April 15, 2021Ravie Lakshmanan

Cybercriminals are resorting to search engine poisoning techniques to lure business professionals into seemingly legitimate Google sites that install a Remote Access Trojan (RAT) capable of carrying out a wide range of attacks.
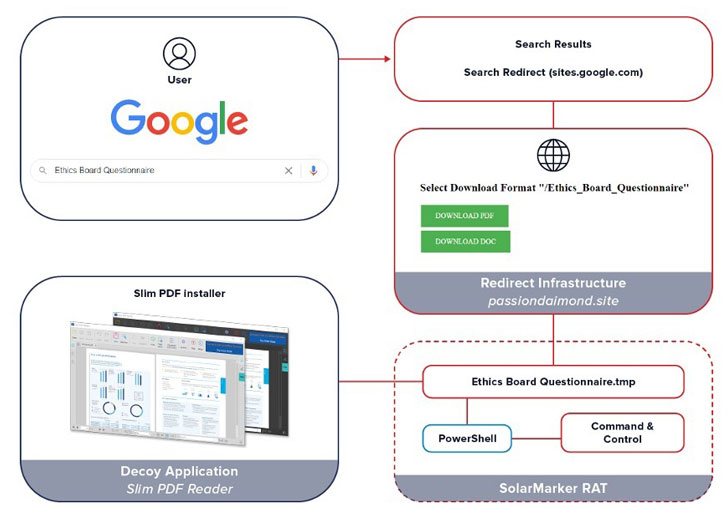
The attack works by leveraging searches for business forms such as invoices, templates, questionnaires, and receipts as a stepping stone toward infiltrating the systems. Users attempting to download the alleged document templates are redirected, without their knowledge, to a malicious website that hosts the malware.
“Once the RAT is on the victim’s computer and activated, the threat actors can send commands and upload additional malware to the infected system, such as ransomware, a credential stealer, a banking trojan, or simply use the RAT as a foothold into the victim’s network,” researchers from eSentire said in a write-up published on Tuesday.
The cybersecurity firm said it discovered over 100,000 unique web pages that contain popular business terms or keywords such as template, invoice, receipt, questionnaire, and resume, thus allowing the pages to be ranked higher on the search results, and therefore, increasing the likelihood of success.
Once a victim lands on the attacker-controlled website and downloads the document being searched for, it becomes an entry point for more sophisticated threats, ultimately resulting in the installation of a .NET-based RAT called SolarMarker (aka Yellow Cockatoo, Jupyter, and Polazert).
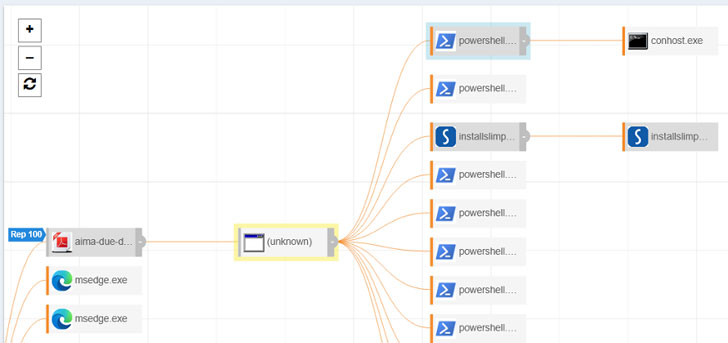
In one case investigated by eSentire, which involved an employee of a financial management company, the malware executable was disguised as a PDF document that, when launched, deployed the RAT along with a legitimate version of Slim PDF as a decoy.
“Another troubling aspect of this campaign is that the SolarMarker group has populated many of their malicious web pages with keywords relating to financial documents,” said Spence Hutchinson, eSentire’s manager of threat intelligence.
“A financial cybercrime group would consider an employee, working in the finance department of a company, or an employee, working for a financial organization, a high value target. Unfortunately, once a RAT is comfortably installed, the potential fraud activities are numerous.”
Views: 0





















































