Source: www.csoonline.com – Author:
Security leaders offer advice on researching, piloting, and implementing the most frequently cited cyber tech pilots, according to our latest CSO Security Priorities Study.
Ask almost any CISO and they will tell you the security landscape just keeps getting more complex. New products arise, technology categories blur, vendors gobble up competitors or venture into adjacent markets, and every once in a while a seismic advance like generative AI comes along to shake up everything.
But with threat vectors constantly evolving and enterprise IT transforming to introduce new attack surfaces, CISOs must continuously research and assess new solutions to advance their defenses and keep up with the threatscape.
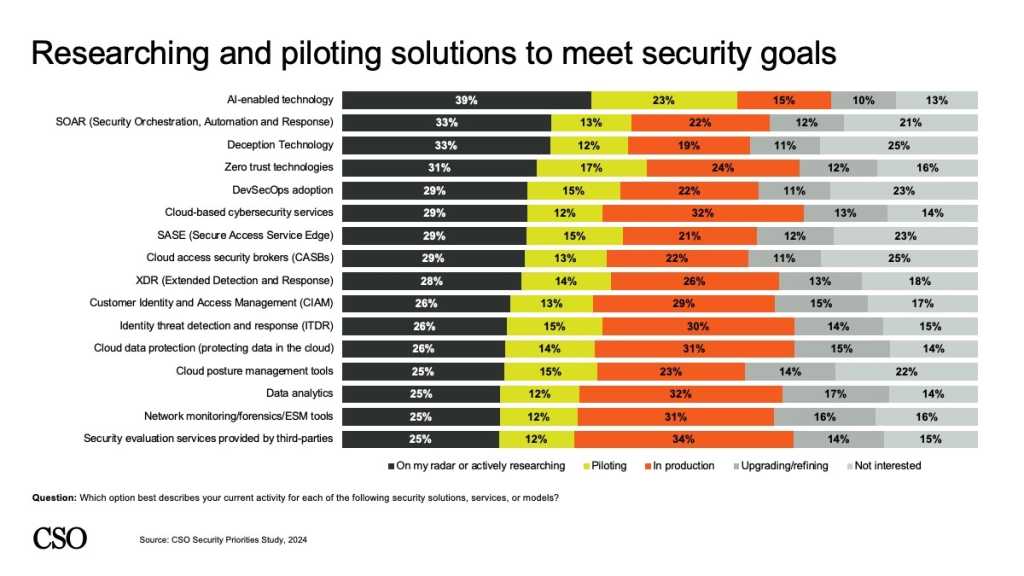
As part of our “CSO Security Priorities Study,” we surveyed over 870 CISOs, CSOs, and other cybersecurity leaders about where their organization stood with a range of technologies core to enterprise security today. Far and away the most popular category under investigation is AI-enabled technologies, cited as being researched or piloted by 62% of CISOs — followed by zero trust (48%); security, orchestration, automation, and response (SOAR) (46%); and deception tech (45%).
DevSecOps and SASE, each cited by 44% of CISOs, are also popular areas for investigation, with XDR (42%), CASB (42%), cloud-based cybersecurity services (41%), and identity threat detection and response (ITDR) (41%) rounding out the top 10.
Foundry / CSO
While there is overlap between the various categories surveyed, this diversity captures the challenge CSOs face in the marketplace: the overwhelming number of technologies and solutions to choose from and then integrate seamlessly into their existing tech stack.
Overcoming the paradox of choice in cybersecurity
Pascal Menezes, CTO of MEF, summarizes the issue well: “The problem with cybersecurity is that they’re all little parts and pieces that enterprises have to kind of glue together and make it work. …The world’s changing rapidly,” he says.
In this environment, cybersecurity leaders may fall into a common trap, pursuing technologies based on market hype rather than business needs, resulting in a hodgepodge of security solutions.
To circumvent this problem, Achyuth Krishna, head of IT and infosec at Whatfix, advises looking inward instead of outward. While particular technologies may address specific threats and vulnerabilities, their impact is inherently tied to the nature and priorities of the business. Thus, according to Krishna, cybersecurity leaders must understand information security risks as they align with their organization’s objectives and operations.
“The first priority should be identifying and addressing blind spots in the security landscape, as these often pose the greatest risks,” he says, adding that CISOs should then focus research and piloting on technologies that address these vulnerabilities as part of a proactive, business-aligned approach to cybersecurity.
For Krishna, this means piloting cloud access security brokers (CASBs) at Whatfix, which has another six commonly researched areas already in production: DevSecOps, cloud-based cybersecurity services, cloud data protection, data analytics, third-party security evaluation services, and cloud posture management tools.
Adopting cutting-edge technologies — in phases
When cybersecurity leaders feel a new technology is important for their security posture, they may often rush a solution to production, leading to poor or haphazard results.
Pablo Riboldi, CISO of BairesDev, recommends a phased approach. Today, the provider of nearshore tech talent is implementing zero-trust technologies to continuously verify who’s accessing its systems and to ensure its devices meet security standards, Riboldi says. The goal is to minimize risks from unauthorized access and lateral movement within its network.
“For our zero-trust strategy, we started with the high-risk applications and then widened our focus to include more access scenarios. We keep track of how we’re doing by looking at access success rates and the number of incidents we’ve reduced,” he says.
BairesDev is also taking a phased approach to implementing secure access service edge (SASE), a term coined by Gartner when companies were shifting to remote and hybrid work en masse and needed secure access from various environments. Riboldi says BairesDev’s SASE implementation will centralize its network and security services in one cloud-based solution, giving the security team greater visibility into their distributed workforce.
“When it comes to SASE, we made it a priority to integrate it with our existing cloud-based services and provided user training to help everyone adjust easily. We’re also working closely with stakeholders and doing regular check-ins to ensure these technologies align well with our business goals,” he says.
Understanding tech-specific implementation challenges
With security vendors rapidly enhancing solutions with AI — and hyping them — CISOs are faced with a firehose of options to investigate, many of which require the greater scrutiny that a version 1.0 product requires.
Because a key selling point of “AI inside” is scale, IDC Asia Senior Research Manager Sakshi Grover advises CISOs who want an AI-enabled use case in their cybersecurity portfolio to first determine what they are trying to scale.
“Is the problem occurring with your [configuration management], your system identity and event management, identity, threat intelligence, or threat detection and response workloads? If you are able to figure out which tech you want to scale — what’s the problem on ground — that solves the majority of your problem,” she says.
Mital Patel, CIO of Caxton, says his company is implementing AI-enabled technology, especially around ITDR and XDR, for its user base of 100 to 125 employees.
“What we typically find is we give them technology, we give them access to systems, but we don’t know how they’re controlling their accounts, the devices, and anything related to the company,” he says.
This lack of transparency compounds the nature of cyberattacks against the fintech company, which occur when the company is most vulnerable, such as after work hours or on bank holidays.
AI-enhanced, the company’s security software now monitors login analytics, such as where a person is logging in from and what device they are using, to detect any abnormal activities and raise an alert. The goal is to create a self-service model because Caxton’s cybersecurity team is small and not on-site.
But the AI-enabled solution has taken time to prove effective, Patel says. In the first few months of implementation, Caxton received many false positives: activities that were flagged as vulnerabilities but were, in fact, legitimate business uses. These false positives wasted the team’s time.
Patel advises businesses exploring AI-enhanced technologies to pay close attention to parameters and give the solution time to understand and learn from your infrastructure. He also emphasizes the importance of feeding it relevant data.
“[AI-enabled solutions] can give you a lot of nonsense, a lot of noise that you don’t even respond to. So it’s basically having that granular throughput where you can actually see, ‘Okay, this is genuine information that I care about, the organization cares about, and this is how we handle it,’” Patel says.
Evaluating vendors
Evaluating and implementing external solutions carries many risks. With AI-based solutions, this is compounded.
IDC’s Grover says her research firm predicts that in the next year at least 20% of organizations will move gen AI use cases from proof-of-concept to production without conducting a risk-based assessment, leading to a “house of cards situation,” she says.
Vendors may not be immune to this practice, so Grover stresses that any vendor must be vetted through a litany of questions in the early stages relevant to its intended use.
“For example, if it comes to data: Who is going to use that data? Where is that data coming from? How is that data being used? How is it being collected?” she says.
If the CISO gets satisfactory answers to these questions, they should look at the metrics the vendor will track and project their return on investment, Grover says. “If you feel that those metrics can give you a good return on investment and you are assured of the vendor’s answer, then only go to the pilot stage,” she advises.
MEF’s Menezes suggests another shorthand for evaluating vendors: certifications. According to Menezes, examining a vendor’s certifications can help CSOs cut through the marketing speak.
“Because really, they all claim a whole bunch of stuff, but who knows what they can really do, right? Certification is third-party testing to ensure this stuff works,” he says.
As a global industry association, MEF offers vendor certifications that cover SASE and zero-trust technologies, but Menezes recommends looking for certs from a vendor regardless of category.
With certification, “everything is tested by a third party to make sure it works as it claims it should work. And certification by default means there’s some standardization that allows them to test these various use cases,” he says.
Prioritize with purpose
IDC’s Grover says each technology category mentioned in the “CSO Security Priorities Study” is generally crucial to all enterprises. In this view, organizations should not treat the categories as a menu of options but a list to prioritize to suit their needs.
For example, when asked where a cybersecurity organization should start from scratch, such as a startup that just received venture funding, she offered the following advice: “Once you have decided [between on-premises or cloud], the most important vision for cybersecurity you need to have is SASE because it gives you a methodology and a framework to protect your assets.”
Grover then advises researching threat detection and response, including incident management and vulnerability assessment and penetration testing (VAPT). “Last but not the least, identity — because, at the end of the day, you are going to interact with your clients, your partners, your employees, and other stakeholders from the board as well,” she says.
Regardless of the where your company is on its growth curve, security leaders should prioritize their pilots based on the underlying purpose of the technology: what they ultimately defend, Grover says.
To sharpen focus in a busy landscape, organizations may want to determine how a technology advances — or does not advance — the security posture of the area they are trying to strengthen.
“[The technologies] are basically protecting these five control points, which are your data, your network, your APIs and applications, your endpoint, and your identity,” she says. “All solutions are directly linked to these five control points.”
SUBSCRIBE TO OUR NEWSLETTER
From our editors straight to your inbox
Get started by entering your email address below.
Original Post url: https://www.csoonline.com/article/3626931/top-security-solutions-being-piloted-today-and-how-to-do-it-right.html
Category & Tags: IT Strategy, Security – IT Strategy, Security
Views: 5




















































