Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: Mimi Pham After tons of hard work, your company has successfully completed...
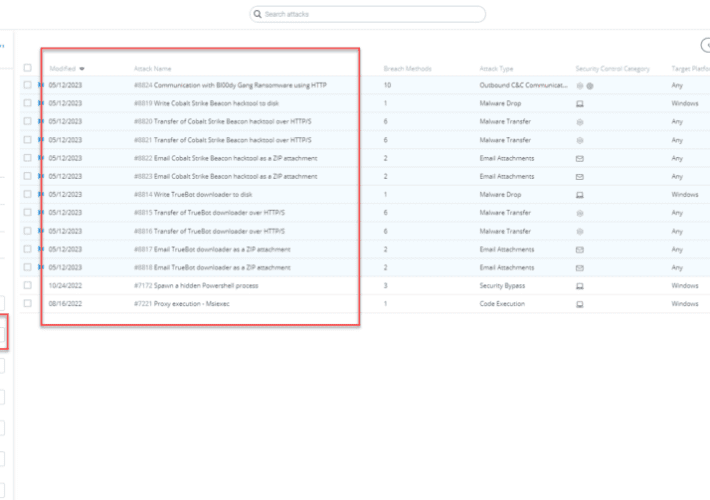
Source: securityboulevard.com - Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On May 11th,...
Source: securityboulevard.com - Author: David Lindner, Director, Application Security Insight #1 “Privacy is becoming a problem...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Bob Zhang Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Grip Security Blog See and Secure the SaaS-Identity Attack Surface When a...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community...
Source: securityboulevard.com - Author: Santiago Vicente Key Points CryptNet is a new ransomware-as-a-service that has been...
Source: securityboulevard.com - Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX...
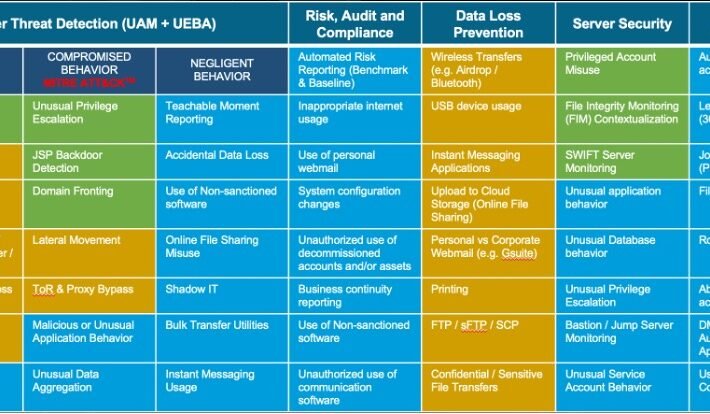
Source: securityboulevard.com - Author: Brian Stoner Insider risk is the fastest growing area of cybersecurity today....
Source: securityboulevard.com - Author: Bruce Schneier Ted Chiang has an excellent essay in the New Yorker:...
Source: securityboulevard.com - Author: Guest Expert Sponsorships Available Keshav Malik Keshav is a full-time Security Engineer...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Michael Vizard Okta this week made available Security Center, an extension of...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Jenn Jeffers In today’s world, fraud and cybercrime are rampant. With the...
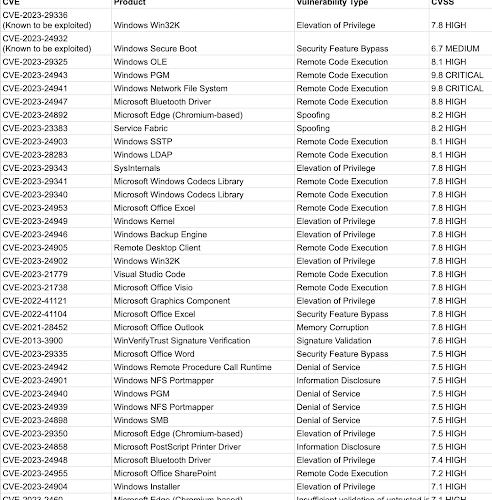
Source: securityboulevard.com - Author: Team Nuspire Microsoft released its May Patch Tuesday update this week, with...
Source: securityboulevard.com - Author: Votiro Cybercriminals do it for the money. Okay, maybe not all of...
Source: securityboulevard.com - Author: Kyle Morris, Senior Compliance Success Manager, Scytale It’s hard to ace the...
Source: securityboulevard.com - Author: Tom Dixon Day In the Life: SOC Analyst By Tom Dixon, Security...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Natalie Anderson Cybersecurity compliance represents a major business opportunity for managed service providers...
Source: securityboulevard.com - Author: RiskLens Staff RiskLens successfully completed a SOC 2 Type 2 audit and...
Source: securityboulevard.com - Author: Flashpoint Intel Team Yesterday was the monthly (in)famous Patch Tuesday, where many...
Source: securityboulevard.com - Author: Ofri Ouzan On May 9th 2023, Microsoft released their May Patch Tuesday...
Source: securityboulevard.com - Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach The Cybersecurity and...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Satya Moutairou POV: an important prospect requires all of their partners to...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community...