Source: www.cybertalk.org – Author: slandau
In this outstanding, in-depth article, Check Point’s Head of Cloud Security & DevSecOps, Jason Normanton, discusses public cloud trends in 2023.
Public cloud services are becoming increasingly popular and essential for enterprises that want to leverage the benefits of scalability, agility, innovation and cost-efficiency. According to Gartner, worldwide end-user spending on public cloud services is forecast to grow by 21.7%, totaling $597.3 billion in 2023, up from $491 billion in 2022.
Cloud computing is driving the next phase of digital business, as organizations pursue disruption through emerging technologies like generative artificial intelligence (AI), web and the metaverse.
In this blog post, we will explore some of the key public cloud trends identified by me during my time at Gartner and most recently at Check Point, a leading provider of cyber security solutions. We will also address the challenges and opportunities related to cloud usage, migration strategy, native application hosting, security, regulatory information and standards, as well as some of the notable security breaches that occurred in the cloud. Finally, we will provide 10 pieces of actionable advice for enterprises that want to optimize their cloud journey in 2023.
Cloud usage
According to a survey conducted by Flexera in 2022, AWS and Azure are the most dominant players in the public cloud market, with GCP being the third-largest provider in terms of market share. AWS and Azure both offer a comprehensive set of capabilities with global coverage. GCP is known for its strength in AI and machine learning, as well as its competitive pricing. Alibaba Cloud and Tencent Cloud are the leading cloud providers in China, with a strong presence in the Asia-Pacific region. Oracle Cloud is gaining traction among enterprises that use Oracle databases and applications. OpenShift is a popular platform for hybrid cloud and container-based deployments.
The following table shows the current enterprise public cloud adoption worldwide from 2017 to 2023, by service: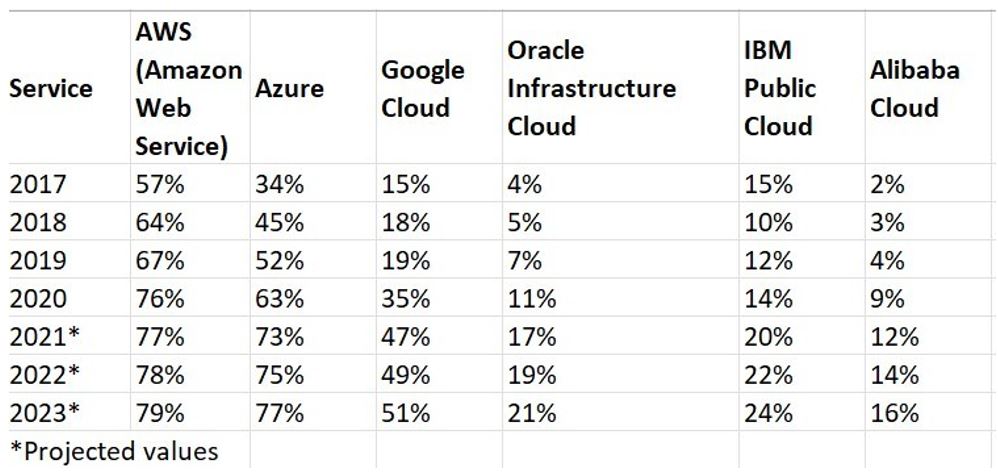
It should be noted that this is an average rate of adoption based on global statistics with significant variances in regions, for example Azure has greater adoption rates in Europe than AWS. Oracle has a much higher adoption rate than Google in GCC and Alibaba beats all other providers when it comes to adoption by enterprises in China.
Other factors that have influenced cloud usage amongst enterprises over the past decade are:
- The need for hybrid workers: The pandemic has accelerated the shift to remote work and hybrid work models, which require cloud-based solutions to enable collaboration, communication and productivity across distributed teams.
- The demand for cloud sustainability or ‘cloud washing’: As environmental concerns become more prominent, enterprises are looking for ways to reduce their carbon footprint and energy consumption. Cloud providers are investing in renewable energy sources, carbon offset programs and green data centers to meet this demand. Leveraging these services can reduce your organization’s carbon footprint without you having to do the heavy lift or investment yourself; you simply reap the benefit of all the hard miles the hyper-scalers have invested already.
- The adoption of AI: AI is one of the most disruptive technologies that can transform various industries and domains. Cloud providers offer various tools and services to enable AI development and deployment, such as machine learning platforms, natural language processing, computer vision, speech recognition and generative AI.
- The emergence of sovereign clouds: Sovereign clouds are cloud services that are operated within a specific country or region, complying with local laws and regulations. Enterprises that operate in highly regulated sectors or regions may prefer sovereign clouds to ensure data sovereignty, privacy and security.
- The maturity of XaaS: XaaS stands for anything-as-a-service, which encompasses various cloud-based offerings such as software-as-a-service (SaaS), platform-as-a-service (PaaS), infrastructure-as-a-service (IaaS), function-as-a-service (FaaS) and more. XaaS enables enterprises to access various resources and capabilities on demand, without having to invest in or manage them.
- The rise of FinOps: FinOps is a set of practices that aim to optimize the financial management of cloud resources. FinOps involves collaboration between IT, finance and business teams to align cloud spending with business goals, monitor and control cloud costs, and leverage cloud pricing models and discounts.
Every organisation’s journey to cloud will be different; rate of uptake, speed to transformation and realization of benefits, even total cost of ownership can be heavily dependent on the migration strategy undertaken. Migration strategy refers to the approach and plan that enterprises adopt to move their workloads and applications from on-premises or legacy environments to the cloud. Migration strategy can vary depending on the complexity, scale and objectives of the migration project. Some of the common migration strategies are:
- Lift-and-shift: This is the simplest and fastest migration strategy, which involves moving an application or workload to the cloud without making any changes to its architecture or code. This strategy can reduce the migration cost and risk, but it may not leverage the full potential of the cloud or address the performance or compatibility issues that may arise in the cloud environment.
- Replatform: This is a moderate migration strategy, which involves making some minor changes to an application or workload to optimize it for the cloud, such as changing the database engine or the operating system. This strategy can improve the performance, scalability and reliability of the application or workload in the cloud, but it may require some additional effort and testing.
- Refactor: This is a complex and time-consuming migration strategy, which involves redesigning and rewriting an application or workload to take advantage of the cloud-native features and services, such as microservices, containers, serverless functions and managed services. This strategy can maximize the benefits of the cloud, such as agility, innovation and cost-efficiency, but it may involve significant investment, risk and disruption.
- Repurchase: This is a migration strategy that involves replacing an existing application or workload with a SaaS solution that offers similar or better functionality. This strategy can eliminate the need for managing or maintaining the application or workload, but it may require some customization, integration and data migration.
- Retain: This is a migration strategy that involves keeping some applications or workloads on-premises or in legacy environments, either temporarily or permanently. This strategy can be used for applications or workloads that are not suitable for the cloud, such as those that have high security or compliance requirements, low latency needs, or legacy dependencies.
- Retire: This is a migration strategy that involves decommissioning some applications or workloads that are no longer needed or used. This strategy can reduce the complexity and cost of the migration project, as well as free up resources for other purposes.
Native application hosting refers to the process of developing and deploying applications that are designed specifically for a particular cloud platform, using its native features and services. Native applications can leverage the full potential of the cloud, such as scalability, elasticity, availability and performance. However, native applications may also face some challenges, such as vendor lock-in, portability issues, complexity and security risks.
Some of the benefits of native application hosting are:
- Faster time-to-market: Native applications can be developed and deployed faster using the cloud-native tools and services provided by the cloud platform, such as code editors, IDEs, SDKs, APIs and CI/CD pipelines.
- Higher quality: Native applications can be tested and validated more easily using the cloud-native tools and services provided by the cloud platform, such as testing frameworks, monitoring tools, logging tools and feedback mechanisms.
- Lower hosting costs: Native applications can be optimized for cost-efficiency using the cloud-native features and services provided by the cloud platform, such as pay-as-you-go pricing models, auto-scaling capabilities, spot instances and reserved instances.
- Greater innovation: Native applications can be enhanced and updated more frequently using the cloud-native features and services provided by the cloud platform, such as serverless functions, containers, microservices and managed services.
Some of the challenges of native application hosting are:
- Vendor lock-in: Native applications may become dependent on specific features and services provided by a particular cloud platform, which may limit their flexibility and interoperability with other platforms or environments. You will always experience some form of lock-in with cloud; choose where you are willing to accept it and to what level.
- Portability issues: Native applications may face difficulties in migrating or replicating across different regions or zones within a cloud platform, or across different cloud platforms or environments.
- Complexity: Native applications may involve multiple components and layers that interact with each other through various protocols and interfaces, which may increase the complexity and risk of errors or failures.
- Security risks: Native applications may expose more attack surfaces and vulnerabilities due to their distributed nature and reliance on external services. They may also require more security measures and controls to protect them from unauthorized access or data breaches.
Security
Security is one of the most critical aspects of public cloud services. Cloud security involves protecting data, applications and infrastructure from various threats and risks in the cloud environment. Cloud security requires shared responsibility between the cloud provider and the customer. The cloud provider is responsible for securing the physical infrastructure and network of the cloud platform (security of the cloud), while the customer is responsible for securing their data and applications hosted on the cloud platform (security in the cloud).
In order to simplify cloud security, look for fully integrated capabilities within a platform rather than a mishmash of individual point solutions. Multiple teams working from the same platform and “one source of truth” is far more efficient and effective than having multiple siloed environments for users to log into each of which contains it own risks, vulnerability information and data. Collaboration, control and visibility are the key to effective enterprise risk management in the cloud and you just don’t get that without a fully integrated platform approach.
Some of the best practices for ensuring security in the public cloud are:
- Encrypt data at rest and in transit.
- Ensure you have full visibility across all your cloud assets. If you can’t see it, you can’t check its configuration or fix it.
- Automate your deployments to avoid manual configuration errors.
- Re-use code wherever possible – get it right and then use it again and again.
- Minimize permissions applied to administrative and service accounts; give just enough rights to an account for it to do its job.
- Enforce multi-factor authentication for ALL privileged accounts, regularly review permissions assigned and have a robust process for turning accounts off when you are no longer using them or when someone leaves the organisation.
- Rotate security keys on a regular basis.
- Baseline your environment and actively look for suspicious activity/behaviours.
- Never, never, ever use any/any rulesets.
- Always limit access to your environment from geographies you don’t do business in or that are well-known cyber attack locations.
- Have a well planned and well practiced breach procedure, clearly establish which team is responsible for what elements, policies and technologies and war-game multiple breach scenarios on a regular basis.
- Define the level of risk which is acceptable to the organisation and educate the board about the risks they are accepting.
- Calculate the cost to the organisation of different breach scenarios and invest in tooling to mitigate the risks with the highest potential cost to the company and its reputation.
- If you are not using something turn it off. Not only will that save you money but it will also reduce your attack surface.
- Develop robust risk and FinOps assessment processes. They are linked to each other and having both a risk and financial view within the same team will pay dividends.
- When selecting tooling, don’t just rely on products that detect issues; look for tooling that can pro-actively protect your environment, as detecting that you have been breached is nowhere near as effective as preventing the breach in the first place.
- Don’t just rely on a vendor’s native toolsets as being “GoodEnough” – No cloud vendor is also a security vendor. No matter what they tell you, their tools are often lagging behind the market in critical features and capabilities, require lots of set up and maintenance and do not work well if at all in multi-cloud architectures. Ask yourself how many public cloud vendors top the Gartner MQ’s for security tooling? Absolutely none!
- When selecting cloud security tooling, assess the tooling against business use cases, establish what use cases are important to your company in given scenarios, then review capabilities. Don’t just select a toolset based on how pretty the interface is or engage in a tick box exercise of functional specifications; test drive it, ensure the capabilities you need today are there and think about what you may need tomorrow before you make a purchasing decision.
- When it comes to cloud security “good enough” is not really “good enough” you want the “best” because your data, your customers data and even your organisation’s reputation will depend on it
For more cloud security insights from CyberTalk.org, please click here. Lastly, to receive more timely cyber security news, insights and cutting-edge analyses, please sign up for the cybertalk.org newsletter.
Original Post URL: https://www.cybertalk.org/2023/07/11/top-public-cloud-insights-to-help-you-manage-risk-more-effectively/
Category & Tags: TRENDING NOW – TRENDING NOW
Views: 0



















































