Source: heimdalsecurity.com – Author: Livia Gyongyoși
Managed security services like Arctic Wolf and its competitors help companies boost cybersecurity without the hassle of an in-house IT team. It’s a practical way to stay secure while focusing on your core business.
Arctic Wolf is popular, but many other MDR providers offer excellent features and services. Here are nine top Arctic Wolf alternatives to explore.
Key takeaways
- Heimdal MXDR – Comprehensive, Fast-Patching Security Platform
- CrowdStrike Falcon – End-to-End Remediation with Expert Threat Intelligence
- Sophos – Real-Time Ransomware Rollback and Endpoint Isolation
- Darktrace – AI-Driven Threat Detection and Anomaly Identification
- Rapid7 Managed Threat Complete (MTC) – Extensive Third-Party Integrations
- Red Canary – High-Fidelity Threat Detection with Automated Responses
- SentinelOne Singularity™ – AI-Powered Endpoint Protection with Financial Assurance
- BitDefender MDR – Global Threat Intelligence with Behavioral Analytics
- Huntress – Proactive Ransomware Detection with Persistent Foothold Identification
1. Heimdal MXDR
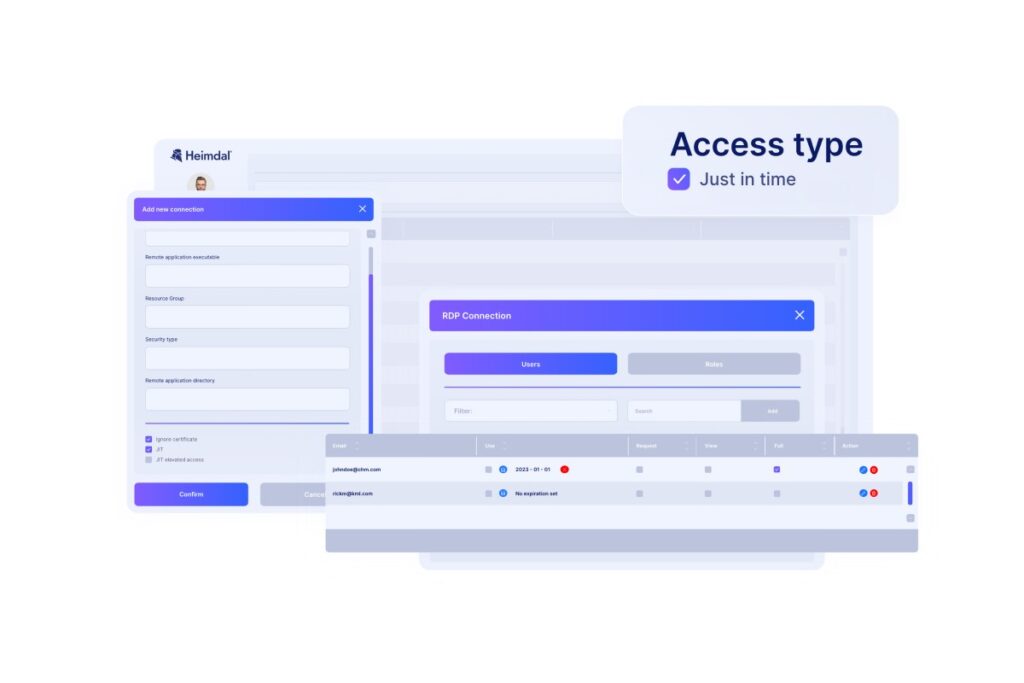
Heimdal’s Managed Extended Detection and Response (MXDR) solution provides 24/7 monitoring through its Security Operations Center (SOC). The team handles event monitoring, threat investigations, extended threat hunting, and forensics. Heimdal’s XDR Unified Security Platform powers its outstanding services.
What makes Heimdal the best alternative to Arctic Wolf?
Here’s what Hemdal brings to your table in a much better way than Arctic Wolf:
Patch & asset management
Heimdal delivers patches for 350+ apps across Windows, macOS, and Linux. It also encrypts patches while in transit, for increased safety. This automated patch management software offers the industry’s shortest vendor-to-end-user waiting time. It can deliver, test, and deploy patches in less than 4 hours.
DNS filtering
This DNS filtering engine uses machine learning to detect both known and unknown malicious domains. Thus, it blocks any potentially harmful communication to and from your network.
Privileged access management (PAM)
Best PAM solutions, like Heimdal’s, enforce the principles of least privilege and just-in-time access. This helps reduce several risks:
- privilege abuse
- internal threat
- privilege creep
Ransomware encryption protection (REP)
REP tools scan to detect potentially malicious encryption attempts. When they find a malicious process, they block it on the spot and isolate the infected device. What makes Heimdal’s REP solution better than others is that it detects ransomware regardless of signature.
What our customers say
It’s not just the feature rich software, it’s the fact that this company stands right behind their product with nothing short of excellent support. They know it’s important to get to clients promptly and they know they need to have actionable knowledge. They excel at both.
Mark F., Director, Computer & Network Security
We bought the product to get a “setup and forget” product to easily patch known 3rd party software on our company pc’s. Today we have ended up using it for elevating rights when needed to manually install software and also DNS filtering to prevent users from reaching bad sites and services when not connected to our sites. We are happy with the product.
Heimdal’s main features & capabilities
Monitoring
Continuous monitoring helps you get a clear, real-time view of all processes in your network:
- communication attempts
- privileged sessions requests
- login attempts, etc.
Being able to see all these events in real time, on the same dashboard, enables you to stop threats quickly.
Investigation
Forensic analysis, process tracking, and intelligent insights help find and understand potential risks.
Threat hunting
Security teams need in-depth data to act fast:
- pre-analyzed risk scores
- indicators of attack (IoAs)
- indicators of compromise (IoCs)
- login reports
Heimdal’s MXDR brings all that intelligence on the same screen, making communication between various tools seamless.
Remediation and response
In case of an attack, time is of the essence. Automated incident response can make the difference between a minor event and a system infection.
Heimdal pricing
Heimdal offers customized Pricing that fits various business requirements and usage patterns. To see Heimdal in action before making any commitments, book a demo.
2. Crowdstrike
CrowdStrike’s Falcon Complete XDR offers threat-hunting, native threat intelligence, and end-to-end remediation across various environments. Thus, it helps identify and mitigate threats before they can cause harm.
Crowdstrike’s main capabilities
- Threat Intelligence: Provides insights into threat actors and their tactics.
- End-to-End Remediation: Ensures threats are fully eradicated and systems are restored to a secure state.
- 24/7 Expert Management: Offers round-the-clock monitoring and response by security experts.
Crowdstrike pricing
CrowdStrike’s pricing details are not public. Here’s a more in detail comparison between Crowdstrike and other vendors.
3. Sophos
Sophos provides real-time, on-device protection that blocks and rolls back ransomware. The solution prevents exploits, limits lateral movement, and automatically isolates compromised endpoints.
In certain deployment scenarios or with extensive security features enabled, Sophos Firewall may require significant hardware resources, which could be a concern for organizations with budget constraints or older hardware.
Sophos’ main capabilities
- Ransomware rollback: Reverts systems to their pre-attack state in case of ransomware incidents.
- Exploit prevention: Blocks the common techniques that attackers use from exploiting vulnerabilities.
- Automatic isolation: Automatically isolates compromised endpoints to prevent threat spread.
Sophos pricing
You’ll need to contact Sophos for details on pricing, at the moment they are not sharing any with the public.
4. Darktrace
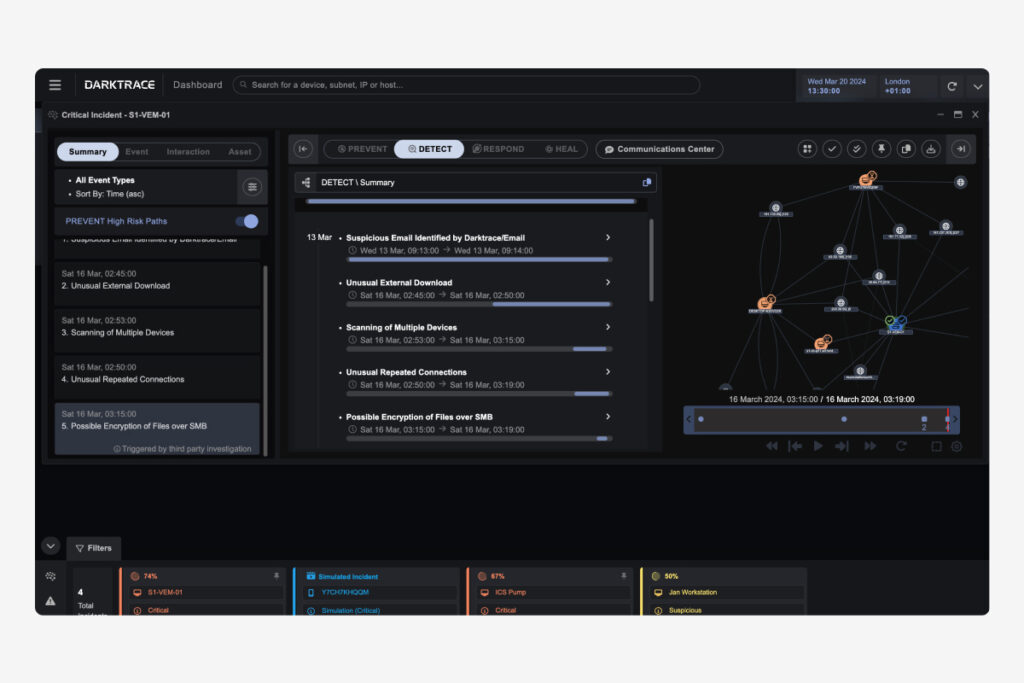
This vendor offers an AI-driven cybersecurity platform that detects, responds to, and investigates threats.
Darktrace main capabilities
- Self-learning AI: Continuously learns each organization’s unique patterns to identify anomalies.
- Real-time threat detection: Monitors digital environments to detect threats as they emerge.
- Comprehensive coverage: Protects across cloud, email, network, and industrial systems.
Darktrace pricing
Pricing details are not public for Darktrace’s MDR platform. If you want specific information about this vendor, contact them directly.
5. Rapid7
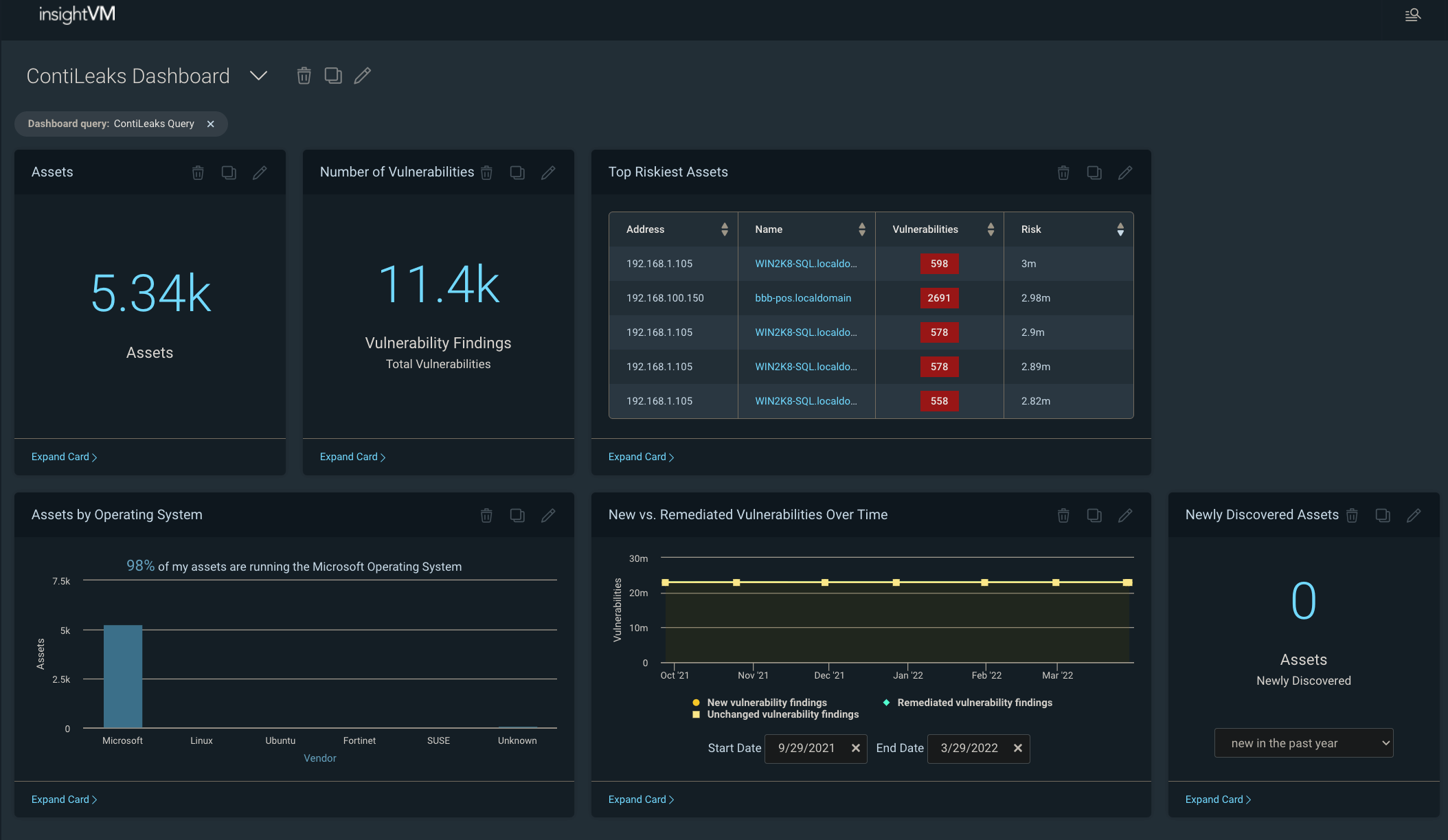
Rapid7’s Managed Threat Complete (MTC) includes coverage for third-party endpoint detection platforms like CrowdStrike Falcon, SentinelOne Singularity Endpoint, and Microsoft Defender for Endpoint.
Single platform for complete risk management, I appreciate the overall interface, and the support team is also very helpful with providing relevant information for the system. Some of the remediation suggestions are not exactly application-oriented and they can defer depending on the application. The software can be a bit cheaper so that small companies can afford it better.
Rapid7 main capabilities
- 24/7 Monitoring: Continuous surveillance of the IT environment to detect and respond to threats.
- Threat Intelligence: Uses up-to-date information on emerging threats to inform defenses.
- Incident Response: Provides guidance and support during security incidents to mitigate impact.
Rapid7 pricing
Rapid7’s pricing information is not public, so I recommend you contact them.
6. Red Canary
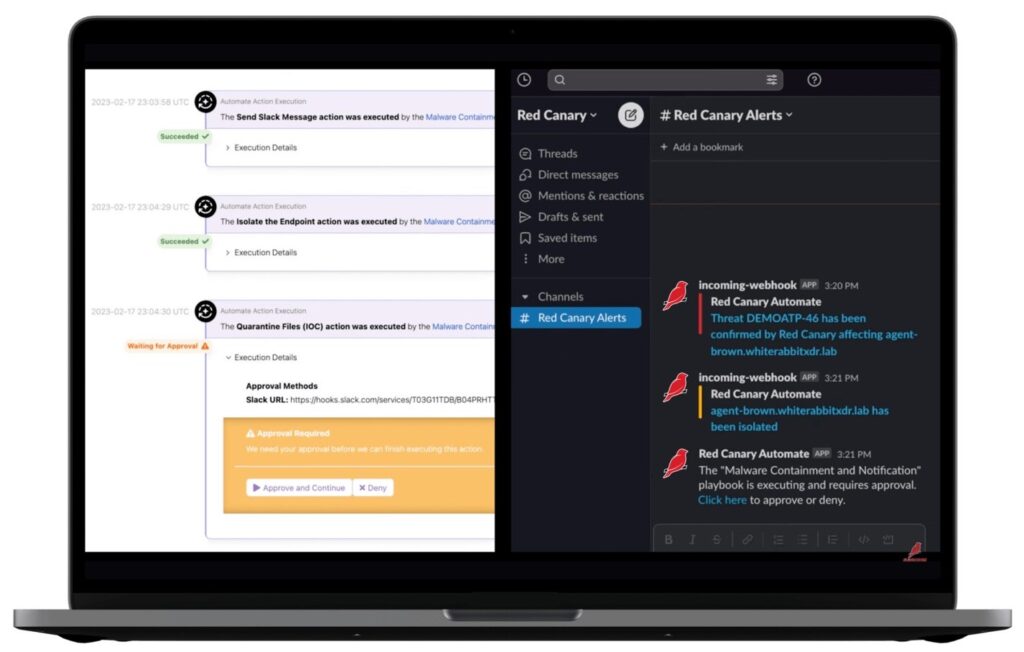
Red Canary also provides MDR services. The tool focuses on delivering high-fidelity threat detection, expert analysis, and automated response. It aims minimizing false positives while also responding timely to threats.
Red Canary main capabilities
- Expert analysis: Security experts analyze potential threats to determine their validity and impact.
- Automated response: Implements automated actions to contain and remediate confirmed threats.
- Comprehensive coverage: Monitors endpoints, identities, cloud workloads, networks, and email systems.
Red Canary pricing
This solution’s pricing is approximately $100 per device per year.
7. SentinelOne
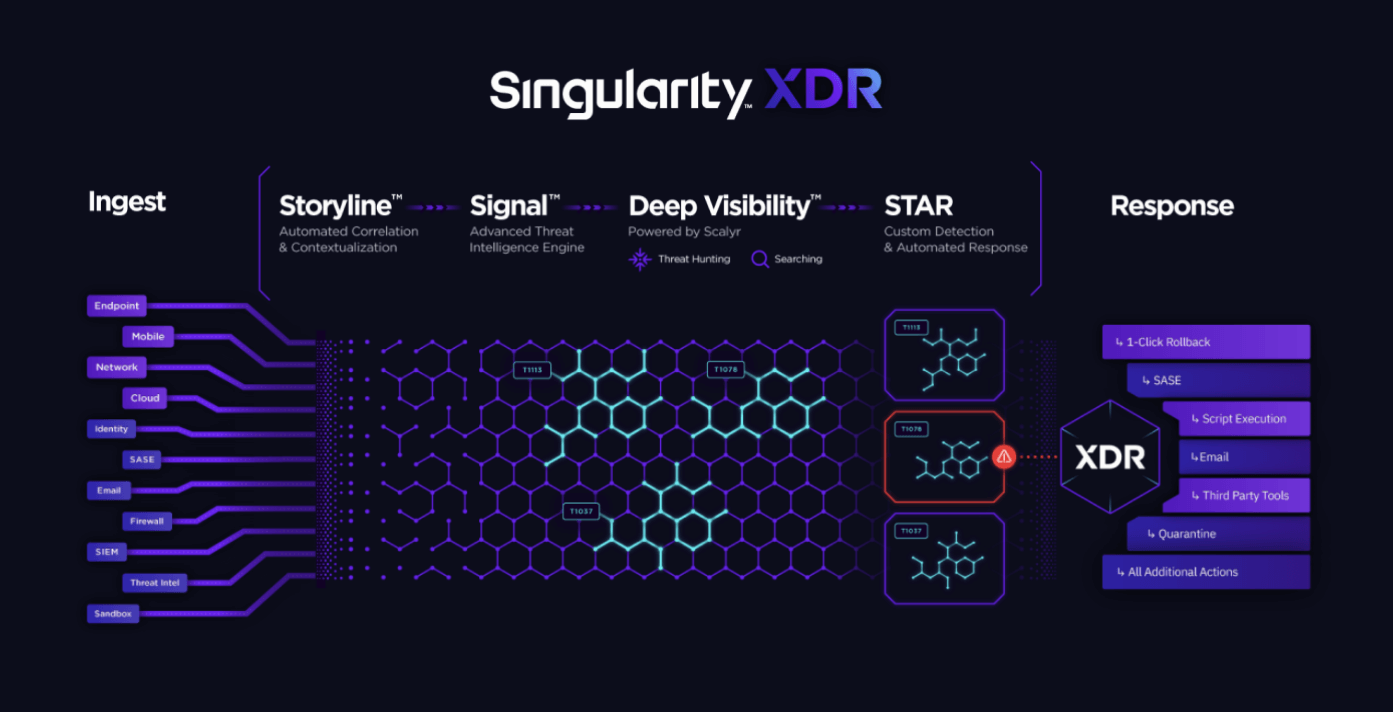
SentinelOne’s Singularity™ utilizes AI and machine learning to analyze endpoint data, detect anomalies, and identify malicious activities.
SentinelOne main capabilities
- Automated remediation: Automatically neutralizes threats to minimize damage.
- 24/7 Monitoring: Provides continuous surveillance by security experts.
- Breach response warranty: in case of a breach caused by a service flaw, SentinelOne offers up to $1 million in coverage for timely financial relief.
SentinelOne pricing
SentinelOne’s pricing details are not public, so get in touch with them for a customized offer.
8. BitDefender
Bitdefender’s Managed Detection and Response (MDR) is another well-known service provider. Its continuous threat monitoring, detection, and response capabilities make it a popular choice.
The platform integrates global threat intelligence to identify and mitigate emerging threats.
BitDefender main capabilities
- Behavioral analytics: Monitors user and entity behaviors to detect anomalies.
- Incident investigation: Conducts thorough analyses of security incidents to find root causes.
- Customized reporting: Offers detailed reports tailored to organizational needs.
BitDefender pricing
Bitdefender’s pricing information is not public, but you can contact them for details.
9. Huntress
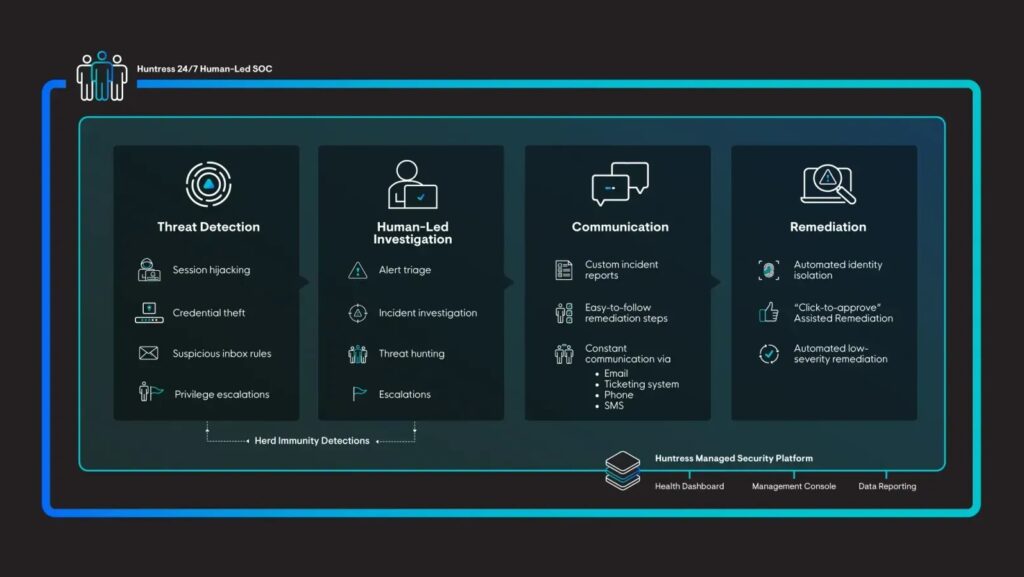
Huntress offers an MDR service that focuses on detecting persistent footholds. It helps stop ransomware attacks that might succeed bypassing traditional security measures.
Huntress Managed EDR has the occasional false positives and I don’t like that they tend to occur when running a software update or making changes. The speed in the support team resolving these issues is great but it regresses our workflow with some unnecessary disruption. It also would benefit from more granular alert setting customization options, which we would like to be able to set notifications to a specific threat level more effectively.
Huntress’ main capabilities
- Ransomware canaries: Deploys decoy files to detect ransomware activity.
- Incident response: Offers guidance and support to remediate identified threats.
- Easy to use dashboard: Provides an intuitive interface for monitoring and managing threats.
Huntress pricing
For specific information, contact Huntress directly.
Why do companies need MXDR services?
MXDR services help companies strengthen their security posture and meet compliance goals. Thus, they can focus on their core business operations and productivity.
Here’s why and how MXDR software benefits your business:
Enhanced threat detection
MXDR providers use advanced tools to stop threats that traditional security measures overlook.
24/7 Monitoring
Continuous surveillance help detect and address threats in time. Imagine an incident happens outside usual working hours, on a Friday evening or on Christmas Eve. You can still be sure someone will be there to see and stop the infection from spreading.
Expertise and resources
Security analysts and other highly skilled IT personnel are hard to find or train. MXDR solutions offer access to trained professionals 24/7.
Cost-effective security
Buying all the advanced tools you need, and hiring professionals to handle them is pricey. Also, building an in-house security operations center will take a while. Outsourcing detection and response services is faster and more cost effective.
FAQs
What is the difference between MDR and MXDR services?
MXDR and MDR are both outsourced cybersecurity solutions. They combine advanced security tools with human expertise. MDR focuses on endpoints only, while MXDR extends across all IT environments.
Can MXDR services integrate with existing security tools?
Yes, some MXDR providers, like Heimdal, run modular platforms. So, they are easy to integrate with an organization’s in-place infrastructure.
Are managed security services suitable for small to medium-sized businesses (SMBs)?
Yes, managed security services can adjust to meet the needs and budgets of SMBs. Modular platforms, like Heimdal’s MXDR, allow paying only for the tools you want.
Livia Gyongyoși is a Communications and PR Officer within Heimdal®, passionate about cybersecurity. Always interested in being up to date with the latest news regarding this domain, Livia’s goal is to keep others informed about best practices and solutions that help avoid cyberattacks.
Original Post URL: https://heimdalsecurity.com/blog/arctic-wolf-competitors/
Category & Tags: Comparisons,XDR – Comparisons,XDR
Views: 0