Source: www.csoonline.com – Author:

Reports of the demise of Windows Active Directory are greatly exaggerated – here’s how Microsoft is supporting AD in its latest server platform.
We’ve often heard that on-premises solutions are on their way out, but until it’s clear that being completely in the cloud makes sense, we will remain in a long transition period. Nowhere else is this made more evident than in the new security features of Windows Server 2025.
While many of these features showcase a “cloud first” viewpoint, there are also clear indications that such technologies are here to stay — a case in point is Microsoft’s Active Directory, which is still supported and is in fact getting some enhancements.
As with many technologies, these features and enhancements kick in after you have ensured that you have raised the forest level and made certain changes in your domain. For example, one of the new changes in Active Directory security surrounds mandatory Lightweight Directory Access Protocol (LDAP) encryption for all connections, protecting sensitive directory data from eavesdropping and tampering.
LDAP has long been used and abused by users and attackers alike. A line of business application will often rely on LDAP for its authentication processes, exposing a means for an attacker to perform injection attacks and other queries.
We’ve often been told to ensure that our network enforces LDAP signing, but that isn’t the same process as encryption or turning on LDAPs, as this encrypts all LDAP attributes including user credentials. Microsoft has been wanting us to turn this setting on since 2007 and Server 2008. Now with Server 2025 they are enabling the setting by default — it can be turned off if you have an older application that won’t support it.
Server 2025 will be supporting TLS 1.3, the latest version of transport layer security, in LDAP over TLS connections. This is not a new technology, but a setting that will now be strongly recommended.
Implementing transport layer security in Server 2025
The implementation of TLS 1.3 when using LDAP over SSL or using the StartTLS command was first supported on platforms starting in June of 2022. Windows updates KB5014668 and KB5014665 specifically add support for this security setting to Windows 11 and Server 2022. If you have these platforms now you can enable this with the following settings:
LDAP server side
Use Registry Editor to modify the following values to disable or re-enable TLS 1.3 LDAP) on the server side:
Registry key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesNTDSParameters
Registry value: LdapDisableTLS1.3
Value type: REG_DWORD
Value data: 0 (Default Enabled) / 1 (Disabled)
Restart the Active Directory Domain Services service for the setting to be effective.
LDAP client side
Use Registry Editor to modify the following values to disable or re-enable TLS 1.3 for LDAP on the client side:
Registry key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLDAP
Registry value: DisableTLS1.3
Value type: REG_DWORD
Value data: 0 (Default Enabled) / 1 (Disabled)
The setting starts taking effect at the next LDAP connection.
Server 2025 will support randomly generated passwords
It’s recommended that you test to ensure that no impact is made to your domain. You may wish to use tools such as IISCrypto in order to back up the current working settings before you make adjustments. If there are systems still sending requests over lower-level security settings, you need to ensure they can support the level of ciphers you have enabled. You will need port 636 open on your domain controller for LDAPS to work.
Next, Server 2025 will support randomly generated passwords for machine accounts, making brute-force attacks more difficult. Machine accounts are identified by the presence of a $ character at the end of the account name. As with all things in Active Directory, even devices and machines need to have an account to join the domain.
Most machine accounts have strong passwords generated automatically and randomly every 30 days. Ensure you review your network and domain for any device that demands a “pre-windows 2000” computer account assignment.
The passwords for these devices are weak and often can be cracked if based on the lowercase name of the machine itself, which was often the case in previous eras. If an attacker steals a machine account, there are often various techniques that can be used to perform reconnaissance on the network ranging from browsing authenticated shares, establishing persistence or initiating attacks on the domain. Always review event 4741 in your event logs to determine if a new unknown machine has joined your domain.
Server 2025 also mandates encrypted connections required for operations involving confidential attributes. This ensures that unauthorized interception and access to data will not occur during transmission.
Make sure to employ Server 2025 patches
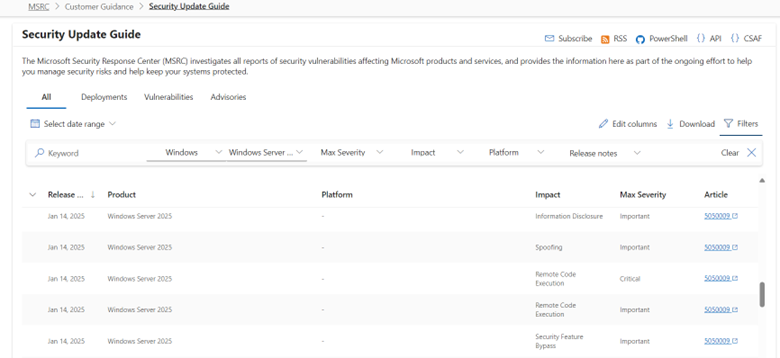
That’s not to say that Windows Server 2025 has been bug-free since release – it has already been patched for six spoofing bugs, 12 security feature vulnerabilities, 71 remote code execution bugs (some critical), 24 information disclosure bugs, 77 elevation of privilege bugs, and 27 denial-of-service bugs since November.
Susan Bradley
Server 2025 includes the ability to perform “hotpatching,” which allows the patching administrator to install updates and not reboot the system. While this is not new, as it was first introduced in Windows Server 2022 Datacenter: Azure edition, it now is also an option through Azure Arc. Azure Arc enables management and allows the Windows Server internal licensing service for Hotpatch to run so that Hotpatch updates are delivered to customers. You can hotpatch Windows Server 2025 physical servers or virtual machines, and those VMs can run on Hyper-V, VMware, or anything else that supports Microsoft’s protection-focused Virtualization Based Security standard.
Getting ready to migrate to Server 2025
Finally In order to migrate to Server 2025 you need to be at the Server 2016 functional level. For Server 2025, if you want a 32K database page size, you need to raise the forest level to Server 2025. In place upgrades are also supported for Server 2025.
Beginning with Windows Server 2025, you can upgrade up to four versions at a time, meaning you can upgrade directly to Windows Server 2025 from Windows Server 2012 R2 and later. Prior to this, you could only upgrade up to two versions at a time.
If you are using the Cluster OS rolling upgrade feature, you are limited to only one version at a time. You are also supported to migrate from an evaluation version to a retail version, or from an older retail version to a newer version, or from a volume-licensed edition to an ordinary retail version.
Review your network and the server operating systems you have under your control. Confer with your hosting partners and with your hardware vendors to ensure that everyone is aligned in their support of your hosting plans. The cloud is not your only option.
SUBSCRIBE TO OUR NEWSLETTER
From our editors straight to your inbox
Get started by entering your email address below.
Original Post url: https://www.csoonline.com/article/3814617/the-cloud-is-not-your-only-option-on-prem-security-still-alive-and-well-in-windows-server-2025.html
Category & Tags: Cloud Security, Data and Information Security, Network Security, Windows Security – Cloud Security, Data and Information Security, Network Security, Windows Security
Views: 4



















































