to shield enterprises from the inherent vulnerabilities and perils in IoT devices.
IoT and endpoint security collaboratively act as guardians of devices and data in a BYOD setting. They encounter shared threats and vulnerabilities, such as insecure firmware and frail credentials, capable of breaching the integrity of business networks and data. They also mutually advocate for security best practices and innovative solutions crucial for augmenting IoT endpoint security.
By assimilating and applying these insights, businesses can erect a robust defense structure, ensuring the secure amalgamation of IoT devices within their operational frameworks. This empowers them to harness the transformative essence of IoT while alleviating the correlated security risks, cultivating a secure and favorable atmosphere for innovation and advancement.
Conclusion: Endpoint and IoT Security Recommendations
In conclusion, the fortification of the interconnected sphere of IoT devices and endpoints is paramount. By integrating unified security protocols, amplifying authentication, performing routine security audits, implementing sophisticated encryption methods, and segregating IoT devices within specialized network segments, businesses can fortify themselves against the diverse threats in the interconnected digital realm. By adopting innovative solutions and selecting the optimal IoT endpoint security solution, businesses can navigate securely through the digital era, exploiting the extensive capabilities of IoT innovations while maintaining a vigilant defense against the lurking shadows of cyber threats.
BYOD Policy in Action: Real-life Examples
the practical implementation of BYOD policies has proven to be transformative, offering insights into the tangible benefits and potential pitfalls of this approach. Let’s explore a couple of generalized real-life examples to illustrate the practical applications and outcomes of implementing BYOD policies.
Example 1: A Small Marketing Agency
A small marketing agency, aiming to enhance flexibility and employee satisfaction, decided to implement a BYOD policy. The agency’s diverse team, consisting of graphic designers, content creators, and SEO specialists, embraced the opportunity to use their devices. The BYOD policy led to improved productivity and job satisfaction, as employees felt more comfortable and efficient using their own devices. However, the agency faced challenges in securing a variety of devices and operating systems, requiring the implementation of robust security measures and employee training to mitigate potential security risks and data breaches.
Example 2: A Local Retail Business
A local retail business adopted a BYOD policy to streamline operations and reduce overhead costs. The sales team, armed with their devices, could quickly access inventory data, process transactions, and communicate with the back office, enhancing customer service and operational efficiency. The implementation of BYOD allowed the business to save on hardware costs and adapt swiftly to the dynamic retail environment. However, the business had to confront the challenges of securing personal and work data on the same device, necessitating clear guidelines and stringent security protocols to protect sensitive company data.
In both examples, the implementation of BYOD policies resulted in enhanced flexibility, productivity, and cost savings. However, they also underscore the imperative need for comprehensive security measures, clear guidelines, and continuous employee education. These will help safeguard against the inherent risks of mixing personal and work devices. By learning from these real-life applications, small businesses can optimize the benefits of BYOD while minimizing the associated security risks. Thus, paving the way for a secure and innovative working environment.
Conclusion: The Future of BYOD for Small Business
BYOD policies have emerged as a double-edged sword, offering unprecedented flexibility and productivity gains while posing significant security risks. This article has traversed the multifaceted world of BYOD. It has explored its increasing relevance and the security minefield it presents. Finally, it has discussed the pivotal role of employee education and endpoint security in crafting a resilient and effective BYOD environment.
We’ve delved into the symbiotic relationship between remote working and BYOD. We have highlighted how this synergy can unlock transformative potential for small businesses. Real-life examples have illustrated the practical applications and outcomes of implementing BYOD policies. These examples offer insights into the tangible benefits and potential pitfalls of this approach.
Looking ahead, the future of BYOD policies is intertwined with the continuous advancements in technology and the shifting paradigms of work. Small businesses must stay abreast of the emerging trends and developments in BYOD, adapting their strategies to leverage the opportunities while mitigating the risks. The integration of advanced security measures, continuous employee training, and robust BYOD policies will be paramount in navigating the evolving BYOD landscape.
We invite you to join the conversation and share your thoughts, experiences, and questions about BYOD policies in the comments section below. Have you implemented a BYOD policy in your small business? What challenges have you encountered, and how have you overcome them? Let’s foster a community of learning and exchange, empowering each other to harness the full potential of BYOD in a secure and innovative manner.
The post Unlock BYOD Benefits: Policy Guide for Small Business 2023! appeared first on Endpoint Security.
*** This is a Security Bloggers Network syndicated blog from Endpoint Security authored by Michael Toback. Read the original post at: https://smallbizepp.com/byod-policy/?utm_source=rss&utm_medium=rss&utm_campaign=byod-policy
Original Post URL: https://securityboulevard.com/2023/09/unlock-byod-benefits-policy-guide-for-small-business-2023/
Category & Tags: Endpoint,Security Bloggers Network,Endpoint security – Endpoint,Security Bloggers Network,Endpoint security
Views: 0





















































