On 10AUG2022 three Nigerians were extradited from the UK to the US to face charges related to their roles in conducting Business Email Compromise (BEC) attacks against a number of US-based businesses.
43-year old Oludayo Kolawole John Adeagbo, 40-year old Donald Ikenna Echeazu, and 42-year old Olabanji Egbinola were brought to North Carolina to face their charges, although some of their crimes were also charged in Texas and their victims are across the United States and the world.
The three were linked together by exchanging data related to construction companies who were involved in multi-million dollar building projects, and whose emails they were able to acquire through phishing attacks against targets they had purchased from a commercial intelligence service intended to be used by potential sub-contractors.
BEC’s through Look-alike Domains
Victim A notified the FBI that someone was spoofing Victim B, by sending emails from the address “accounts@lucasconstruct.com.” (The real company, Lucas Construction, in League City, Texas, uses the domain “lucasconst.com”.) In one email, a victim received an appropriate form that their company used for updating banking information. The email sender was clearly familiar with their processes, as the email said:
Please find attached our completed ACH form and a copy of a voided check as requested. Kindly let us know once updated.
After processing the change of banking information, Victim A sent the next construction payment of $525,282.39 to a SunTrust bank account rather than to Lucas Construction!
Victim C, a community college in the Houston, Texas area, had a similar experience, resulting in sending $1,995,168.64 to a PNC Bank account controlled by criminals after receiving a similar request to update their records from “accounts@tellepsengroup.com.” The real domain (Victim D) should have been tellepsen.com, a four generation family owned construction and concrete company in Houston.
Victim E, a county government in Texas, sent $888,009.40 to a JPMorgan Chase account after being asked to update the banking records via an email from “accounts@dwcontractorsgroup.com.”
All three of those domains were registered by NameCheap by “Daniel Roberts” who used three different email addresses for the domains. danielroberts604@mail.com, danielroberts605@mail.com, and danielroberts606@mail.com. Additional domains, including TellepsenGroup.com, D1construct.com, and SouthWoodBuilding.com were also created by the criminal — close imitations of the real domains, tellepsen.com, d1construction.com, and southwoodbuilders.com. These domains were used to target additional victims with BEC attempts via bank record “update” requests.
The Texas FBI investigators learned that danielroberts604 was also linked to an investigation being led by FBI Charlotte, North Carolina, where he had used the domain rodgersbuildersinc.com to do a similar scam, as well as another Texas scam using the domain leelewisusa.com to steal funds from a school system in Dallas, Texas.
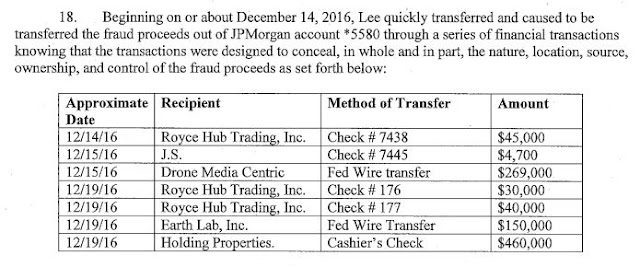
North Carolina was able to add another victim to the case – Appalachian State University, from which ADEAGBO and ECHEAZU were able to steal $1,959,925.02 using a similar methodology. The two recruited a money mule in Los Angeles, California, Ho Shin Lee, who agreed to register a company “Royce Hub Trading” and open a JPMorgan Chase bank account in the same name. Funds stolen by imitating North Carolina based “Rodgers Builders” were stolen after sending emails from “accounts@rodgersbuildersinc.com” to change the banking information. (The real company uses the domain rodgersbuilders.com.)
Construction Market Data
The scammers had subscribed to a service operated by Construction Market Data (CMD), which provided contact information related to “hundreds of thousands” of commercial and civil construction projects.
CMDGroup.com
CMD provided data to the FBI, indicating that the relevant records had been requested by one John Edwards who listed both a US and UK address:
1270 Hasen Hurst Drive, Apt 12, West Hollywood, CA 90046
14 College Gardens, London, GB e47ALG
and who used the email JohnEdwards79@yahoo.co.uk. The associated telephone number +44 797.335.9482 belonged to ADEAGBO. JohnEdwards79 was actually an alias to the email account OludayoAdeagbo@yahoo.co.uk.
Adeagbo was found to possess three passports, a Nigerian and British passport in his true name, listing the birthday 06APR1979, and a second UK passport in the name “John Edwards” b. Nigeria on 06APR1979.
Prior to his involvement in BEC, the BBC reported that ADEAGBO was part of a car-theft ring that used stolen identities to allow them to drive off in Jaguars, Mercedes, BMW’s and Porsches. Calling themselves “the iPod Crew” Adeagbo’s car theft ring stole 70 luxury automobiles worth $1.8 million over a ten month period in 2001. Adeagbo told the BBC in 2004 that he served a 2.5 year prison sentence during which he “found God” and that he was “trading crime for Christianity.”
JohnEdwards and DanielRoberts were both found to have used the same IP addresses to access a variety of online accounts which all provided IP history to the FBI, including Apple, Yahoo, LocalBitcoins.com, and Namecheap. OludayoAdeagbo@yahoo.co.uk also had bank statements in true name for his Santander bank accounts.
The CoinBase account for JohnEdwards79, was actually confirmed to a different person! Donald Echeazu, who used the email diecheazu@yahoo.co.uk and phone 7837887959. Although Coinbase had two photos on file for JohnEdwards which were consistent with Adeagbo, the third photo matched the UK Passport of ECHEAZU.
Homeland Security Investigations (HSI) and Customs and Border Patrol (CBP) learned more when they searched the phone of another co-conspirator as he entered the country. In that phone, he chatted with ADEAGBO’s known UK telephone number, labeled “John Dayo” in his contacts, about bank accounts which he was providing. ADEAGBO instructed him to open up a JPMorgan Chase account in order to receive funds. They discussed a bank transfer where they had expected to received 12 Million (currency unspecified) but were only able to take 8 million.
Photos that were shared in the account, showing ADEAGBO in a Porsche, were found to match a car that he was driving when he was ticketed in London (a black Porsche.)
Another chat in the phone showed a Bank of America account (#32508061285) in the name “Oludayo Kolawole John Adeagdo” using the address 1270 Havenhurst dr Apt 12, West Hollywood, CA 90046.
The Bank of America account had been used to pay $4,510 in several payments in order to receive business information for individuals in North American construction companies from the aforementioned CMD.
Olabanji Egbinola
The final party in the group of extradited scammers, Olabanji Oladotun Egbinola, was tripped up in exactly the same way. Having likely received construction data from the same source (CMD), Olabanji used the email address “accounts@kjellstromleegroup.com” to imitate the real Richmond, Virginia-based company Kjellstrom and Lee. Using the name “Rachel Moore” Olabanji interacted with the University’s Treasury department acting as if a payment was missed and then providing new bank details to fix the problem. As a result they wired the next construction payment of $469,819.49 to the new bank account at the Bank of Hope.
The bogus domain was registered at NameCheap by “bridgetclark” who also registered more than 50 other domains with namecheap, each “deceptively similar to the Internet domain names associated with legitimate construction companies.” Because “bridgetclark” was using a TOR-based cryptocurrency wallet to obscure his true location, the FBI pursued a Rule 41(b)(6)(A) search warrant. Rule 41(b) allows a search warrant to be issued from any US jurisdiction if the location of the target has been obscured using technology and to use technology to seize data from such a targeted computer. In the FBI’s case, this is referred to as a NIT, or a Network Investigative Technique. After receiving the court’s authority, the FBI sent a NIT-laden email message to accounts@kjellstromleegroup.com, which was used to determine the account was being operate from a computer at the IP address 86.191.189.88, a British Telecom IP in the UK. BT was then able to provide UK law enforcement with the subscriber identification of that IP address and it was found that subscriber Samiat Egbinola in Essex shared the residence with OLABANJI OLADOTUN EGBINOLA.
Egbinola had been previously arrested in 2008 for money laundering in the UK and had previously traveled to Los Angeles, California, when he used the email address aegbinola@gmail.com for his point of contact going through customs. A review of the email account, which had been active since 2008, showed that he was in regular communications with the scammers listed above on their yahoo.co.uk addresses.
The post Three UK-based Nigerian BEC Scammers Used Construction Intelligence Service to Target Victims appeared first on Security Boulevard.
Leer másSecurity Boulevard
Views: 3