Vulnerability management – we’re doing it wrong Security professionals (and the people who measure our performance...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
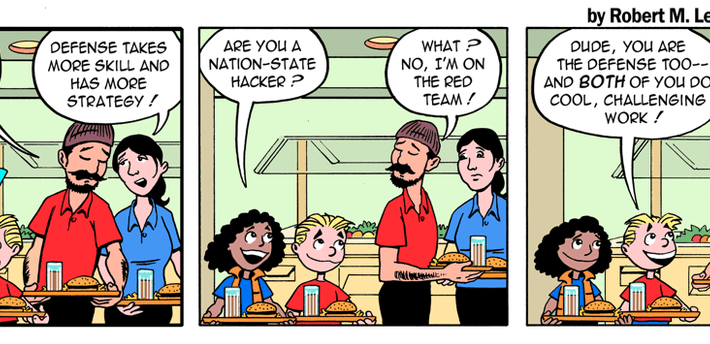
Robert M. Lee’s & Jeff Haas’ Little Bobby Comic – ‘WEEK 235’ (2019 Repost) via the...
BSidesTLV 2022 – Amichai’s And Stav Shulman’s ‘Now You C(&C), Now You Don’t’ Our thanks to...
Email and cybersecurity: Fraudsters are knocking Can you remember your first email? Either sending one, or...
Multi-Factor Authentication Fatigue Attack, Signal Account Twilio Hack, Facebook and Instagram In-App Browser A Cisco employee...
More Password Cracking Tips: A Defcon 2022 Crack Me If You Can Roundup “We do not...
Deepfence Open Source Community Update – August 2022 We’ve seen some tremendous momentum since our last...
Understanding eBPF for API Security Executive Summary API security is increasingly a top priority for security...
BSidesTLV 2022 – Vera Mens’ ‘Total Flaw: Hacking Flow Computers For Fun And Free Gas’ Our...
Black Hat Fireside Chat: Replacing VPNs with ZTNA that leverages WWII battlefield tactics The sunsetting of...
Analysis of Clop’s Attack on South Staffordshire Water – UK On August 15, the Clop ransomware...
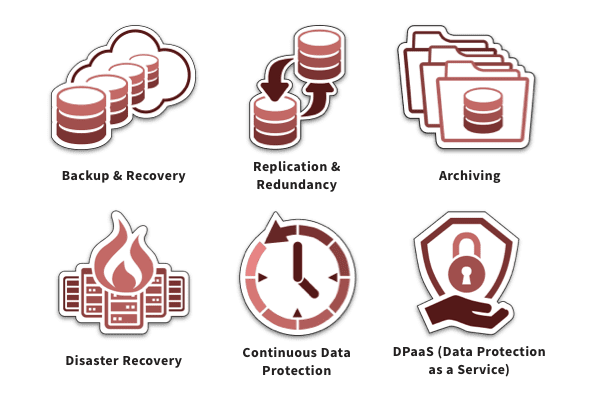
Data Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats “Data really powers everything that...
Friday Squid Blogging: The Language of the Jumbo Flying Squid The jumbo flying squid (Dosidicus gigas)...
July Tesla Sales Crashed in Germany and Norway: Not Even on Chart Looking at July I...
Goodbye “Kill Chains”, Hello “Attack Sequences” A few years ago at the RSA Conference I co-presented...
Aspen Security Forum 2022 – Moderator: Courtney Kube – Niamh King’s Opening Remarks & National Security...
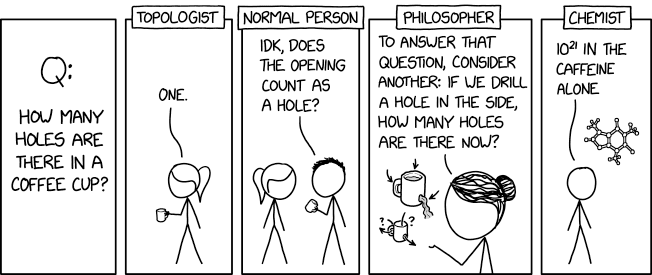
XKCD ‘Coffee Cup Holes’ via the comic artistry and dry wit of Randall Munroe, resident at...
Aspen Security Forum 2022 – Moderator: Dafna Linzer – The 21st Century Nuclear Arms Race Emma...
5 tips for spotting and avoiding Pig butchering scams A new type of scam, called “pig...
The Importance of Faraday Technology with Aaron Zar from SLNT Aaron Zar, SLNT founder and director...
Comparing Twilio and Slack breach responses We recently learned about major security breaches at two tech...
Back to School Means More Cyber Concerns Cyberattacks continue to rise, threatening the educational sector As...
The Power of Provenance: From Reactive to Proactive Cybersecurity While next-gen firewalls (NGFW), extended detection and...
$23 Million YouTube Royalties Scam Scammers were able to convince YouTube that other peoples’ music was...
The Week in Cybersecurity: MFA shortcomings paved the way for Cisco breach MFA’s shortcomings paved the...
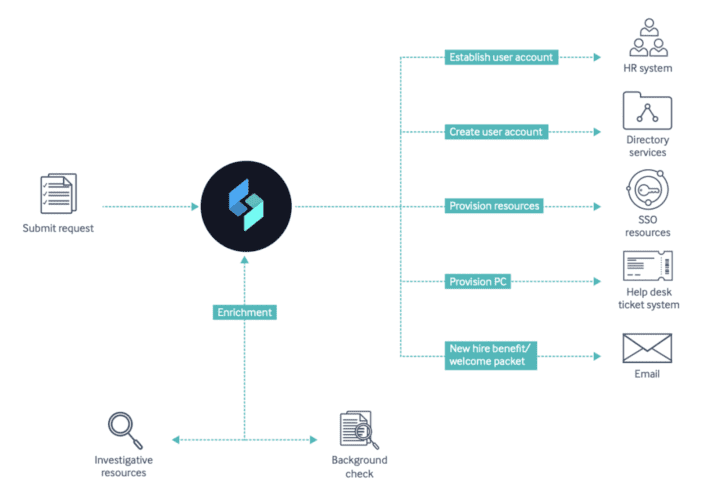
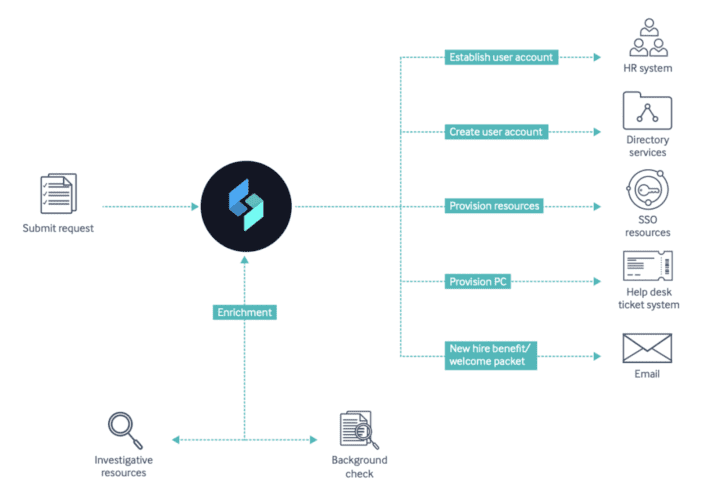
Why You Need to Automate Your Onboarding & Offboarding Process The growing threat landscape has made...
Why You Need to Automate Your Onboarding & Offboarding Process The growing threat landscape has made...
Aspen Security Forum 2022 – Led By Penny Pritzkerl – Virtual Fireside Chat with Secretary Gina...
Aspen Security Forum 2022 – Moderator: Edward Luce – Global Economy: Recovery Or Recession Bound? In...
Black Hat 2022 — End-to-End Fun and API Security It’s a wrap on Black Hat 2022!...