Source: thehackernews.com - Author: . Feb 06, 2024NewsroomCybersecurity / Vulnerability A recently disclosed server-side request forgery...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
The Hacker News
Source: thehackernews.com - Author: . Feb 06, 2024NewsroomSurveillance / Privacy The U.S. State Department said it's...
Source: thehackernews.com - Author: . Feb 05, 2024NewsroomCryptocurrency / Financial Fraud A 42-year-old Belarusian and Cypriot...
Source: thehackernews.com - Author: . Feb 05, 2024The Hacker NewsData Protection / Threat Intelligence A significant...
Source: thehackernews.com - Author: . Feb 05, 2024NewsroomSpyware / Surveillance The iPhones belonging to nearly three...
Source: thehackernews.com - Author: . Feb 05, 2024NewsroomMalware / Financial Security The threat actors behind the...
Source: thehackernews.com - Author: . The U.S. government on Wednesday said the Chinese state-sponsored hacking group...
Source: thehackernews.com - Author: . Feb 08, 2024The Hacker NewsUnified Identity / Cyber Security If you've...
Source: thehackernews.com - Author: . Feb 08, 2024NewsroomEndpoint Security / Cyber Threat The threat actors behind...
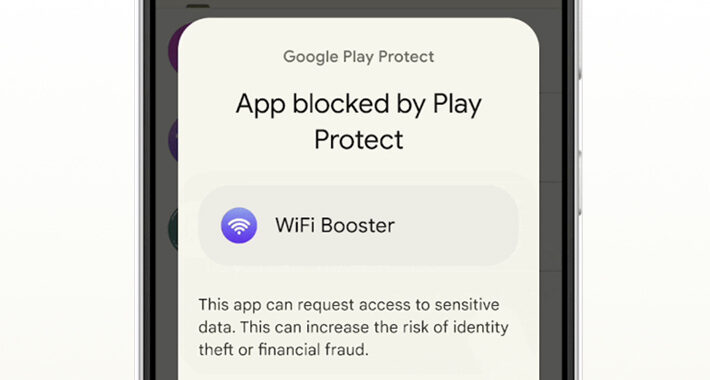
Source: thehackernews.com - Author: . Feb 08, 2024NewsroomData Protection / Mobile Securit Google has unveiled a...
Source: thehackernews.com - Author: . Feb 08, 2024NewsroomCyber Espionage / Malware The North Korea-linked nation-state actor...
Source: thehackernews.com - Author: . Feb 08, 2024NewsroomCyber Threat / Network Security Cisco, Fortinet, and VMware...
Source: thehackernews.com - Author: . The threat actors behind the KV-botnet made "behavioral changes" to the...
Source: thehackernews.com - Author: . Feb 07, 2024NewsroomDevice Security / Vulnerability The maintainers of shim have...
Source: thehackernews.com - Author: . Feb 07, 2024The Hacker NewsRisk Management / Cybersecurity 2024 will be...
Source: thehackernews.com - Author: . A coalition of dozens of countries, including France, the U.K., and...
Chinese Hackers Exploited FortiGate Flaw to Breach Dutch Military Network – Source:thehackernews.com
Source: thehackernews.com - Author: . Feb 07, 2024NewsroomCyber Espionage / Network Security Chinese state-backed hackers broke...
Source: thehackernews.com - Author: . Feb 07, 2024NewsroomCybersecurity / Software Security JetBrains is alerting customers of...
Source: thehackernews.com - Author: . Feb 06, 2024NewsroomVulnerability / Cloud Security Three new security vulnerabilities have...
Source: thehackernews.com - Author: . SaaS applications are the darlings of the software world. They enable...
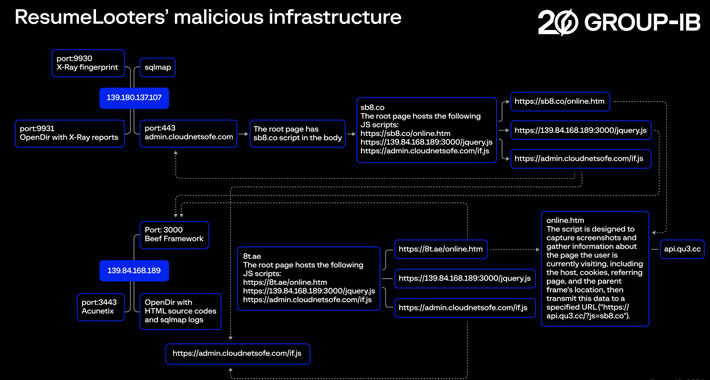
Source: thehackernews.com - Author: . Feb 06, 2024NewsroomDark Web / Cybercrime Employment agencies and retail companies...
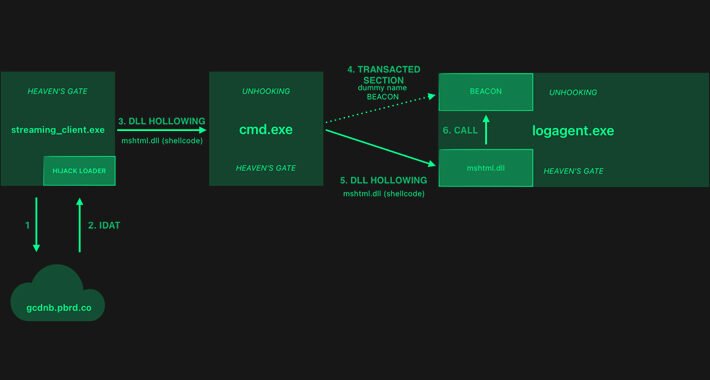
Source: thehackernews.com - Author: . Feb 06, 2024NewsroomSocial Engineering / Malvertising Threat actors are leveraging bogus...
Source: thehackernews.com - Author: . Feb 05, 2024NewsroomCyber Espionage / Cyber Extortion The threat actor known...
Source: thehackernews.com - Author: . Feb 03, 2024NewsroomIntelligence Agency / Cyber Security The U.S. Treasury Department's...
Mastodon Vulnerability Allows Hackers to Hijack Any Decentralized Account – Source:thehackernews.com
Source: thehackernews.com - Author: . Feb 03, 2024NewsroomVulnerability / Social Media The decentralized social network Mastodon...
Source: thehackernews.com - Author: . Feb 03, 2024NewsroomCyber Attack / Software Security Remote desktop software maker...
Source: thehackernews.com - Author: . Russian state-sponsored actors have staged NT LAN Manager (NTLM) v2 hash...
Source: thehackernews.com - Author: . Feb 02, 2024NewsroomCryptojacking / Malware The Computer Emergency Response Team of...
Source: thehackernews.com - Author: . Feb 02, 2024NewsroomNational Security / Data Breach A former software engineer...
Source: thehackernews.com - Author: . Feb 02, 2024The Hacker NewsThreat Intelligence / Cloud Security Cloudzy, a...