Do Hardened Systems Need FIM? In a recent podcast interview with Hillarie McClure, Multimedia Director of...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
The Top 5 Ways to Secure Your Snowflake Environment The world is increasingly built on data....
VMware vRealize Log Insight VMSA-2023-0001 IOCs Introduction The recent VMware VMSA describes four new CVEs affecting...
USENIX Security ’22 – R. Spencer Hallyburton, Yupei Liu, Yulong Cao, Z. Morley Mao, Miroslav Pajic...
Kevin Mitnick Hacked California Law in 1983 Early in his career, Kevin Mitnick successfully hacked California...
CBA AND FIDO: One, Other, or Both? Overview – A Pragmatic FIDO Approach There are a...
There’s No There There….Or is There? You Won’t Find Out With DLP Over the past weeks,...
Clarification of Obligations for the Use of Online Tracking Technologies by HIPAA Covered Entities and Business...
Threat Hunting: The Cost-Effective Way to Protect Your Organization’s Bottom Line (and Keep the Hackers at...
Cybersecurity is Facing a Cataclysmic Problem At a time when cybersecurity threats are at an all-time...
Public Groups Identify Tesla Terrorist After Unexplained Police Delay A data sharing initiative with news video...
Flexible Metal NASA Robot Tires Now Available for Bicycles A couple of the awards at this...
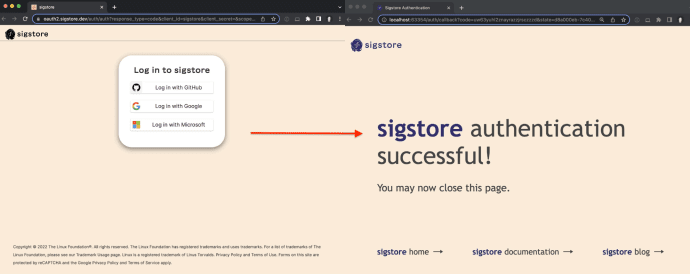
Announcing a stable release of sigstore-python By William Woodruff Read the official announcement on the Sigstore...
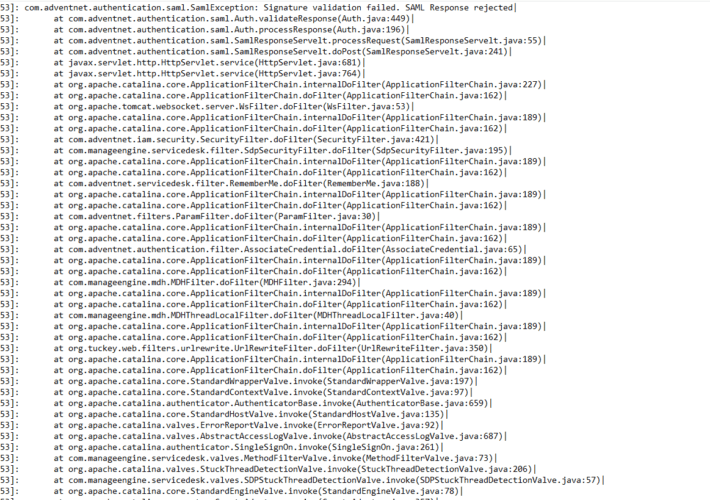
ManageEngine CVE-2022-47966 IOCs Introduction The recent ManageEngine CVE-2022-47966 is a pre-authentication remote code execution vulnerability. Depending on...
USENIX Security ’22 – Theresa Stadler, Bristena Oprisanu, Carmela Troncoso ‘Synthetic Data – Anonymisation Groundhog Day’...
Yikes, Control Web Panel has Critical RCE — Patch NOW Linanto’s popular web hosting control panel,...
Randall Munroe’s XKCD ‘Washing Machine Settings’ via the comic artistry and dry wit of Randall Munroe,...
Control Web Panel Vulnerability, CVE-2022-44877, Actively Exploited in the Wild This post offers details on the...
Sonatype Nexus Lifecycle Boosts Open Source Security and Dependency Management The post Sonatype Nexus Lifecycle...
USENIX Security ’22 – Aloni Cohen, University of Chicago – ‘Attacks on Deidentification’s Defenses’ Distinguished Paper...
Tesla Factories Pollute Schools? A Story Nobody is Talking About From a long list of horrible...
Microsoft January Patch Tuesday 2023: 98 Security Vulnerabilities and a Zero Day On January 10th, 2023...
Multiple Global Car Brands Discovered to Have API Vulnerabilities Connected cars are a way of life...
USENIX Security ’22 – Theresa Stadler, Bristena Oprisanu, Carmela Troncoso – ‘Synthetic Data – Anonymisation Groundhog...
Why You Need Continuous Password Monitoring for True Protection Some free password policy tools out there...
Why These CAPTCHAs Don’t Work Why These CAPTCHAs Just Don’t Work Over the past four years,...
Data Security: Your Ultimate Duty to Your Online Customer Retail business leaders deal with many risks...
ReversingLabs Threat Analysis and Hunting Solution January 2023 Update: Driving SecOps Forward Learn how your organization...
Best Practices in Dependency Management: Cooking a Meal of Gourmet Code The post Best Practices...
Tesla “Solar Factory” Implicated in FSD Fraud: Workers Directed to Classify Images for Driving Elon Musk...