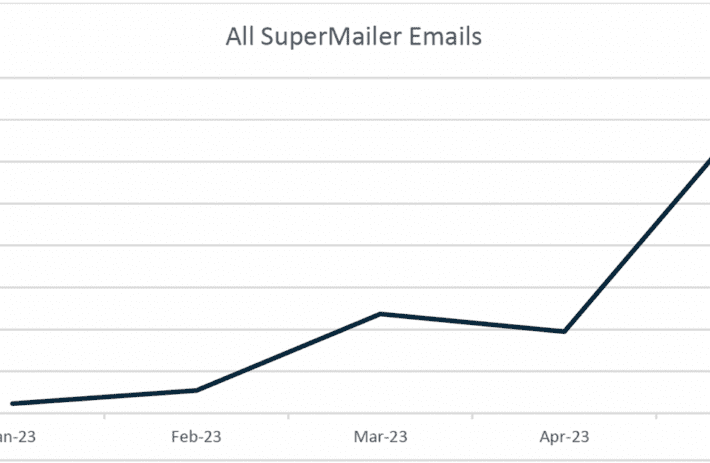
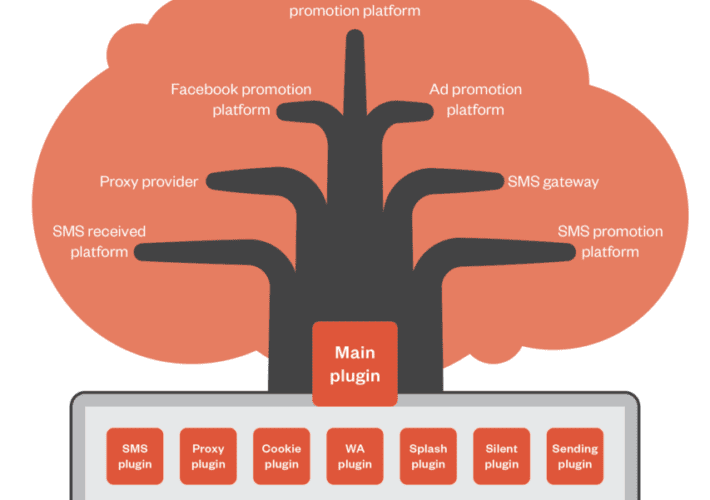
Source: www.securityweek.com - Author: Kevin Townsend A credential phishing campaign using the legitimate SuperMailer newsletter distribution...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire An advanced persistent threat (APT) actor named GoldenJackal has been...
Source: www.securityweek.com - Author: Ionut Arghire Iranian threat actors have been using a newly identified Windows...
Source: www.securityweek.com - Author: Ionut Arghire Google this week introduced Mobile VRP (vulnerability rewards program), a...
Source: www.securityweek.com - Author: Eduard Kovacs German car parts and defense company Rheinmetall has confirmed being...
Source: www.securityweek.com - Author: Marie Hattar The Zero Trust framework has emerged as the leading security...
Source: www.securityweek.com - Author: Ionut Arghire A new US Government Accountability Office (GAO) report shows that...
Source: www.securityweek.com - Author: Ionut Arghire Food distributor Sysco Corporation is informing over 126,000 individuals that...
Source: www.securityweek.com - Author: Eduard Kovacs Satellite TV giant Dish Network has started notifying the individuals...
Source: www.securityweek.com - Author: Ionut Arghire Cybercriminals are using residential IP addresses in business email compromise...
Source: www.securityweek.com - Author: Associated Press The European Union slapped Meta with a record $1.3 billion...
Source: www.securityweek.com - Author: Associated Press Stepping up a feud with Washington over technology and security,...
Source: www.securityweek.com - Author: Eduard Kovacs Samsung smartphone users have been warned by the vendor and...
Source: www.securityweek.com - Author: Ionut Arghire A Wisconsin teenager has been charged with accessing tens of...
Source: www.securityweek.com - Author: Ionut Arghire Security researchers are warning that vulnerabilities patched in the open-source...
Source: www.securityweek.com - Author: Ionut Arghire Cybersecurity firm eSentire says it has identified the second developer...
Source: www.securityweek.com - Author: Ionut Arghire Cloudflare on Thursday announced Secrets Store, a new solution designed...
Source: www.securityweek.com - Author: Eduard Kovacs Apple on Thursday released security updates for its operating systems...
Source: www.securityweek.com - Author: Ryan Naraine Manifest, an early stage startup building technology to help businesses...
Source: www.securityweek.com - Author: Eduard Kovacs Secure remote access is essential for industrial organizations, but many...
Source: www.securityweek.com - Author: Derek Manky So far in 2023, layoffs have resulted in tens of...
Source: www.securityweek.com - Author: Kevin Townsend Quantinuum has demonstrated the controlled creation and manipulation of non-Abelian...
Source: www.securityweek.com - Author: Ionut Arghire Lineaje has launched SBOM360 Hub, a platform for software producers,...
Source: www.securityweek.com - Author: Ionut Arghire Google on Wednesday announced that it’s updating the Android and...
Source: www.securityweek.com - Author: Ionut Arghire A researcher has published a proof-of-concept (PoC) tool that exploits...
Source: www.securityweek.com - Author: Ionut Arghire Cisco this week announced patches for critical-severity vulnerabilities in multiple...
Source: www.securityweek.com - Author: Eduard Kovacs A threat actor has control over millions of smartphones distributed...
Source: www.securityweek.com - Author: Eduard Kovacs Threat actors have been offering access to energy sector organizations,...
Source: www.securityweek.com - Author: Eduard Kovacs The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) announced...
Source: www.securityweek.com - Author: Ionut Arghire Apple this week announced that it blocked 1.7 million applications...