Source: hackread.com – Author: Deeba Ahmed.
KEY POINTS
- Cybersecurity researchers at ReversingLabs found that hackers used malicious code to combine the Ultralytics AI library to mine cryptocurrency.
- Hackers exploited the library’s build system and injected XMRig mining software into updates 8.3.41 and 8.3.42.
- The attack used GitHub Actions Script Injection and fake pull requests to gain access to the system.
- With over 60 million downloads, the compromised library posed a risk, though the damage was limited to mining.
- Developers and users must verify software updates and sources to avoid similar incidents.
The latest research from ReversingLabs (RL) shared with Hackread.com, reveals that a popular AI library called “Ultralytics“ has been secretly mining cryptocurrency for someone else. This follows the recent discovery of the malicious aiocpa Python package, which was spreading an infostealer.
On December 4th, an update (version 8.3.41) for Ultralytics hit the Python Package Index (PyPI), a repository for Python software. However, something else also hit the repository: Hackers had infiltrated the project’s build environment, which prepares the software for release.
The content in the GitHub repository did not match the content of the matching PyPI package, as malicious actors compromised the build environment and injected malicious code after the code review process was completed.
The tampered code downloaded a program called XMRig, a cryptocurrency miner. The worst part, according to RL’s report, is that even a supposed “fix” (version 8.3.42) released the next day was also infected.
That’s because the project’s maintainers failed to locate the compromise, resulting in version 8.3.42, intended to address the incident and serve as a safe upgrade, containing the same malicious code. A clean version, 8.3.43, was released on the same day, resolving this supply chain attack.
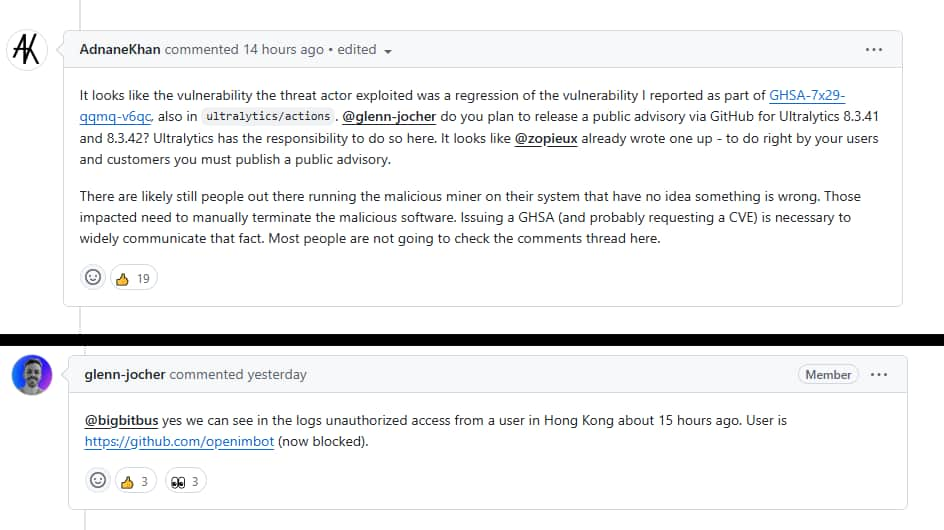
In case you are wondering how the hackers got in, it all started with exploiting a GitHub Actions Script Injection to enter the build environment of a trusted npm package, @solana/web3.js. This injection allowed a malicious actor to create a fork of any repository using ultralytics/actions and craft a pull request from a branch with injection payload code in its title.
Next, two maliciously crafted pull requests, #18018 and #18020, were designed to enable backdoor access to the compromised environment. The user account behind this pull request, openimbot, and the remote connection established after the execution of the malicious payload were initiated from Hong Kong, based on information provided by ultralytics maintainers. By creating fake pull requests with cleverly crafted titles, actors tricked the system into running their malicious code.
Impact: 60 million downloads and 30,000 GitHub stars
This attack had the potential to impact millions considering that Ultralytics boasts over 60 million downloads and 30,000 GitHub stars, indicating its widespread use. Thankfully, the damage seems limited to cryptocurrency mining.
However, this incident shows how vulnerable software supply chains can be. Malicious actors could have easily injected more dangerous code, like backdoors or remote access tools. This means, developers must be cautious at all stages to protect AI projects.
It also shows the importance of software security, emphasizing the need for developers to double-check code changes from untrusted sources, and users to download software from trusted sources and keep it updated.
Original Post url: https://hackread.com/ultralytics-ai-library-compromised-for-cryptomining/
Category & Tags: Security,Cryptocurrency,Malware,Crypto,Cryptominer,PyPI,Python,Ultralytics AI – Security,Cryptocurrency,Malware,Crypto,Cryptominer,PyPI,Python,Ultralytics AI
Views: 3




















































