Source: socprime.com – Author: Veronika Telychko
The notorious russian state-sponsored threat group UAC-0001 (also tracked as APT28) has once again surfaced in the cyber threat landscape. After CERT-UA’s late June alert exposing the group’s use of the COVENANT framework and the BEARDSHELL backdoor, UAC-0001 has maintained its focus on Ukraine. CERT-UA now reports a new wave of cyber-attacks targeting the security and defense sector, this time leveraging the LAMEHUG tool, which incorporates an LLM.
Detect UAC-0001 (APT28) Attacks via LLM-Powered LAMEHUG Malware
The russia-affiliated hacking groups remain a persistent threat to cyber defenders, continuously adapting their TTPs to enhance stealth and bypass detection. Since the beginning of the full-scale invasion of Ukraine, the aggressor has intensified its APT attacks, using the conflict as a testing ground for emerging offensive strategies.
Register for SOC Prime Platform to stay ahead of increasing attacks linked to the nefarious russia-backed hacking collective known as UAC-0001 (APT28). SOC Prime Team curates a selection of Sigma rules addressing the ongoing group’s campaign against the security and defense sectors using AI LLM for data theft covered in the latest CERT-UA alert. Press the Explore Detections button to reach the corresponding detection stack enriched with actionable CTI, aligned with MITRE ATT&CK®, and compatible with multiple SIEM, EDR, and Data Lake technologies. For the ease of search, this Sigma rule collection is tagged “CERT-UA#16039” based on the relevant CERT-UA alert identifier.
For more Sigma rules to detect attacks orchestrated by this russia-linked group, security teams can search the Threat Detection Marketplace library using the “UAC-0001” and “APT28” tags. Microsoft Defender for Endpoint (MDE) customers can also enable Bear Fence, a plug-and-play, always-on service fully integrated with the customers’ MDE to protect the organization from russia-backed APT threats. Automatically hunt for APT28 and 48 more russian nation-state actors through an exclusive Attack Detective scenario using 242 hand-picked behavior rules, over 1 million IOCs, and a dynamic AI-driven TTP feed.
Security engineers can also rely on Uncoder AI to create Roota & Sigma Rules in under 30 seconds, document and optimize code, gain expertise in 56 detection languages, generate Attack Flows and ATT&CK mapping with AIML. By leveraging threat intel from the latest CERT-UA#16039 alert, teams can auto-convert relevant IOCs into custom queries ready to hunt in the selected SIEM or EDR format.
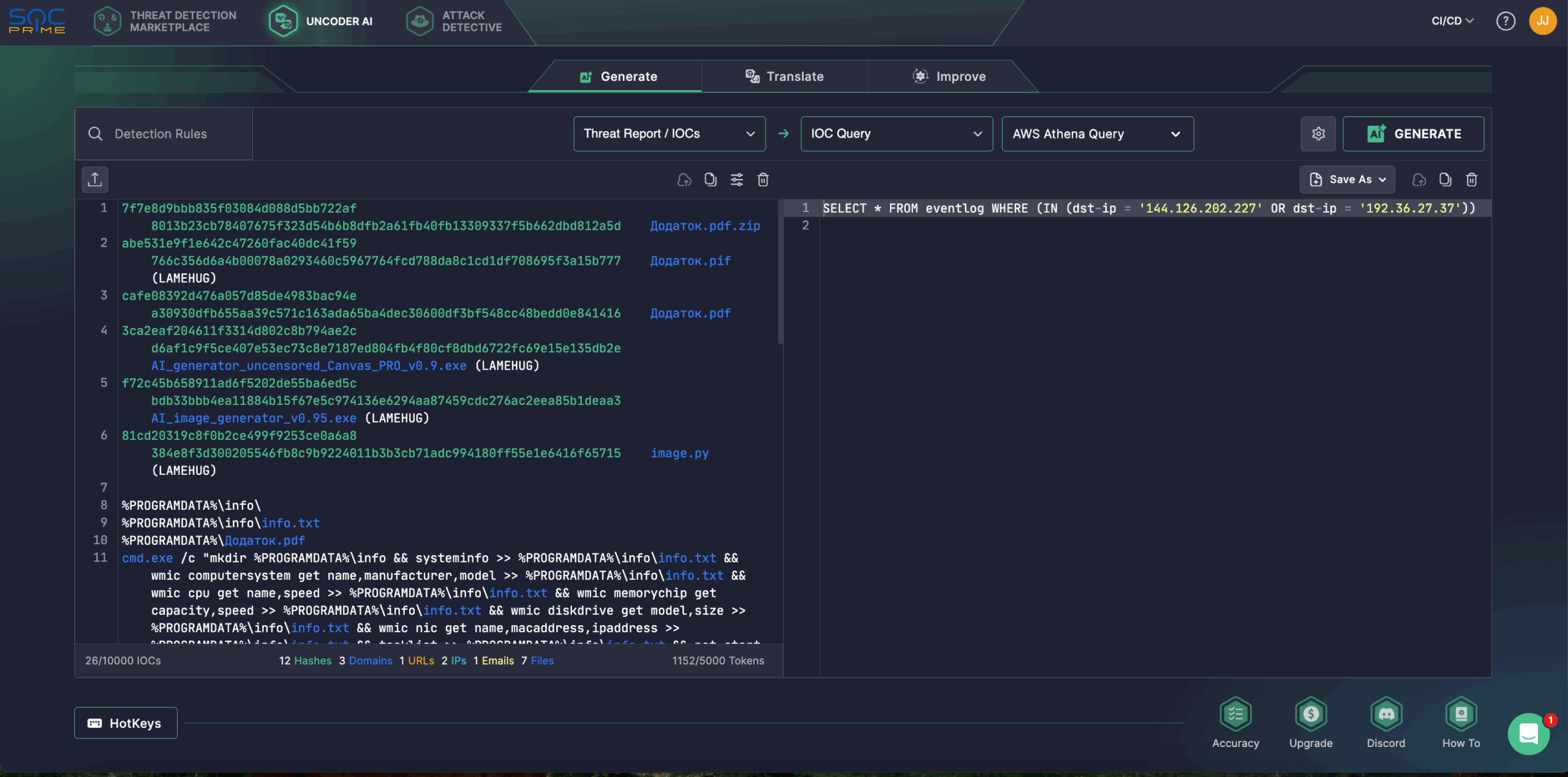
UAC-0001 (APT28) Latest Activity Overview
On July 10, 2025, CERT-UA received information regarding the distribution of phishing emails among executive authorities, impersonating officials from the relevant ministry. These emails contained an attachment titled “Додаток.pdf.zip” disguised as a legitimate document. With moderate confidence, CERT-UA attributes this activity to UAC-0001 (APT28).
APT28, aka UAC-0001, also tracked as Fighting Ursa, Fancy Bear, Forest Blizzard, or STRONTIUM, has maintained a persistent focus on Ukraine’s public sector, often leveraging phishing campaigns and software vulnerability exploits as its primary methods of attack.
The ZIP archive leveraged by adversaries in the latest campaign included an executable file with a “.pif” extension, named identically to the archive. The file was built using PyInstaller from Python source code and has been classified by researchers as a malicious software tool named LAMEHUG.
During the incident investigation, at least two additional variants of this malware were discovered, “AI_generator_uncensored_Canvas_PRO_v0.9.exe” and “image.py,” which differ in how they exfiltrate data from compromised machines. It is worth noting that the phishing emails were distributed using a compromised email account, while the C2 infrastructure was deployed on legitimate but compromised resources.
A distinctive feature of LAMEHUG is its use of an LLM, which generates executable commands based on their textual descriptions. LAMEHUG is a Python-based malware that leverages the LLM Qwen 2.5-Coder-32B-Instruct via the huggingface[.]co API to generate system commands from predefined text descriptions. It collects system information, such as hardware, processes, services, and network connections. Further, it stores the data in %PROGRAMDATA%infoinfo.txt, and recursively searches for Microsoft Office, TXT, and PDF files in the Documents, Downloads, and Desktop directories, and then copies them to %PROGRAMDATA%info. The stolen data is exfiltrated using SFTP or HTTP POST requests, depending on the malware version.
As APT28 intensifies its attacks on Ukraine’s security and defense sectors and begins testing advanced LLM-powered malware, proactive cyber defense becomes critically important. SOC Prime equips security teams with a complete product suite backed by AI, automation, and real-time threat intelligence to outscale cyber threats and strengthen the organization’s cybersecurity posture.
MITRE ATT&CK Context
Using the MITRE ATT&CK offers detailed insight into the latest UAC-0001 (APT28) campaign targeting the security and defense sector with LAMEHUG malware. The table below outlines all relevant Sigma rules mapped to the associated ATT&CK tactics, techniques, and sub-techniques.
Original Post URL: https://socprime.com/blog/detect-uac-0001-attacks-with-lamehug-malware/
Category & Tags: Blog,Latest Threats,APT28,CERT-UA,CERTUA,Phishing – Blog,Latest Threats,APT28,CERT-UA,CERTUA,Phishing
Views: 12



















































