Source: thehackernews.com - Author: . Feb 02, 2024NewsroomCyber Crime / Malware An INTERPOL-led collaborative operation targeting...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
The Hacker News
Source: thehackernews.com - Author: . Feb 02, 2024NewsroomData Breach / Cloud Security Cloudflare has revealed that...
Source: thehackernews.com - Author: . Feb 01, 2024NewsroomCyber Attack / Botnet The threat actor behind a...
Exposed Docker APIs Under Attack in ‘Commando Cat’ Cryptojacking Campaign – Source:thehackernews.com
Source: thehackernews.com - Author: . Feb 01, 2024NewsroomCryptojacking / Linux Security Exposed Docker API endpoints over...
Source: thehackernews.com - Author: . The U.S. government on Wednesday said it took steps to neutralize...
Source: thehackernews.com - Author: . Feb 01, 2024NewsroomCryptocurrency / Botnet Cybersecurity researchers have detailed an updated...
Source: thehackernews.com - Author: . How's your vulnerability management program doing? Is it effective? A success?...
Source: thehackernews.com - Author: . Feb 01, 2024NewsroomNetwork Security / Malware Google-owned Mandiant said it identified...
Source: thehackernews.com - Author: . Feb 01, 2024NewsroomVulnerability / Software Update The U.S. Cybersecurity and Infrastructure...
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomSoftware Security / Linux Multiple security vulnerabilities have been...
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomVulnerability / Zero Day Ivanti is alerting of two...
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomCyber Crime / Hacking News Cybersecurity researchers are calling...
Italian Businesses Hit by Weaponized USBs Spreading Cryptojacking Malware – Source:thehackernews.com
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomCryptocurrency / Cybersecurity A financially motivated threat actor known...
Source: thehackernews.com - Author: . The SEC isn't giving SaaS a free pass. Applicable public companies,...
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomCyber Attack / Network Security A pair of recently...
Source: thehackernews.com - Author: . Jan 31, 2024NewsroomVulnerability / Endpoint Security Malicious local attackers can obtain...
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomCyber Crime / Malware A Brazilian law enforcement operation...
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomDevSecOps / Vulnerability GitLab once again released fixes to...
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomMalware / Cyber Espionage The China-based threat actor known...
Source: thehackernews.com - Author: . Each New Year introduces a new set of challenges and opportunities...
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomGenerative AI / Data Privacy Italy's data protection authority...
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomMalware / Cyber Threat Threat hunters have identified a...
Juniper Networks Releases Urgent Junos OS Updates for High-Severity Flaws – Source:thehackernews.com
Source: thehackernews.com - Author: . Jan 30, 2024NewsroomVulnerability / Network Security Juniper Networks has released out-of-band...
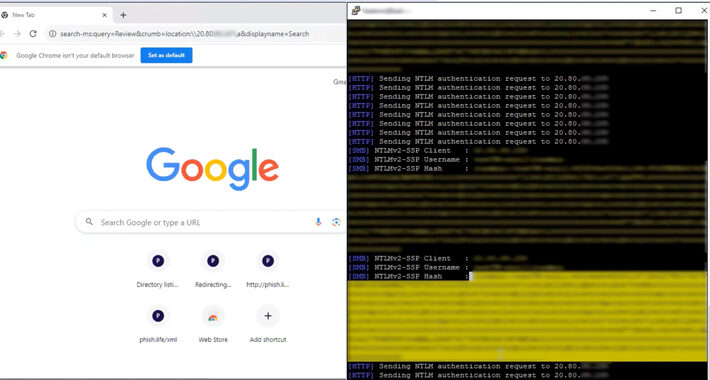
Source: thehackernews.com - Author: . Jan 29, 2024NewsroomVulnerability / NTML Security A now-patched security flaw in...
Source: thehackernews.com - Author: . Jan 29, 2024The Hacker NewsSaaS Security / Webinar In today's digital...
Albabat, Kasseika, Kuiper: New Ransomware Gangs Rise with Rust and Golang – Source:thehackernews.com
Source: thehackernews.com - Author: . Jan 29, 2024NewsroomRansomware / Malware Cybersecurity researchers have detected in the...
Source: thehackernews.com - Author: . Jan 29, 2024NewsroomSurveillance / Data Privacy The U.S. National Security Agency...
Source: thehackernews.com - Author: . Jan 29, 2024NewsroomPyPI Repository / Malware Cybersecurity researchers have identified malicious...
Source: thehackernews.com - Author: . Jan 27, 2024NewsroomMalware / Software Update Mexican financial institutions are under...
Source: thehackernews.com - Author: . Jan 26, 2024NewsroomMalvertising / Phishing-as-a-service Chinese-speaking users have been targeted by...