Source: socprime.com – Author: Eugene Tkachenko
In today’s threat landscape, when the number and sophistication of cyber attacks are constantly rising, threat actors are targeting the most secure and critical systems across continents and industries. Organizations are continually improving their cyber defense posture, migrating to cloud-based security solutions that reportedly enhance real-time threat detection capabilities. Yet, as adversaries adopt new approaches, organizations dealing with sensitive, classified, and mission-critical data—such as critical industrial control systems, government and military networks, and financial and healthcare institutions—must have the most efficient measures in place to protect against breaches.
Why Air-Gapped Networks Are Not Immune to Threats?
Air-gapped networks for mission-critical data have long been a trusted solution, and along with strong regulations and compliance requirements, they are designed to keep crucial systems isolated from the Internet and any external systems or networks.
Such isolated systems are designed to maintain high levels of security by being physically or logically disconnected from the internet and external networks and systems. However, as a security professional, you know that this isolation brings challenges. In practice, despite their separation, air-gapped networks still require the usage of peripheral equipment, software updates, patches, and legitimate data transfers, which expose the isolated environment to supply chain attacks, insider threats, and social engineering, among other vectors. This creates new challenges for security operations, particularly threat detection and incident response.
What is SOC Prime’s Uncoder?
Since its release in 2018, Uncoder IO has become a trusted tool in the cybersecurity community for enabling vendor-agnostic threat detection by translating Sigma rules into multiple language formats. Today, SOC Prime offers three versions of its legendary Uncoder tool that has been supporting detection engineers:
Uncoder AI – an IDE and Augmented Intelligence co-pilot for detection engineers, SOC analysts, and threat hunters. You can code your detection rules using best-practice templates, build your research on top of collective cyber threat intelligence, and enrich your detection with information about recommended configurations, suggested triage procedures, and false positives. As part of the SOC Prime Platform, a SOC 2 Type II compliant SaaS, Uncoder AI is available for integrations and API support for organizations that use the SOC Prime Platform. Also, it supports contributions to the collective cyber defense via the Threat Bounty Program.
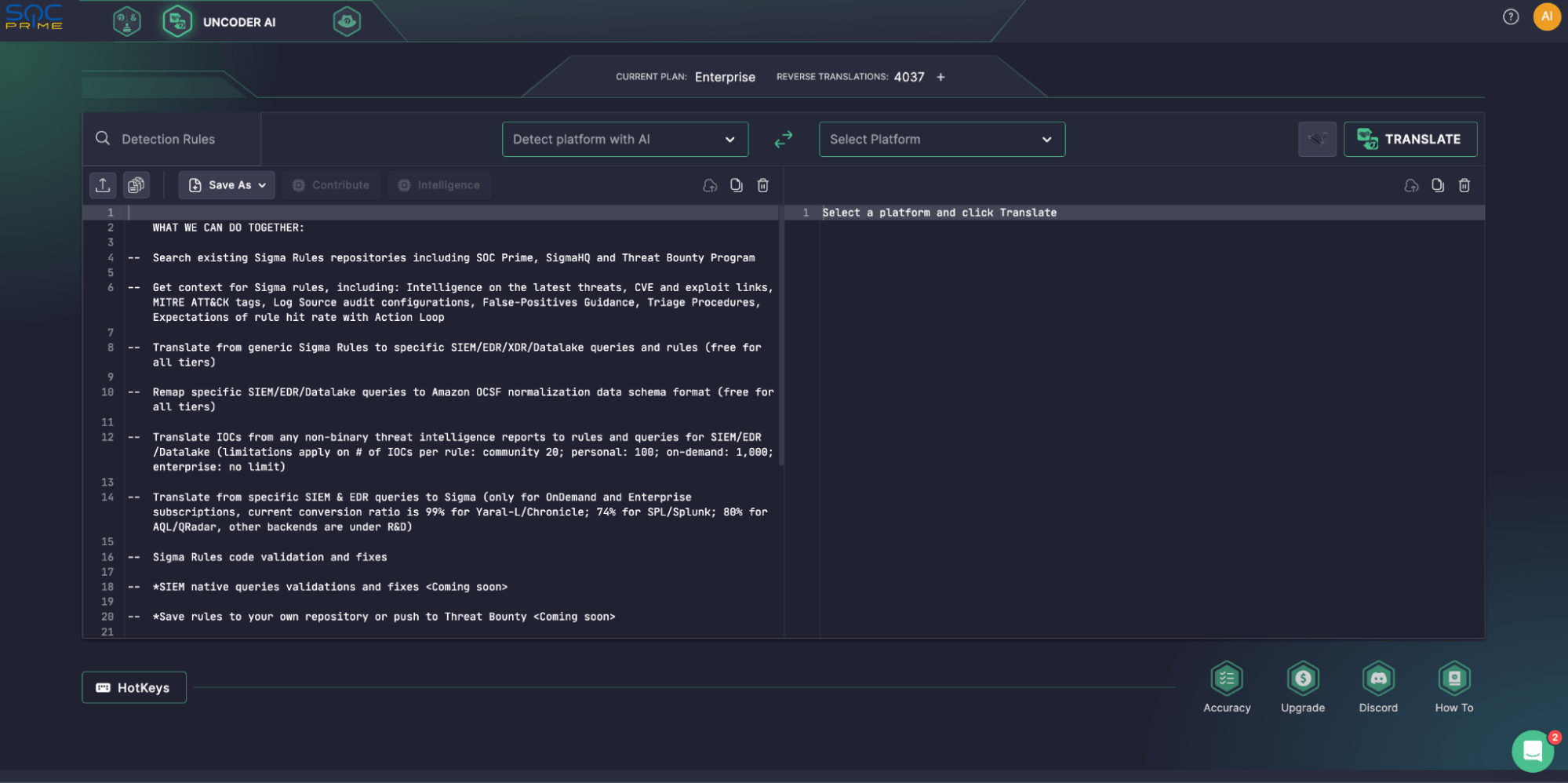
Uncoder IO is a free and private online translation engine (without registration and cookies) that allows one-click translations of generic detections (Sigma and Roota rules) and IOCs to various SIEM, EDR, and Data Lake formats.
Uncoder IO Public Beta – is an open-source version of Uncoder IO that can be installed and run on-prem and is distributed under Apache 2.0. Commercial Edition license.
Benefits of Uncoder On-Prem
Effective threat detection and response require trusted tools that streamline the daily operations of security teams, regardless of the architectural peculiarities of the environments they operate in. The on-prem version of Uncoder supports teams that defend isolated networks serving as a reliable and secure tool for converting detection rules and IOCs into actionable SIEM-specific queries.
Do you need an easy-to-use tool that works just within your network? Uncoder IO On-Prem brings the same intuitive and user-friendly experience as its online counterpart, ensuring that even teams operating in isolated networks can take advantage of its capabilities for streamlined threat detection. With the ability to automatically convert Roota and Sigma rules and IOCs into queries on their workstations, security specialists working in air-gapped networks can handle the detection tasks more effectively, gaining operational time to focus on more complex threats and strategic objectives.
How do you manage detection rules in a closed network? In networks with strict restrictions regarding access to outside networks, it can be challenging to respond effectively and timely to cyber threats. Do you maintain your own Sigma rules library within your organization or rely on imported external rules? With SOC Prime’s on-prem translator, you can keep using the queries automatically converted from Sigma or Roota rules or IOCs and remain compliant with your security protocols. This also ensures that detection rules can be applied consistently and all systems of your organization are protected against threats.
How do you ensure that critical data remains internal? In networks designed to protect highly sensitive data, the information about how these systems are defended is equally crucial. Detection rules, configuration details, and peculiarities of the local customizations, such as exceptions to reduce false positives, can expose security gaps of the defended network if leaked. The on-prem setup of Uncoder within your isolated network allows you to react to threats promptly without the risk of exposure of your defense strategies.
Will your team benefit from the tool that converts IOCs to queries offline? While air-gapped networks by design do not have real-time access to external feeds or the integrations that provide real-time attack surface visibility, SOC teams may be spending excessive amounts of time coding queries from the indicators of compromise without access to Uncoder IO and Uncoder AI. Your team can overcome this inconvenience by using Uncoder On-Prem.
How to Start with Your Private Uncoder?
With different versions of the Uncoder tool, SOC Prime offers a secure and flexible solution that perfectly fits the needs of security specialists working in various environments. However, when you are part of the security team handling classified or highly sensitive data and within strict security regulations, the ability to deploy Uncoder IO in-house enhances operational efficiency and security.
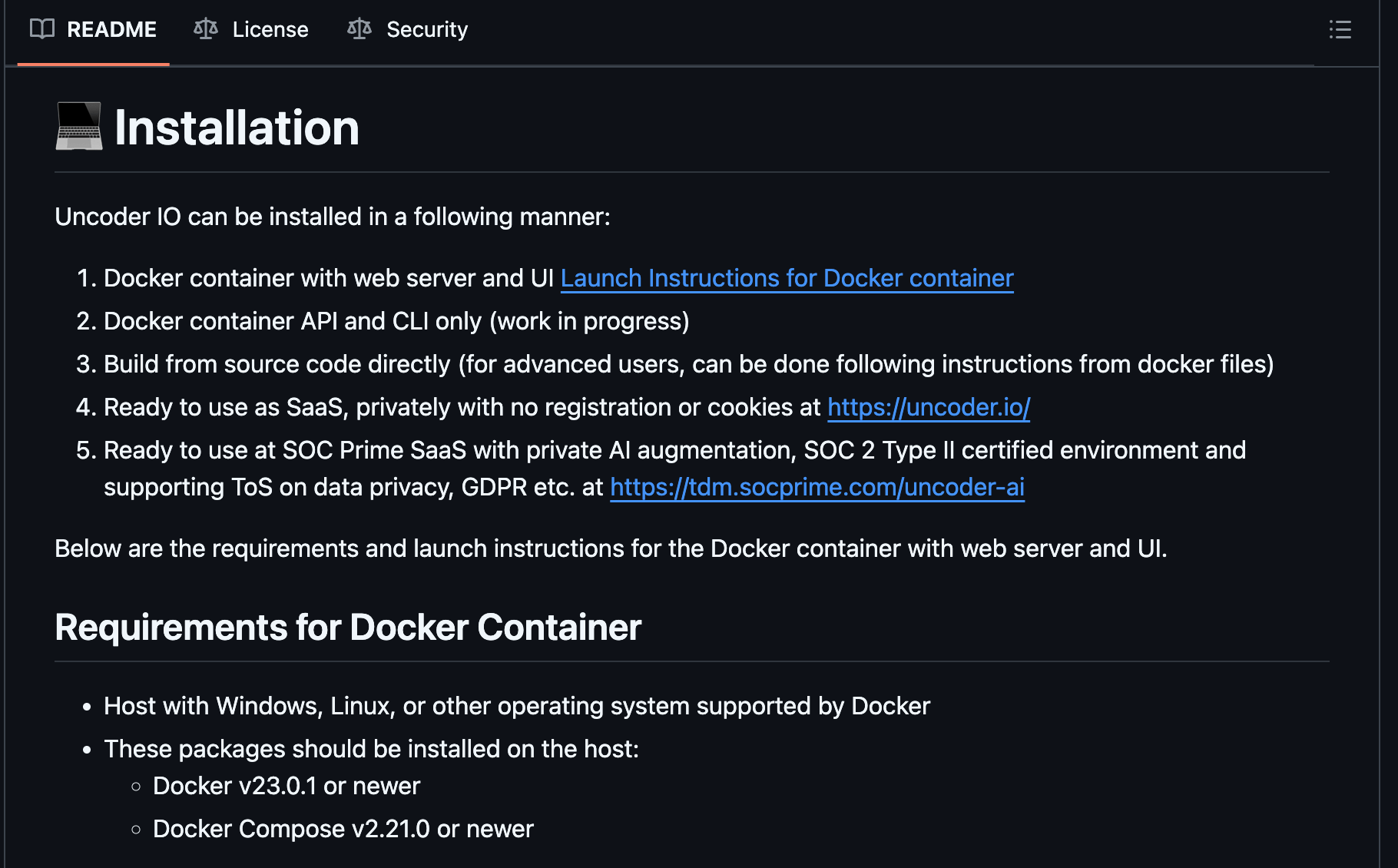
The official SOC Prime’s GitHub repo provides comprehensive information on the installation and supported technologies.
- Download the Uncoder IO files from the official SOC Prime’s Uncoder repository on GitHub.
- Set Up: unpack the archive and run instructions for the Docker container from the command line.
- Access: Once the Docker setup completes, you can access your private instance by visiting
http://localhost:4010/on your local browser.
Implementing Uncoder IO for operations in air-gapped environments provides significant benefits for SOC teams managing threat detections. Its ease of use and the ability to convert generic rules like Roota and Sigma and IOCs empower teams to maintain effective and timely detection capabilities in environments with the highest security standards.
Original Post URL: https://socprime.com/blog/uncoder-for-flexible-threat-detection-from-cloud-to-air-gapped-networks/
Category & Tags: Blog,SOC Prime Platform,Detection Content,Sigma,Uncoder,Uncoder AI,Uncoder IO – Blog,SOC Prime Platform,Detection Content,Sigma,Uncoder,Uncoder AI,Uncoder IO
Views: 0