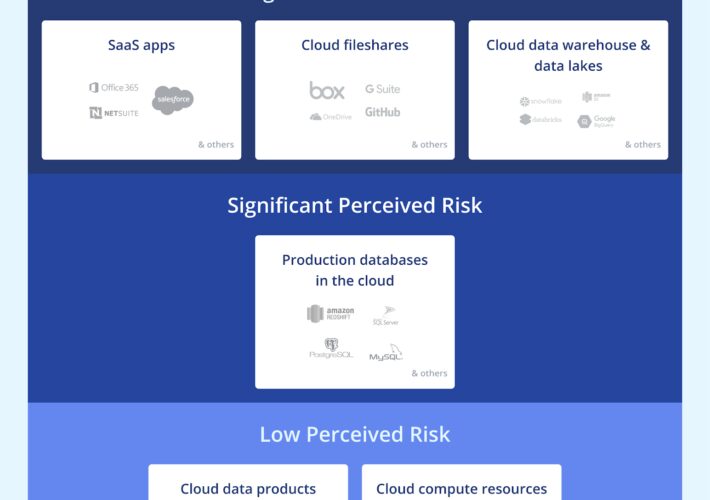
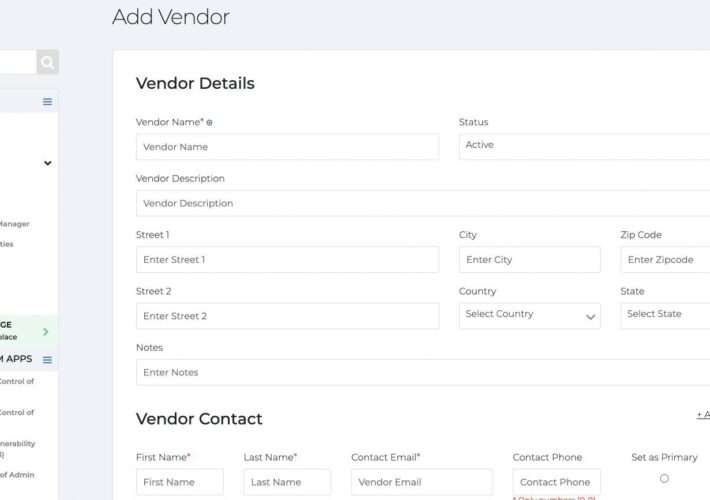
Source: securityboulevard.com - Author: Erin Crapser Today’s edition of GRC Newsflash features our Compliance Specialist Frank...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
Source: securityboulevard.com - Author: Yuzuka Akasaka The threat landscape has never been more challenging for CISOs...
Source: securityboulevard.com - Author: Yuzuka Akasaka The nebulous part of the internet: the dark web, which...
Source: securityboulevard.com - Author: Mal Fitzgerald Contextual Awareness in Network Detections By Mal Fitzgerald, Sales Engineer...
Source: securityboulevard.com - Author: Vikas Shetty In an era marked by unprecedented advancements in artificial intelligence...
Source: securityboulevard.com - Author: Sarit Yerushalmi GraphQL is a powerful query language for APIs that has...
Source: securityboulevard.com - Author: Jeffrey Burt Phishing continues to be a bane of organizations. Phishing accounts...
Source: securityboulevard.com - Author: Dylan Broxson A few days ago our team met with security leaders...
Source: securityboulevard.com - Author: Natalie Anderson Monthly Release Notes for August Looking to learn about Apptega’s...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Jeffrey Burt Millions of people who use the Freecycle online forum to...
Source: securityboulevard.com - Author: SecureIQLab In the rapidly evolving digital landscape, organizations are confronted with the...
Source: securityboulevard.com - Author: Votiro Team Cybercrime, once chiefly associated with shadowy individuals seeking personal gains,...
Source: securityboulevard.com - Author: Michael Vizard Noname Security has added full support for reducing the top...
Source: securityboulevard.com - Author: Deepak Gupta - Tech Entrepreneur, Cybersecurity Author The U.N. Declaration of Human...
Source: securityboulevard.com - Author: Merton Notrem, Compliance Success Manager, Scytale Are you ready to hit pro-level...
Source: securityboulevard.com - Author: Nik Hewitt More than just IP addresses or VLANs, identity segmentation is...
Source: securityboulevard.com - Author: Marc Handelman Monday, September 4, 2023 Security Boulevard The Home of the...
Source: securityboulevard.com - Author: Marc Handelman Monday, September 4, 2023 Security Boulevard The Home of the...
Source: securityboulevard.com - Author: Michelle Ofir Geveye Cyber insurance offers financial protection and support in the...
Source: securityboulevard.com - Author: Tom Eston In this episode Luke Jennings VP of Research & Development...
Source: securityboulevard.com - Author: Lohrmann on Cybersecurity Reports from cybersecurity companies in 2023 show mixed trends...
Source: securityboulevard.com - Author: Marc Handelman Sunday, September 3, 2023 Security Boulevard The Home of the...
Source: securityboulevard.com - Author: Avoid The Hack! This post was originally published on 27 APR 2021;...
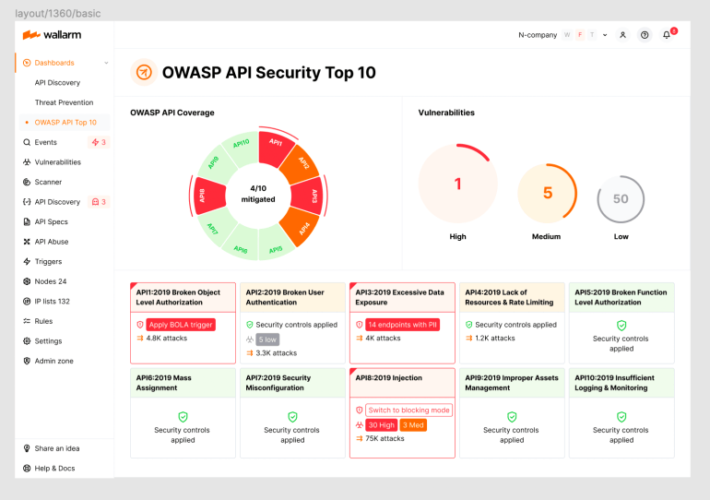
Source: securityboulevard.com - Author: wlrmblog Welcome to the 7th post in our weekly series on the...
Source: securityboulevard.com - Author: Amy Luby MSP v MSSP – is there a distinction anymore? Well,...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Keon Ramzani In response to the growing concerns surrounding AI-driven threats, Constella...
Source: securityboulevard.com - Author: Digital Defense by HelpSystems San Antonio, TX – August 1, 2023 –...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...