Source: socprime.com – Author: Steven Edwards
In threat detection, time is everything. Especially when identifying tools like NimScan—a known Potentially Unwanted Application (PUA) often associated with reconnaissance or malicious scanning activities. Microsoft Sentinel provides detection rules for such threats using Kusto Query Language (KQL), but understanding their full scope at a glance can be time-consuming.
That’s where Uncoder AI’s Full Summary comes into play. This AI-powered capability translates complex Sentinel queries into actionable plain-English summaries—boosting SOC efficiency by removing the guesswork.
The Detection Logic: Tracking NimScan Executions
The Microsoft Sentinel rule featured in this case is built to detect:
- Any process execution where the image name ends with
NimScan.exe - Or, file hash matches known IMPHASH values tied to NimScan variants
This simple yet effective rule can quickly flag suspicious command-line scans—whether the binary name is unchanged or the threat actor attempts to disguise it with a renamed executable.
Input we used (click to show the text)
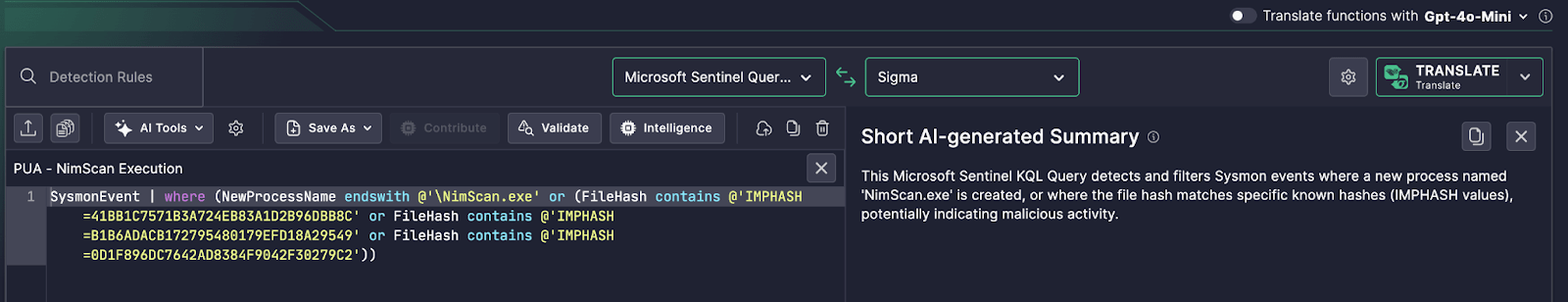
SysmonEvent | where (NewProcessName endswith @'NimScan.exe' or (FileHash contains @'IMPHASH=41BB1C7571B3A724EB83A1D2B96DBB8C' or FileHash contains @'IMPHASH=B1B6ADACB172795480179EFD18A29549' or FileHash contains @'IMPHASH=0D1F896DC7642AD8384F9042F30279C2'))
AI Output (click to show the text)
This Microsoft Sentinel KQL Query detects and filters Sysmon events where a new process named 'NimScan.exe' is created, or where the file hash matches specific known hashes (IMPHASH values), potentially indicating malicious activity.
Why It Matters
IMPHASH detection plays a critical role when attackers rename binaries. Even if the file is rebranded, its internal structure remains the same—allowing security teams to match it by hash.
NewProcessName detection ensures coverage when NimScan is run under its original identity, commonly found in red team toolkits or early-stage malware delivery.
Operational Benefits with Short Summary
With Uncoder AI’s Short Summary, threat hunters and SOC analysts can:
- Instantly understand the intent and scope of the detection
- Align known threats (like NimScan) to file behaviors or hashes
- Share insights across teams without requiring deep KQL expertise
- Respond faster with higher confidence
In short, what used to require manual inspection now takes just seconds—reducing dwell time and boosting the speed of your detection pipeline.
Original Post URL: https://socprime.com/blog/uncovering-pua-nimscan-activity-with-full-summary-in-uncoder-ai/
Category & Tags: Blog,SOC Prime Platform,Full Summary,Uncoder AI – Blog,SOC Prime Platform,Full Summary,Uncoder AI
Views: 2




















































