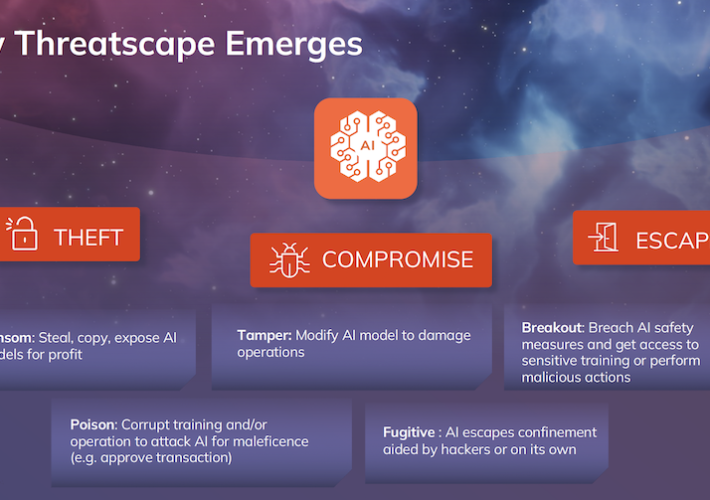
Source: www.securityweek.com - Author: Eduard Kovacs Two vulnerabilities discovered earlier this year in Atos Unify products...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
securityweek.com
Source: www.securityweek.com - Author: Ionut Arghire DevOps platform GitLab this week announced the release of security...
Source: www.securityweek.com - Author: Associated Press A federal judge has halted implementation of a California law...
Source: www.securityweek.com - Author: Eduard Kovacs Secure access service edge (SASE) solutions provider Cato Networks on...
Source: www.securityweek.com - Author: AFP Britain’s interior minister on Wednesday warned tech giant Meta that rolling...
Source: www.securityweek.com - Author: Ryan Naraine Cybersecurity vendor CrowdStrike on Tuesday announced plans to acquire Bionic,...
Source: www.securityweek.com - Author: Ryan Naraine Texas startup HiddenLayer has bagged a hefty $50 million in...
Source: www.securityweek.com - Author: Kevin Townsend Machine identity firm Venafi has launched a proprietary generative AI...
Source: www.securityweek.com - Author: AFP The International Criminal Court said Tuesday it had been affected by...
Source: www.securityweek.com - Author: Eduard Kovacs Cleaning products manufacturer Clorox says the recent cyberattack has been...
Source: www.securityweek.com - Author: Ionut Arghire Data management startup Alcion today announced that it has raised...
Source: www.securityweek.com - Author: Ionut Arghire Pakistan-linked state-sponsored threat actor Transparent Tribe has been observed using...
Source: www.securityweek.com - Author: Ionut Arghire Threat intelligence firm VulnCheck has published details on a new...
Source: www.securityweek.com - Author: Eduard Kovacs Trend Micro on Tuesday released an advisory to warn customers...
Source: www.securityweek.com - Author: Kevin Townsend In this edition of Hacker Conversations, SecurityWeek talks to Casey...
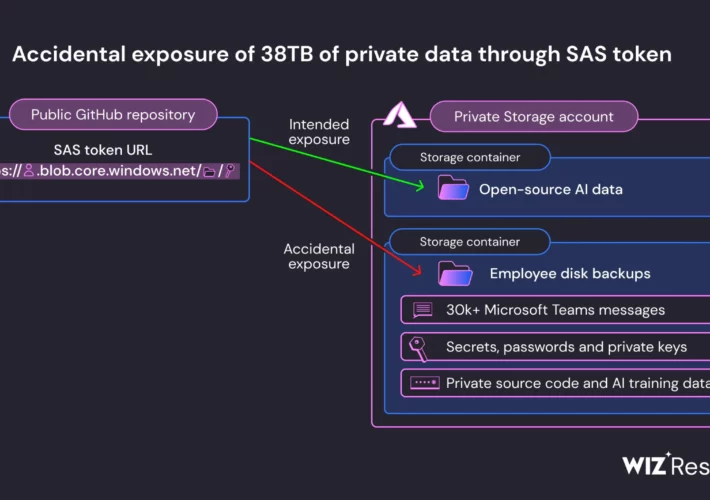
Source: www.securityweek.com - Author: Ryan Naraine Researchers at Wiz have flagged another major security misstep at...
Source: www.securityweek.com - Author: Ionut Arghire Google has announced that it is committed to provide regular...
Source: www.securityweek.com - Author: Kevin Townsend OpenTitan is a project aimed at bringing the success of...
Source: www.securityweek.com - Author: Ionut Arghire The pro-Russian cybercrime group named NoName057(16) has been observed launching...
Source: www.securityweek.com - Author: Ionut Arghire Fortinet has released patches for a high-severity cross-site scripting (XSS)...
Source: www.securityweek.com - Author: Associated Press A persistent error message greeted Dulce Martinez on Monday as...
Source: www.securityweek.com - Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) has released...
Source: www.securityweek.com - Author: Associated Press European regulators slapped TikTok with a $368 million fine on...
Source: www.securityweek.com - Author: Eduard Kovacs Dragos, a company that specializes in protecting industrial control systems...
Source: www.securityweek.com - Author: Associated Press You may not know it, but thousands of often shadowy...
Source: www.securityweek.com - Author: Ryan Naraine Russian hacker Dariy Pankov has pleaded guilty to computer fraud...
Source: www.securityweek.com - Author: Eduard Kovacs The US Department of Defense (DoD) this week published an...
Source: www.securityweek.com - Author: Associated Press Search giant Google agreed to a $93 million settlement with...
Source: www.securityweek.com - Author: Eduard Kovacs SecurityWeek is publishing a weekly cybersecurity roundup that provides a...
Source: www.securityweek.com - Author: Ionut Arghire Identity fraud prevention provider Deduce this week announced that it...