Source: socprime.com – Author: Veronika Telychko
The UAC-0099 hacking collective, active in cyber-espionage campaigns against Ukraine since mid-2022, has reemerged in the cyber threat arena. The CERT-UA team has recently investigated a series of cyber-attacks linked to the UAC-0099 group targeting government authorities, defense forces, and enterprises within Ukraine’s defense industry sector, leveraging the MATCHBOIL loader, the MATCHWOK backdoor, and the DRAGSTARE stealer.
Detect UAC-0099 Activity Using MATCHBOIL, MATCHWOK & DRAGSTARE Malware
The growing wave of highly persistent cyber-espionage campaigns leveraging phishing as the initial attack vector, adopting evolving TTPs, and linked to the UAC-0099 hacking group, encourages security teams to enhance cybersecurity awareness and strengthen their organizational defenses. To help organizations safeguard against emerging attacks by UAC-0099 leveraging targeting the public and defense sector and covered in the latest CERT-UA research, SOC Prime Platform has curated a dedicated list of relevant detection content.
Click the Explore Detections button to explore the entire collection of relevant Sigma rules mapped to MITRE ATT&CK®, enriched with actionable CTI and operational metadata, and ready to deploy in the selected language format compatible with your SIEM, EDR, and Data Lake in use.
Alternatively, security engineers can also apply the corresponding “MATCHBOIL,” “MATCHWOK,” or “DRAGSTARE” custom tags to search for dedicated detections against cyber-attacks covered in the latest CERT-UA heads-up. For more relevant detection content, teams can use the “UAC-0099” custom tag to enhance proactive defenses against the group’s persistent activity.
Security engineers also use Uncoder AI to speed up IOC correlation and hunt for indicators linked to UAC-0099 threats based on the relevant CERT-UA research. The platform allows automatic conversion of IOCs from any non-binary format into custom hunting queries tailored to the selected SIEM or EDR solution. On the Generate tab in Uncoder AI, past threat intel, select Threat Report/IOCs > IOC Query, then select the platform, and instantly get the custom IOC query ready to run in your chosen environment.
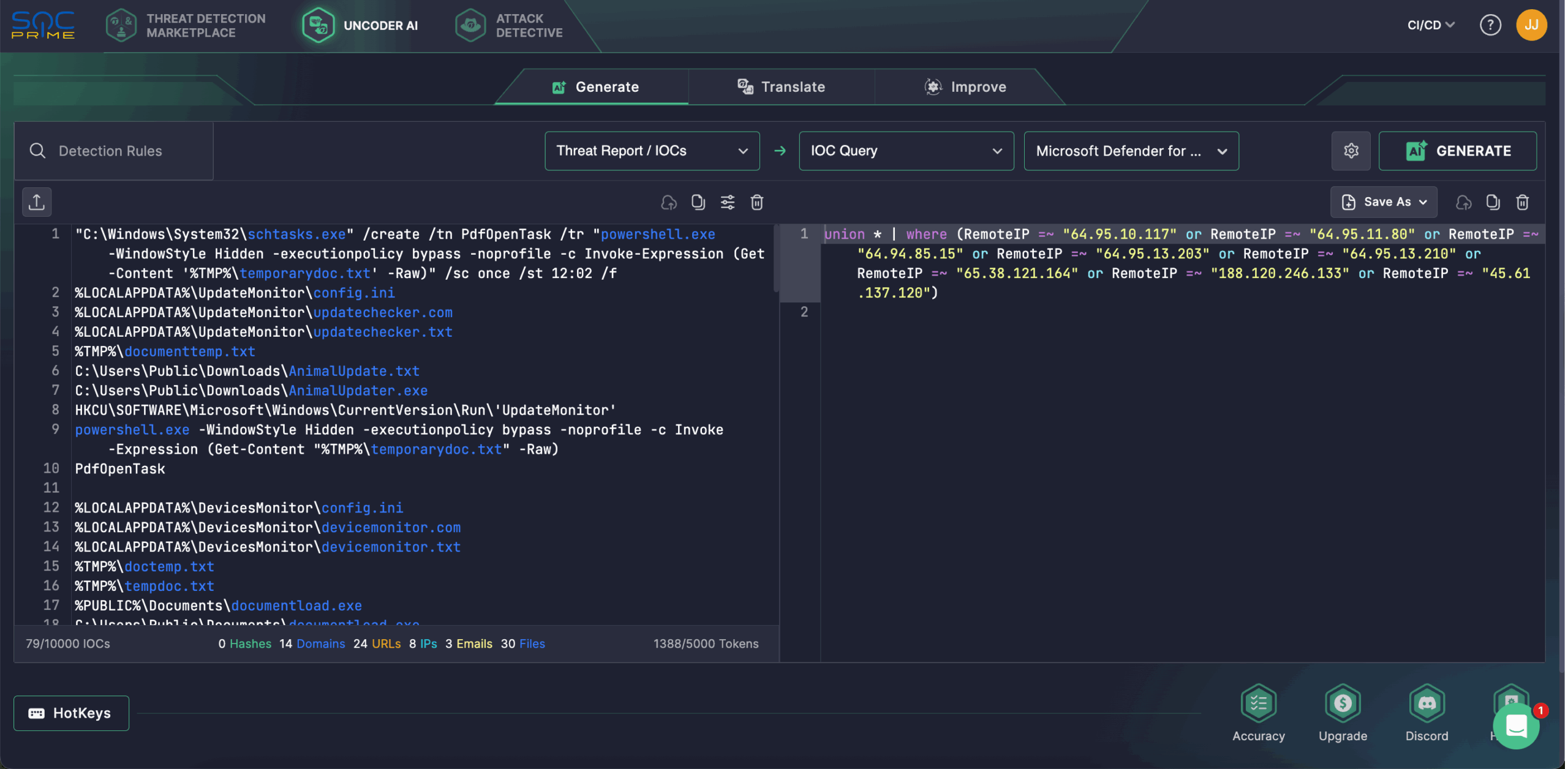
UAC-0099 Activity Analysis
The nefarious UAC-0099 hacking collective has been launching cyber-espionage operations against Ukraine for over three years, mainly relying on a phishing attack vector to gain initial access and employing diverse adversary tools, including multiple malware samples, loaders, and stealers. Between 2022 and 2023, attackers obtained unauthorized remote access to numerous computers within Ukrainian entities, aiming to collect intelligence from the affected systems. During November–December 2024, defenders recorded a surge in the group’s malicious activity, targeting the Ukrainian public sector through phishing campaigns and deploying LONEPAGE malware.
On August 4, 2025, CERT-UA issued a novel alert notifying defenders of a wave of new cyber-attacks against Ukrainian state bodies, defense forces, and defense industry enterprises orchestrated by UAC-0099.
The initial attack stage involves the distribution of phishing emails, primarily sent via UKR.NET. These emails contain links to legitimate file-sharing services (sometimes shortened via URL shorteners), leading to the download of a double archive that includes an HTA file. The latter contains an additionally obfuscated VBScript that creates on the infected machine a text file with HEX-encoded data (“documenttemp.txt”), a text file with PowerShell code (“temporarydoc.txt”), and a scheduled task (“PdfOpenTask”).
The scheduled task “PdfOpenTask” is designed to read and execute the PowerShell code with the primary function to convert the HEX-encoded data into bytes, write them to a file with the “.txt” extension, rename the latter to an EXE file (“AnimalUpdate.exe”) in the same directory, and create a scheduled task to execute it.
As a result, the MATCHBOIL loader (likely replacing LONEPAGE) is deployed on the compromised system. Incident response revealed that additional tools, such as the MATCHWOK backdoor and the DRAGSTARE stealer, may also be downloaded onto the machine.
MATCHBOIL is a C #-based malware that downloads additional payloads to the infected machine and creates a registry key in the “Run” branch to enable their execution.
Upon execution, it collects basic system information, including the CPU hardware ID, BIOS serial number, username, and the network interface’s MAC address. These values are concatenated and used in the “SN” header of HTTP requests. MATCHBOIL communicates with the C2 server over HTTP, adding custom headers while the “User-Agent” header contains a hardcoded string. To download payloads, the malware issues an HTTP GET request to a specific URI, decodes them from HEX and BASE64, and writes them to a .com file. The C2 address is also retrieved via HTTP GET and stored in a configuration file. Persistence for MATCHBOIL is ensured by a scheduled task created during the initial execution of the HTA file delivered in the phishing email archive.
MATCHWOK is a C# backdoor designed to execute PowerShell commands by compiling .NET programs at runtime and passing the commands to the PowerShell interpreter via STDIN. The command output is saved to %TEMP%tempres and transmitted to the C2 server over HTTPS. The commands to be executed are AES-256 encrypted and embedded between
