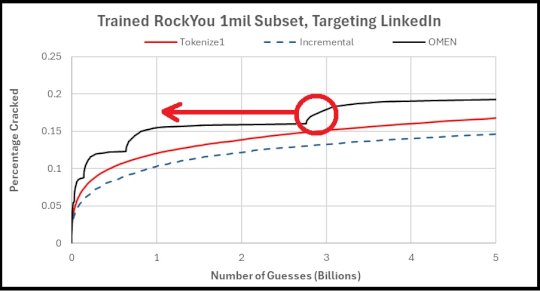
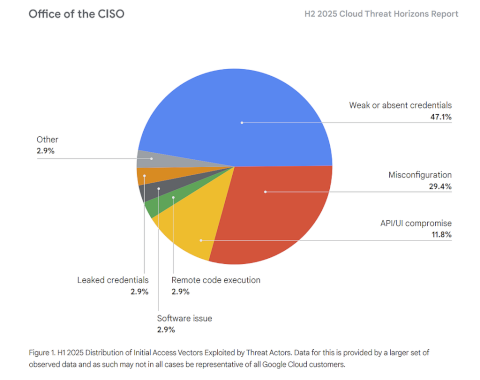
Source: securityboulevard.com - Author: Matt Weir “If I had an hour to solve a problem, I...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: Matthew Rosenquist LinkedIn is a great communication tool for business professionals...
Source: securityboulevard.com - Author: Tom Hollingsworth For IT administrators, two words sure to cause undue stress...
Source: securityboulevard.com - Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe,...
Source: securityboulevard.com - Author: Michael Vizard A survey of 587 CISOs published this week finds security...
Source: securityboulevard.com - Author: Jeffrey Burt In the wake of the high-profile data breaches of the...
Source: securityboulevard.com - Author: Michael Vizard Reveal Security this week unfurled a platform designed to enable...
Source: securityboulevard.com - Author: Michael Vizard A global survey of 2,000 senior security decision-makers in organizations...
Source: securityboulevard.com - Author: Richi Jennings GOOG CRM PII AWOL: ‘ShinyHunters’ group hacked big-G and stole...
Source: securityboulevard.com - Author: Alan Shimel From the floor at #BlackHat2025: Cybersecurity has the blinking lights,...
Source: securityboulevard.com - Author: cybernewswire Austin, TX, Aug. 6, 2025, CyberNewswire: SpyCloud, the leader in identity...
Source: securityboulevard.com - Author: Gary Warner Project Red Hook is a Homeland Security Investigations operation examining...
Source: securityboulevard.com - Author: Michael Vizard Palo Alto Networks this week revealed it is providing early...
Source: securityboulevard.com - Author: Michael Vizard This week at the Black Hat USA 2025 conference, Contrast...
Source: securityboulevard.com - Author: Matthew Rosenquist Microsoft faces ongoing, systemic cybersecurity failures rooted in blind spots...
Source: securityboulevard.com - Author: FireTail - AI and API Security Blog Aug 04, 2025 - Lina...
Source: securityboulevard.com - Author: Erez Hasson Today, organizations increasingly rely on DevOps to accelerate software delivery,...
Source: securityboulevard.com - Author: Teri Robinson Unmanaged machine identities have continued to tick up at a...
Source: securityboulevard.com - Author: Adam Zahorscak Enterprise Kubernetes management is the cornerstone of modern cloud-native operations,...
Source: securityboulevard.com - Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe,...
Source: securityboulevard.com - Author: Anton Chuvakin This is my completely informal, uncertified, unreviewed and otherwise completely...
Source: securityboulevard.com - Author: Jeffrey Burt The security breach of the popular women-only safe-dating app Tea...
Source: securityboulevard.com - Author: Jon Swartz Palo Alto Networks Inc. is in discussions to acquire CyberArk...
Source: securityboulevard.com - Author: George V. Hulme For years, primarily driven by regulatory compliance mandates, such...
Source: securityboulevard.com - Author: Tom Hollingsworth For decades, network security followed a simple model: the castle...
Source: securityboulevard.com - Author: Michael Vizard Intruder this week made available an open-source tool that scans...
Source: securityboulevard.com - Author: Jeffrey Burt Christina Marie Chapman, an Arizona resident, was sentenced to 8.5...
Source: securityboulevard.com - Author: Alan Shimel Clorox is suing IT giant Cognizant, claiming their help desk...
Source: securityboulevard.com - Author: cybernewswire Chennai, India, 25th July 2025, CyberNewsWire The post xonPlus Launches Real-Time...
Source: securityboulevard.com - Author: Jeffrey Burt Clorox is suing Cognizant for $380 million, saying the IT...