Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
- Home
- About Us
- Contact Us
- Register to apply for a free CISO2CISO Membership
- CISO2CISO Network
- CISO2CISO Services
- Sitemap
- Submit News
Security Boulevard
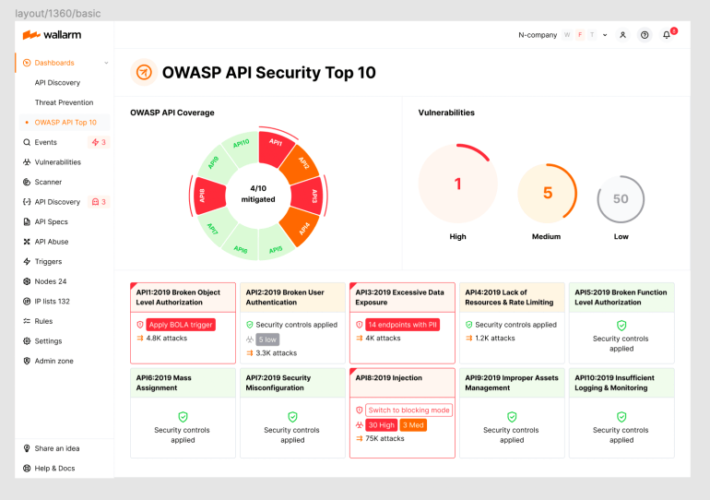
Source: securityboulevard.com - Author: wlrmblog Welcome to the 8th post in our weekly series on the...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
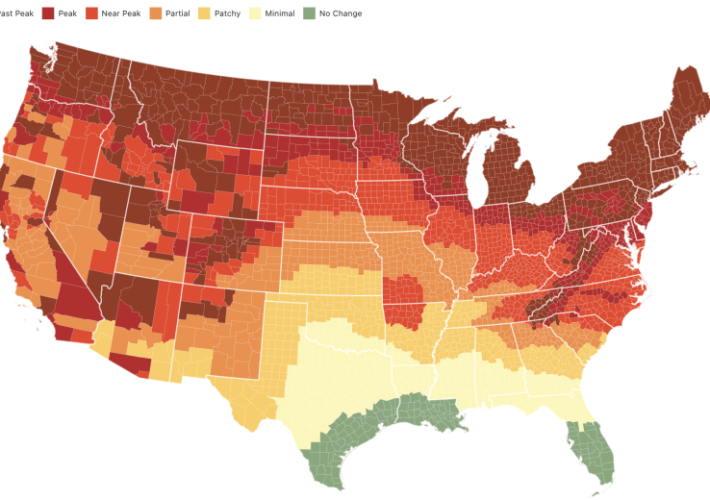
Source: securityboulevard.com - Author: hrbrmstr The days are getting shorter and when we were visiting Down...
Source: securityboulevard.com - Author: Heidi King The modern digital landscape is expanding and transforming at breakneck...
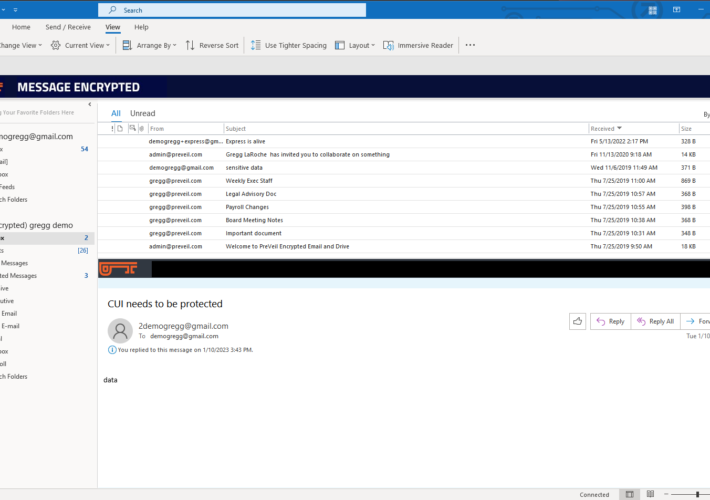
Source: securityboulevard.com - Author: Gregg LaRoche We’re excited to announce 5 new features coming to PreVeil:...
Source: securityboulevard.com - Author: HYPR Team The recent, numerous high-profile attacks targeting identity processes, like those...
Source: securityboulevard.com - Author: Hyperproof Team ISO/IEC 27001 is an information security standard designed and regulated...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
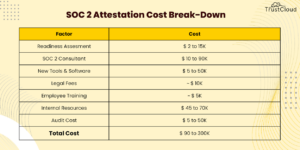
Source: securityboulevard.com - Author: Satya Moutairou How much does it cost to get SOC 2? A...
Source: securityboulevard.com - Author: Kaustubh Jagtap Author: Kaustubh Jagtap, Product Marketing Director, SafeBreach On September 7,...
Source: securityboulevard.com - Author: Richi Jennings “Privacy Sandbox” criticized as a proprietary, hypocritical, anti-competitive, self-serving contradiction.Google...
Source: securityboulevard.com - Author: David Lindner, Director, Application Security Insight #1 Prompt injection is becoming a...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
BSides Buffalo 2023 – Zack Glick – How to Read a Breach Notification – Source: securityboulevard.com
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Jeffrey Burt Cybersecurity firm Emsisoft is telling users to update their anti-virus...
Source: securityboulevard.com - Author: Scott Wright Spoofing attacks often happen through email or online messaging services...
Source: securityboulevard.com - Author: wlrmblog If you’re in the Albuquerque area this Friday and/or Saturday, we...
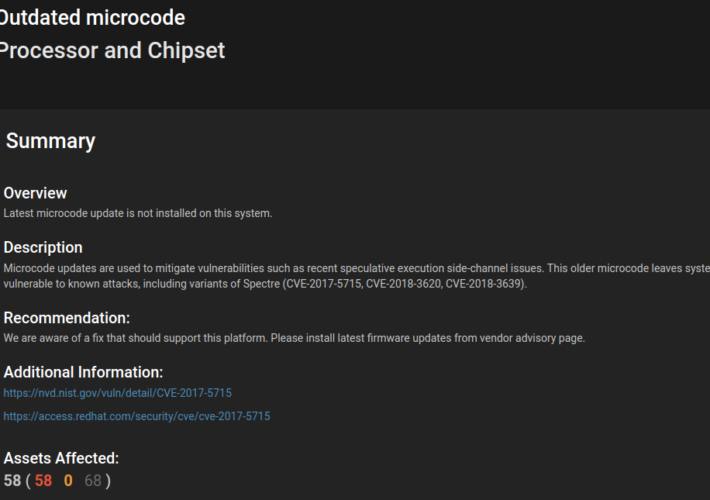
Source: securityboulevard.com - Author: Paul Asadoorian Attacks against low-level CPU architecture popped up on most tech...
Source: securityboulevard.com - Author: Jeffrey Burt California lawmakers later this month are expected to vote on...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Danielle Cook We had so many great questions about Kubernetes in the...
Source: securityboulevard.com - Author: Chris Garland This white paper discusses the increasing threat of ransomware attacks...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Arwen Heredia Fraudulent activity comes in various forms, many of which are...
Source: securityboulevard.com - Author: Jeffrey Burt A relatively unknown threat group that six years ago started...
Source: securityboulevard.com - Author: Aaron Linskens In the ever-evolving world of DevOps, two concepts, Shift Left...
Source: securityboulevard.com - Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original...
Source: securityboulevard.com - Author: Cofense Staying safe online is more important than ever. Cybercriminals are becoming...